Discover the different types of penetration testing and find out which one is best suited for your company’s security needs.
What is penetration testing?
Penetration testing, or pen testing, is a controlled testing process aimed at evaluating the security of a system by discovering and exploiting security weaknesses to gain access to networks, databases, and critical information systems of an organization. Penetration testing is a popular element of an enterprise cybersecurity assurance program.
There are many types of penetration testing depending on the customer’s needs, the scope of the test, the tools and techniques used, the systems assessed, and the amount of information the client wants to share with the pen test provider.
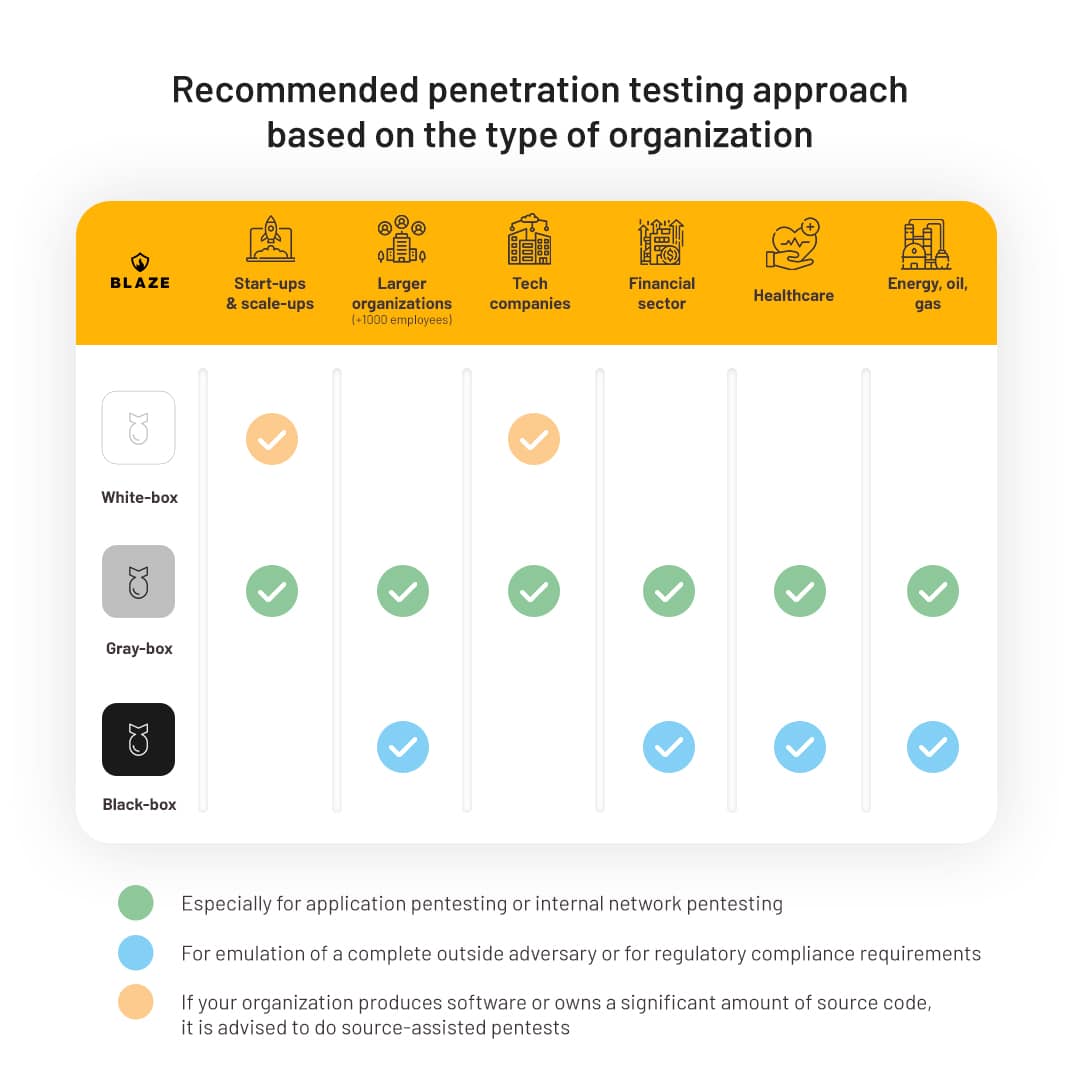
Ideal pentest approach: White-box, black-box, or gray-box?
One of the most common categorizations of penetration tests is based on the volume of information that has to be shared by the company with the penetration testing provider prior to the engagement. Depending on how much information the penetration testers are given, they will perform the assessment from one of the following perspectives:
White-box penetration testing
In white-box penetration testing (also called full-knowledge penetration testing), the security engineers have full access to the target scope, which may include credentials, network diagrams, documentation, and source code. It allows them to thoroughly analyze the system and identify any weak points from a vantage point of a complete insider.
It is typically one of the most time-consuming penetration tests, as it requires sifting through a large volume of information. However, it allows organizations to discover and fix issues that may not be apparent to an average hacker but still might be exploited by a malicious insider.
Black-box penetration testing
Black-box penetration testing, or zero-knowledge pentesting, doesn’t arm the security engineer with any prior knowledge about the systems under the scope. The assessment is performed from the perspective of an attacker who only has publicly available data at their disposal. This type of pentest can be useful for identifying security vulnerabilities and simulating a complete external attacker.
Gray-box penetration testing
Gray-box pentesting, also called insider attack simulation, is a hybrid approach in which the penetration tester has some prior knowledge of the system but not complete access. For instance, in web application pentesting, it is common to provide the testing team with a set of test credentials – this is considered a gray-box approach.
This type of pentest can be useful for identifying both technical and organizational vulnerabilities and is usually more focused than a black-box method. It allows the cybersecurity engineer to thoroughly assess systems that are critical to the organization while still exposing the danger that external hackers may pose. It is also the most common pentesting perspective.
There are benefits to all three types of perspectives. However, most penetration tests take place either from a grey or white-box point of view. In the table below, we demonstrate which penetration testing approach is usually taken based on the type and size of the company.
Should a penetration test be performed manually or automated?
Both manual and automated penetration testing have their own advantages and disadvantages and specific use cases where one is more useful than the other.
Automated penetration testing is, first of all, hardly a penetration test per se, but instead, automated scanning for known issues.
Automated vulnerability scanning is helpful in identifying misconfigurations, vulnerabilities that follow a pattern or have a “signature,” and common attack vectors. On the positive side, automation is cheap and can be used to scan a large number of systems in a short timeframe, finding “low-hanging fruits” security issues that can be valuable, too. It can be especially useful for organizations with limited resources or for initial security assessments of new systems and applications.
Manual penetration testing allows for a more thorough examination of a system or application. If executed by an experienced pentester, it identifies vulnerabilities that may be missed by automated tools. Manual testing also allows pentesters to better illustrate the potential impact a vulnerability or a combined chain of vulnerabilities may have on an organization.
Automation is useful for identifying basic vulnerabilities, but manual penetration testing is often considered superior as it allows for a more thorough assessment that goes beyond what scanners can find.
The ideal penetration testing assessment should combine the strengths of both approaches. It should rely on automation for an initial probe of the attack surface and use seasoned ethical hackers to review the findings of the scanner (which sometimes finds serious vulnerabilities or points to areas for further review) and emulate a real-world attacker by looking for additional security issues that require context and human expertise.
Types of penetration testing
There are several types of penetration testing, including:
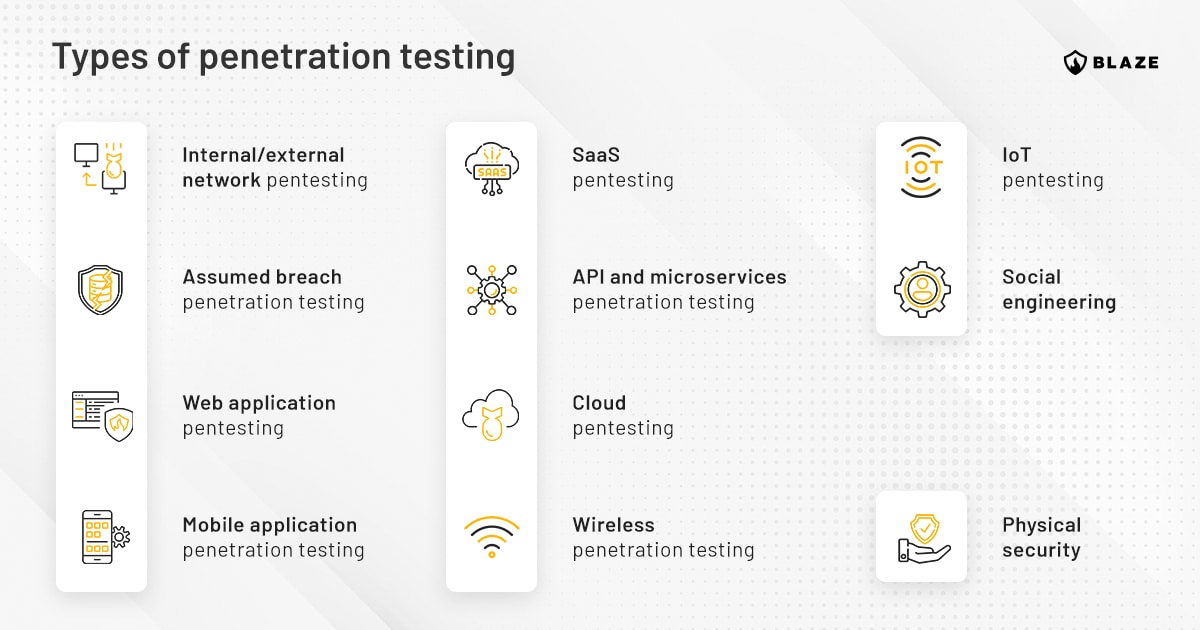
Internal/external infrastructure pentesting
In general, infrastructure/network penetration tests can be divided into two different types:
- Internal penetration testing simulates an attack from within the organization’s network and focuses on testing the security of an organization’s internal systems, such as servers, workstations, file servers, internal applications, and more. Often, it highlights gaps in patch management by finding outdated services and exploiting those that contain known vulnerabilities or are misconfigured, with the intent to achieve the goals outlined in the assessment.
- External penetration tests simulate an attack from outside the organization’s network, and it focuses on testing cybersecurity defenses of Internet-facing assets of the assessment’s scope, such as web servers, VPNs, cloud-based systems, web applications, and APIs.
The main difference between internal and external penetration testing is the level of access that the penetration tester has. In internal penetration testing, cybersecurity engineers need to have some level of access to the internal network (whether via physical access by being on-site patched into the network, via VPN, or via a compromised computer) to simulate the actions of a malicious insider. In contrast, an external pentest doesn’t have the same level of access requirement.
On average, internal pentesting brings in better findings, mainly because the attack surface available to an attacker past the firewall and inside the network perimeter is often richer, and it frequently exposes more servers, platforms, and services than an external perspective.
Assumed breach penetration testing
Assumed breach (or “breach simulation”) penetration testing is usually part of adversary emulation exercises, and it simulates an attacker who has already gained a foothold within an organization’s network. The goal of this type of test is to identify the ways in which an attacker might be able to move laterally within the network, escalate privileges, access sensitive information, and compromise the company’s “crown jewels” once they have already breached an organization’s perimeter defenses.
An assumed breach penetration test can be performed by simulating an intrusion from both external and internal malicious users and can include a variety of tactics, such as:
- Phishing, credential stuffing, and password spraying (frequently used for initial access but often applied in assumed breach assessments)
- Lateral movement and privilege escalation techniques
- Active Directory attacks, in the case of Windows or Azure environment
- Abuse of account permissions and configuration for cloud privilege escalation
- Data exfiltration
- Other attacks against the company’s network infrastructure
This form of testing will help organizations understand how well their incident response teams are prepared and how effectively they are able to detect and respond to a real-world breach scenario.
Looking for a pentest provider? Let us challenge your cyber defenses.
Talk to our experts for a custom quote
Web application penetration testing
Web application penetration testing focuses on assessing the security of web-based systems. This type of assessment often has a minimum baseline checklist, such as OWASP Top 10 2021, and can be enhanced with OWASP Testing Guide and ASVS standards, coupled together with the pentester’s creativity to find business logic issues.
Web application pentesting can help to identify such common vulnerabilities as IDORs, Cross-site scripting attacks (XSS), SQL injection, and more:

Mobile application penetration testing
Penetration tests of mobile apps involve probing the mobile application and the APIs it interacts with to identify vulnerabilities. It also assesses the communication between the app and the server and performs an analysis of the application binary per se, along with its interaction with the mobile device.
A good mobile pentest assessment will also attempt to reverse engineer or decompile the source code of the application in order to gather as much information as possible about the app’s internals, look for hardcoded secrets and key material within it, and use binary instrumentation to attempt to bypass protections, such as jailbreak detection and certificate pinning, should they be in place.
Mobile app pentests are often based on OWASP Top 10 Mobile and, for more thorough checks in SDLC, can also be based on OWASP MASVS.

SaaS penetration testing
Security testing of web-based software focuses on the applications, front-end, and back-end APIs, and a thorough review of external facing assets. In many cases, it is a combination of web application penetration testing, API pentesting, and cloud penetration testing, with a twist of external infrastructure pentesting.
SaaS pentesting became more prominent with the popularity of SOC 2 certification, and it is used to support a company’s SOC 2 compliance objectives.
API and microservices penetration testing
API pentesting is one type that is becoming increasingly popular, as APIs and microservices are now used by many companies in order to allow third-party access to their data and services. API pentesting can help to ensure that REST, GraphQL, web services, and other types of APIs have an adequate level of security against known classes of vulnerabilities.
API pentesting generally follows the same process as other types of penetration tests, such as web application penetration tests. Even tooling is similar, with many pentesters using Burp Suite and OWASP ZAP to achieve their tasks (usually combined with Postman or Swagger), just like it frequently happens in web app pentesting. API pentesting even has a branch of OWASP Top 10 dedicated to it, updated for 2023.

It is important to stress there are some specific considerations that need to be made when testing APIs, such as authentication and authorization mechanisms, and prominent attack vectors, such as mass assignment, access control issues (IDORs and BOLAs), rate limit testing, and more.
Cloud penetration testing
The goal of cloud penetration testing is to identify and exploit security weaknesses in infrastructure and applications, especially SaaS apps, hosted on public cloud providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), to gain unauthorized access to sensitive information. The process typically involves using a variety of tools and techniques to scan for cloud-based assets and identify vulnerabilities and misconfiguration.
When procuring a cloud pentest, it is important to keep in mind that it is not a regular application pentest or a normal external/internal network penetration testing. While frequently, the cloud-hosted apps and infrastructure are also tested for security issues, your penetration test provider must be knowledgeable about the underlying cloud you’re using.
For example, it’s popularly known that an SSRF vulnerability in an AWS-hosted application can have a much larger impact and even lead to the entire compromise of the user’s cloud infrastructure. Additionally, cloud services such as AWS Cognito, Azure AD, S3 buckets, RDS, and more, have their own misconfiguration and issues, meaning it’s important to have an experienced pentester to recognize such services when they’re found and have the ability to leverage them for the assessment.
A cloud penetration test can also be applied to less popular and more niche providers, such as the cloud computing services offered by Oracle OCI, IBM Cloud, Huawei, Alibaba, OVH, and more. Each of them with its own nuances, specific types of security vulnerabilities, and tailored attack vectors.
Wireless penetration testing
When the word “wireless network pentest” is thrown around, in most cases, it refers to Wi-Fi penetration testing and not pentesting of other wireless technologies, such as Bluetooth, BLE, ZigBee, or other protocols that are carried over radio signals (but these can also be assessed for security and require specialized equipment such as a software-defined radio).
The goal of wireless penetration testing is to identify and exploit security weaknesses in Wi-Fi to gain unauthorized access to the company’s network and evaluate whether there’s adequate segregation from the wireless network to the corporate network, enabling pivoting to sensitive servers.
The process typically involves using a variety of tools and techniques to scan for wireless networks, find vulnerabilities, and simulate active attacks (e.g., capturing and cracking WPA2 handshakes) or passive attacks, such as creating rogue access points to obtain wireless credentials.
IoT pentesting
IoT (Internet of Things) penetration testing focuses on testing the security of IoT devices and systems. This can include testing the security of the communication protocols used by IoT devices, as well as the security of the software and firmware on which they operate.
The goal of IoT penetration testing is to discover vulnerabilities and weaknesses in IoT devices and systems and to make recommendations for improving their security.
This can include identifying open ports and their respective misconfigurations, unpatched software, factory “backdoor” accounts, default passwords, extracting firmware for finding security issues, bypassing anti-tamper mechanisms, identifying ways to gain a shell on the device via JTAG/UART/SPI, exploiting vulnerabilities in the embedded web application, or other issues that an attacker could exploit to gain unauthorized access to the device or jailbreak it.
Social engineering testing
Social engineering in cybersecurity is an act of tricking employees into disclosing sensitive information or granting access to a company’s computer systems or infrastructure. Some examples of attacks using social manipulation techniques are phishing (especially BEC – Business Email Compromise) or malvertising.
Social engineering tests can be an important part of penetration testing, especially for initial access in red team operations.
Physical penetration testing
Physical penetration testing simulates an attacker physically accessing a building or location to gain unauthorized access to computer systems or sensitive data. It can include activities such as breaking into a locked facility, bypassing security systems, or “stealing” hardware or data storage devices.
Most organizations that have a physical office, especially containing server rooms, important equipment, or information, can benefit from a physical penetration test.
How to choose the right penetration test type for your needs?
Consider the key factors
- Your business objectives
What are the main drivers for pentesting in your company? Is it part of your security assurance program (driven by engineering), or is it because of an audit, regulatory compliance, or vendor assessment? - Your threat model
It makes more sense, for example, for a tech company to perform a white box penetration test, whereas an IoT company should take into consideration attacks with physical proximity. Some organizations want to emulate an insider threat agent, whereas others have an external adversary in mind.
Other factors relevant to your company, such:
- The size of your organization
- The industry in which the organization operates
- Compliance requirements
- Your risk tolerance
- Budget – if budget and pentest costs are a constraint, try to reduce the scope to business-critical parts but don’t leave out important bits, taking into account your threat model as well
Note: It is sometimes beneficial to combine different penetration testing perspectives. It may happen that a grey-box pentesting need stems from an audit requirement, and a black-box pentest is simultaneously forced by the company’s threat model.
Conclusion
While there are many classifications of approaches to penetration tests, the most common one divides pentests into white-box, black-box, and gray-box.
Other penetration testing types include web and application pentesting, SaaS, cloud pentesting, or wireless network penetration testing.
Some of these tests may overlap in their scope and execution; for example, a web application pen test could also cover social engineering attacks, or an IoT penetration test could include application, web, and physical penetration testing.
Choosing a penetration test type depends on many factors, such as the organization’s business objectives, its size, threat model, or compliance requirements.
It’s important to remember that no single type of penetration testing can provide a complete security solution, which is why it’s recommended to conduct different types of penetration tests at different intervals.
Regularly testing the security of your organization will help you quickly identify and remediate critical vulnerabilities, assess the effectiveness of your security controls, and ultimately improve your overall cyber security posture.
FAQ
What are the three main types of penetration testing?
The most common categorization divides pentests into white box, black box, and gray box, based on how much information is shared with a penetration tester before the engagement.
What is the most common penetration testing type?
Gray box penetration testing is the most commonly performed pentest type, as it is the most versatile and benefits most types of organizations.
What is the best type of penetration test for a start-up?
Start-ups and scale-ups can benefit most from white box penetration testing, as they usually produce and own their source code. Grey box penetration testing is also beneficial.
Which is better: automated or manual pentesting?
Automation is useful for identifying basic vulnerabilities, but manual penetration testing is considered superior as it allows for a more thorough assessment that goes beyond what scanners can find.








