Discover all the essentials of ISO 27001 penetration testing for compliance purposes by reading our buyer’s guide on pen testing. Make smarter choices for your next assessment.
If your organization is interested in a pentest for ISO 27001 compliance, we are offering 15% OFF this month in our penetration testing services package tailored for ISO 27001.
This post will continue to be updated with new requirements for ISO 27001 pentest in 2024, should they come into force.
ISO 27001 compliance involves demonstrating that an organization’s information security management system (ISMS) meets the standard’s requirements. To achieve compliance, an organization must undergo an audit process in which an independent third-party assessor evaluates the organization’s ISMS against the standard.
The assessor will review the organization’s policies, procedures, and controls, as well as its risk assessment and risk remediation processes, to ensure that they are in line with the requirements of the standard. If the auditor determines that the organization’s ISMS meets the requirements outlined by the standard, the organization will be awarded a certificate stating it is compliant with the norm. This certification serves as a formal recognition that the organization has a robust and effective ISMS in place to protect its sensitive information.
According to Afnor, the number of valid ISO 27001 certificates jumped from 36,000 in 2019 to 58,000 in 2021, highlighting the increasing importance of information security controls in businesses worldwide.
In 2022, there was an update of ISO/IEC 27000, the first since 2013, and yet questions about cybersecurity assessments and requirements are still here.
This article will explore all aspects of penetration testing in the context of ISO 27001 compliance to help your organization make clear and informed decisions when hiring pen testing services for your audit.
Who will benefit from this ISO 27001 penetration testing guide?
We crafted this guide with the intention of being an authoritative source of information offering relevant insights into pen testing for ISO 27001 audits to the following groups of individuals who may need to procure penetration testing services:
- Executive personnel in charge of IT security in an organization (CISO, VP of security, CIO)
- Upper management, such as C-level executives (CEO, CTO, COO, CFO, board members)
- Key individuals of an audit team and audit committees
- Auditors and compliance officers
- Cybersecurity professionals, including engineers and analysts (AppSec, SecOps, InfraSec, etc.)
- Engineering managers and product owners who were involved in the organization’s ISO 27001 compliance project
What is ISO 27001 compliance, and why is it important?
ISO/IEC 27001 is perhaps the most recognizable of all existing information security standards. ISO 27001 outlines a framework for an organization’s information security management system (ISMS), providing a set of guidelines and requirements for establishing, implementing, maintaining, and continually improving information security.
The standard is based on a risk management approach, which helps organizations identify, assess, and prioritize the risks to their sensitive information and implement controls to reduce those risks to an acceptable level. ISO 27001 specifies the requirements for an ISMS, including the policies, procedures, and controls an organization should have to protect its sensitive information.
Being ISO 27001 compliant is an important step for a company from a data security and information security policies point of view. A certified organization is in a much better position to not only protect customer data and avoid data breaches but also is able to demonstrate to clients and business partners that they have solid and auditable security processes in place, helping them to gain the confidence of these stakeholders and close deals where risk assessments and compliance play a definitive role.
What is ISO 27001 penetration testing?
ISO 27001 penetration test is a form of assessment that aims to evaluate the security of a system, application, network, cloud, or an entire organization and is frequently used to satisfy certain controls established by the ISO norm.
There are multiple types of penetration testing, and such assessments can be conducted through various approaches, each of which considers a different viewpoint:
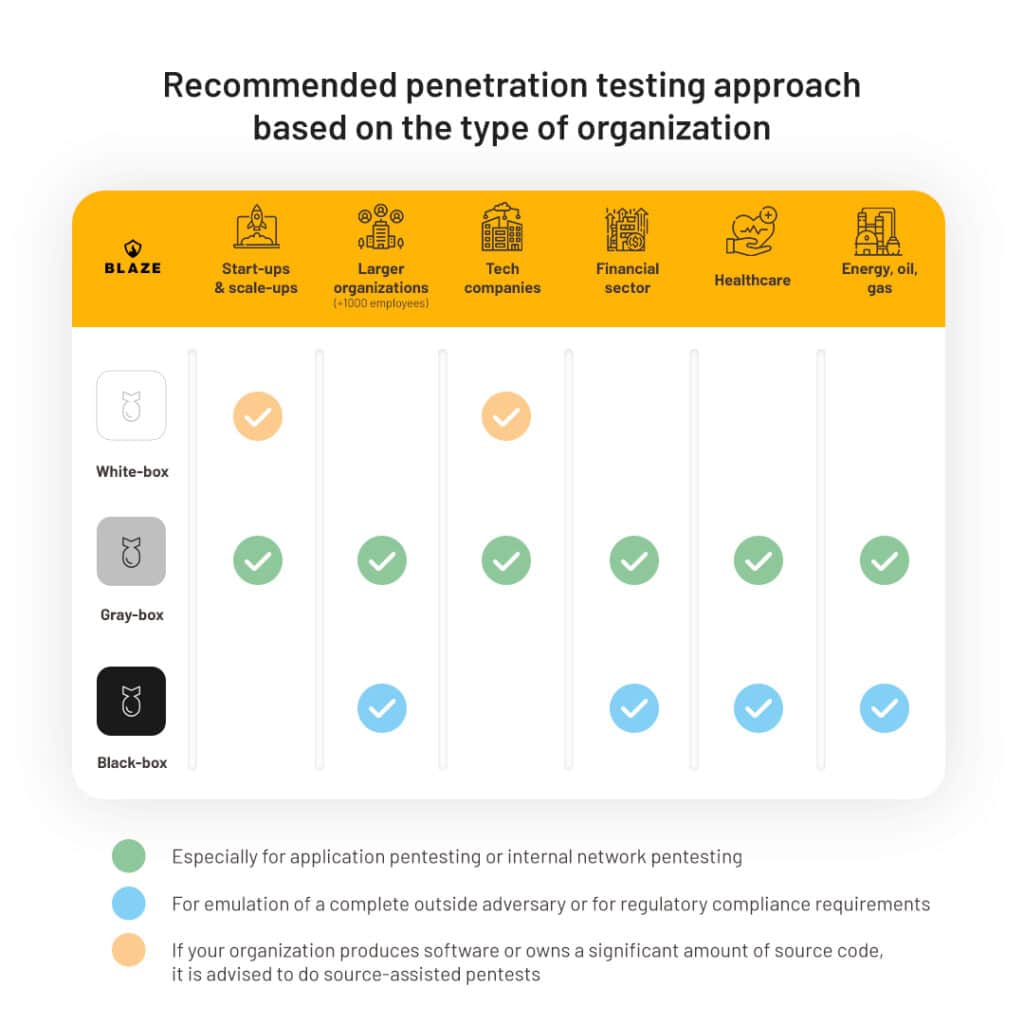
Most professional cybersecurity firms discourage pentests based on a purely black-box approach unless it is the threat model and level of adversary your company wants to emulate. Our experience says that gray-box testing is the preferred method for most ISO 27001 penetration testing engagements.
Penetration tests can be enhanced with automated tools, but skilled and professional pentesters will go beyond automation and conduct manual tests. Although more time-consuming, manual tests often uncover hidden security vulnerabilities that scanning tools miss. Automated tools are useful for routine tasks, such as scanning for open ports or checking for known vulnerabilities, but they cannot replace the expertise of a seasoned ethical hacker trained to identify vulnerabilities and risks.
Is penetration testing a requirement for ISO 27001 in 2023?
Penetration testing is not a mandatory requirement for ISO 27001 compliance, not even with the ISO/IEC 27001:2002 update. However, it is still strongly advised that pen testing be carried out as part of an organization’s continual risk assessment, internal audit, and risk management process.
Annex A of ISO 27001 standard refers to A.12.6.1 Management of technical vulnerabilities and A.14.2.8 System security testing, which state the following:
- A.12.6.1 Management of technical vulnerabilities:
Information about technical vulnerabilities of information systems being used shall be obtained in a timely fashion, the organization’s exposure to such vulnerabilities evaluated and appropriate measures taken to address the associated risk.
- A.14.2.8 System security testing:
Testing of security functionality shall be carried out during development.
It is important to note that ISO 27001:2022 merged A.14.2.8 and A.14.2.9 into a new technological control, namely A.8.29 Security testing in development and acceptance.
A tailored ISO 27001 penetration testing satisfies both A.12.6.1 and A.8.29, providing a way to demonstrate adherence to compliance with technical vulnerability management, as outlined in Annex A.
ISO 27001 penetration testing is used to identify technical security vulnerabilities and demonstrate the impact and likelihood of various attack scenarios. As such, security testing brings an organization an extra layer of assurance that they are correctly implementing information security controls within their environment, as well as providing evidence of compliance when required.
Does ISO 27001 require vulnerability scanning?
ISO 27001 does not specifically require vulnerability scanning as a requirement for compliance. Like penetration testing, this form of automated security assessment is not a hard requirement.
Nevertheless, just like penetration testing, it can be used to augment your audit and satisfy the requirements outlined in A.12.6.1.
What is the average duration of ISO 27001 penetration testing?
The average duration of an ISO 27001 pentest is between 5 and 30 person days, but it depends on the size and the scope of the assessment. Security testing of large and complex scopes can last multiple weeks. This is what we have observed for most pentests with ISO 27001 compliance as the main driver.
We recommend buyers be cautious with penetration testing providers offering “fast and cheap” pentests that only last one, two, or three days. These assessments are usually performed almost entirely using automated scanners, or at best; they follow a standard penetration testing checklist without any “hacker mindset” or creativity. In such cases, there is a high probability that vulnerabilities are missed, and your organization will be left with a false sense of security.
A general guideline is that any penetration test for ISO 27001 performed in less than 40 hours for a small to medium-sized scope (e.g., a web application or a small network) indicates insufficient time to manually examine your systems and thoroughly explore every attack vector.
How to define the scope of an ISO 27001 penetration test?
The scope of a penetration test is established through a collaborative effort between the client’s team (e.g., compliance officer, internal audit, IT) and the external auditor, who will specify the systems, networks, databases, or applications to be assessed and the types of security testing to be carried out.
Based on our experience, organizations undergoing an audit typically consider the following elements for their ISO 27001 penetration testing scope:
- The organization’s flagship product, such as a SaaS platform
- Internet-facing server infrastructure (usually cloud-hosted)
- The organization’s internal network, servers, and key infrastructure, such as Active Directory, Kubernetes clusters, etc.
- APIs (REST, GraphQL, legacy web services) and microservices
- Security testing of mobile apps, if applicable
- Any administrative panel or back office supporting the user-facing SaaS
Frequently, organizations conduct penetration tests in a staging environment to minimize potential disruptions to production systems. As long as the staging environment closely mirrors the production setup, this approach is acceptable and widely adopted. However, before initiating a penetration test, it is recommended to consult your ISO 27001 auditor to ensure they approve of this methodology.
Average pricing of ISO 27001 penetration testing services
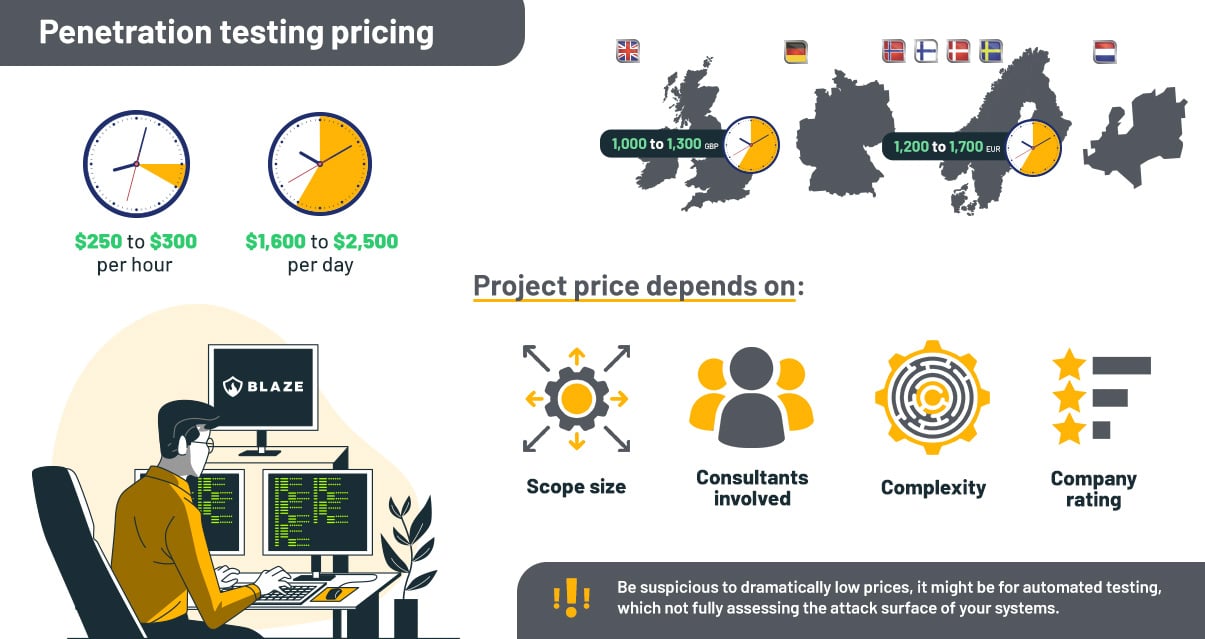
The cost of a penetration test service for ISO 27001, performed by a reputable and accredited cybersecurity firm, typically ranges from $8,000 to $25,000 for a small to medium-sized scope (e.g., a few dozen IP addresses and a handful of web applications/APIs).
Reputable providers offering penetration testing services charge an hourly rate from approximately $250 to $300, or sometimes above, depending on different factors. It is important to remember that the final cost may be higher or lower depending on the size and complexity of the assessment.
Beware of pentest providers that offer significantly lower prices, as they may solely use automated scanners or have unqualified staff, which can result in low-quality assessments that miss high-risk issues and yield false positives.
What are the recommended pentesting methodologies for ISO 27001?
Since ISO 27001 does not establish clear guidelines for penetration testing and the processes that should be employed, it often allows for discretion.
Nonetheless, in our experience, a few widely recognized methodologies are frequently utilized in penetration testing for compliance. One of the most prevalent is the OWASP Top 10, which covers the most common security threats for web, API, mobile, and IoT, making it a suitable choice for many organizations.

Other commonly used methodologies include OSSTMM and PTES, which go beyond application security and encompass network security. Additionally, SANS 25 (less popular) and NIST 800-115 can be applied in compliance testing.
Should I perform penetration testing and vulnerability scanning as part of my ISO 27001 audit?
Even though pen tests and vulnerability assessments are not mandatory to achieve compliance with ISO 27001, there are still several benefits to performing such activities to achieve your industry and regulatory compliance audit goals and improve your cyber defenses:
- Identification of vulnerabilities: Penetration testing is a key activity for organizations to identify security issues in their systems and networks that malicious hackers might exploit.
- Risk reduction and effort prioritization: Pentesting findings highlight security gaps, expose risks and allow organizations to prioritize their efforts in remediating these vulnerabilities and improving their overall security defenses, reducing cyber risks.
- Challenging the effectiveness of security controls: Performing technical security assessments allows organizations to evaluate the effectiveness of their security controls in detecting and preventing attacks. Ultimately, this can help organizations identify gaps in their security measures and spot weaknesses in their defenses.
- Demonstrating compliance: By conducting regular penetration testing and vulnerability scanning, organizations are one step closer to meeting the requirements of the ISO 27001 standard, but also AICPA’s SOC 2 as well as industry compliance such as PCI DSS and HIPAA.
- Protecting against cyber-attacks and data breaches: A professional penetration test can help organizations anticipate real-life adversaries by identifying and addressing vulnerabilities before they are exploited by threat actors, going beyond a checkbox in compliance.
- Increased security awareness: Pen testing can also serve as a practical learning opportunity for organizations, helping to improve security awareness and understanding among employees and management and making a business case for increased investments in cyber defense.
What is the suggested frequency for an ISO 27001 pentest?
Generally, it’s recommended to perform pentests annually, as it’s common for companies to undergo ISO 27001 audits on this basis.
Irrespective of the validity of the certificate and the controls that were audited, in order to keep a continual improvement of the organization’s cyber defenses, it’s advisable to carry out penetration testing regularly.
Closing thoughts
ISO 27001 is certainly a very useful resource for businesses seeking to improve their information security processes, safeguard customer data, and show they have an information security management system with strong controls in place.
While penetration testing and scanning are useful for discovering security vulnerabilities and uncovering associated risks to information systems, they are not required for ISO 27001 compliance purposes. Whether or not to conduct a penetration test or a vulnerability assessment as part of your ISO 27001 audit should be based on your organization’s specific risk profile and security objectives.
Nevertheless, providing an auditor with a thorough penetration test report (containing details about technical vulnerabilities, their respective mitigation, and compensating controls), together with evidence of quarterly vulnerability scans, can certainly inspire confidence in your organization’s cybersecurity practices and security controls.
Here at Blaze, we have partnered with Vanta, Drata and Secfix, some of the world’s leading compliance automation platforms, to provide our customers full support in their ISO 27001 journey.
If your organization is looking for a trusted partner for ISO 27001 audit and penetration testing services or other cybersecurity consulting activities, contact our experts today.
FAQ
What are ISO 27001 penetration testing requirements?
There are no specific requirements for mandatory penetration testing to achieve ISO 27001.
Should I perform a penetration test as part of my ISO 27001 audit despite not being mandatory?
Yes. As part of a strong information security program, it is good practice to conduct penetration testing on a regular basis
How often should I perform an ISO 27001 pentest?
It depends on your organization’s risk profile. For ISO 27001, annual pentests are often recommended.









