Learn about SOC 2 penetration testing requirements and how to improve your company’s security posture against cyber threats. This article will continue to be updated with new requirements for 2024, should they come into force.
If your organization is interested in a pentest for SOC 2 compliance, we are offering 15% OFF this month in our penetration testing services package tailored for SOC 2 audits.
Your organization is going through a long compliance journey, and you’re probably asking yourself: what are SOC 2 penetration testing requirements and the role of vulnerability scanning for an audit?
Achieving SOC 2 is now an essential step for many companies, especially those operating in the SaaS space, to prove to third parties that they have robust procedures to safeguard data and information systems, particularly in the cloud. In many cases, presenting a SOC 2 report can determine whether or not a deal will go through, underscoring its importance to many organizations as it directly impacts revenue and trust.
To ensure compliance with the AICPA’s Trust Services Criteria (formerly known as Trust Services Principles), are vulnerability scanning or penetration testing required for a SOC 2 audit? This is a question that many organizations struggle with, and the answer is sometimes unclear as there is several contradictory information on the Internet about this topic.
In this article, we will explore the requirements for vulnerability scanning and penetration testing in the context of SOC 2 and guide your organization in determining if these assessments are necessary to achieve your SOC 2 compliance objectives.
What is SOC 2 compliance?
SOC 2 is a set of standards that organizations must adhere to ensure that policies and practices are in place to enhance the security of their systems and data. The American Institute of Certified Public Accountants (AICPA) oversees the framework. To become SOC 2 compliant, organizations must have comprehensive policies and procedures to manage cybersecurity risks. They must also undergo regular independent audits to ensure their systems have adequate security measures.
The differences between SOC 2 Type I and Type II
Two types of AICPA SOC 2 attestation reports are SOC 2 Type I and Type II. The difference between them is the following:
- SOC 2 Type I: reports on an organization’s information security controls at a specific time. The idea is to identify the controls and whether they are fit for purpose and in place.
- SOC 2 Type II: reports on an organization’s security controls over a period of time (3-12 months). The main goal is to determine whether the controls work as intended and fulfill the requirements of AICPA’s Trust Services Criteria. They are more comprehensive and valuable for customers assessing an organization’s long-term commitment and strategy regarding cybersecurity.
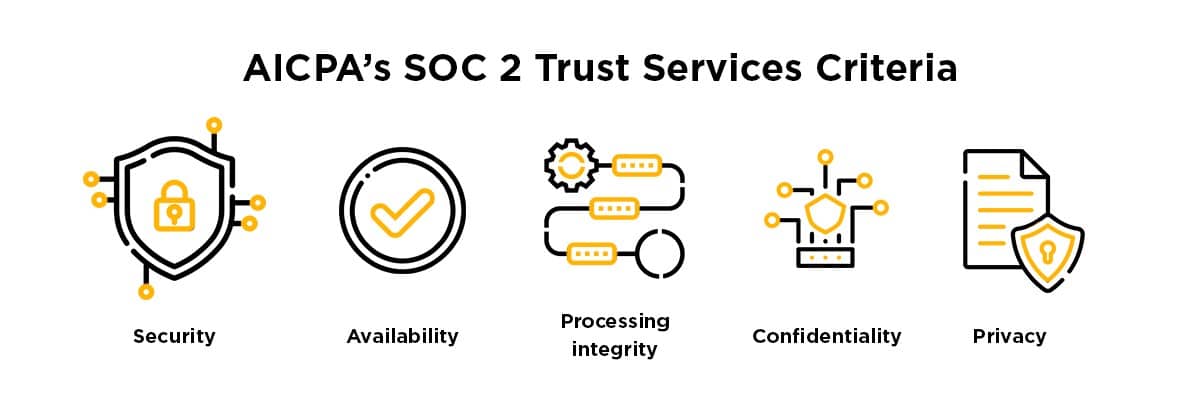
What are AICPA’s SOC 2 Trust Services Criteria?
There are five principles of AICPA’s Trust Services Criteria:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
SOC 2 penetration testing and vulnerability scanning: what are they?
Penetration testing and vulnerability scanning are two critical elements that can be used to assess the security of a computer system and verify the overall security posture of an organization, and put to the test the controls designed to protect against cyber attacks.
Also known by the short form “pentest,” penetration testing involves a simulated attack using the same tools, tactics, techniques, and procedures as an adversary for purposes of ethical security testing. The intention is to identify vulnerabilities and exploit weaknesses to compromise and demonstrate impact on a particular system, a network, or an entire organization.
Demonstration of impact can be displayed in different forms, such as gaining access to confidential assets, such as customer data, or strategic, board-level sensitive information.
On the other hand, vulnerability scanning is an automated process that attempts to identify known vulnerabilities and can serve as an indicator of the company’s security posture.
Penetration testing and vulnerability scanning can help identify security risks, but they have different strengths and weaknesses. Penetration testing is more likely to find unknown vulnerabilities but is more time-consuming and expensive. Vulnerability scanning is less likely to find vulnerabilities that do not follow known patterns, but it is much quicker and cheaper.
Looking for a SOC 2 pentest?
Stay secure and compliant.
Talk to our experts for a quote
Is penetration testing a requirement for SOC 2?
The answer is no. While penetration testing can be valuable for any organization, it is not required to achieve or attain SOC 2 compliance. However, auditors often recommend pentesting assessments to augment the audit and fulfill certain items in Trust Services Criteria (Monitoring activities):
- COSO Principle 16: “The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning.”
- CC4.1’s point of focus – “Management uses a variety of different types of ongoing and separate evaluations, including penetration testing, independent certifications made against established specifications (for example, ISO certifications), and internal audit assessments.”
There is a mention of a pentest for SOC 2 in the criteria, suggesting that it can be one of the methods used to perform the required evaluations. Still, an auditor may say that your organization’s current ISO 27001 certificate is enough to fulfill the requirements, for example.
In our experience, even a customer’s public bug bounty program was once accepted by an auditor as evidence to meet CC4.1. It is all open to interpretation, but there is no doubt that penetration testing is a crucial step to satisfy this requirement, with the added benefit of discovering risks your organization might be exposed to and improving your resilience against cyber attacks.
Does SOC 2 require vulnerability scanning?
The short answer is no; SOC 2 compliance does not require vulnerability scanning, but it is recommended as best practice for any robust cybersecurity program.
Despite not being mandatory, vulnerability scanning can help satisfy the following requirements from the Trusted Services Criteria (System operations):
- CC7.1: “To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities”
- CC7.1 point of focus: “Conducts Vulnerability Scans — The entity conducts vulnerability scans designed to identify potential vulnerabilities or misconfigurations on a periodic basis and after any significant change in the environment and takes action to remediate identified deficiencies on a timely basis”
Vulnerability scanning is an activity that supports the achievement of CC7.1, but it is not required.
Companies should consider incorporating regular vulnerability scans into their security practices because vulnerabilities resulting from not keeping systems up-to-date and lack of timely patching are considered the root cause of 60% of data breaches, according to Automox.
Should my organization perform penetration testing and vulnerability scanning as part of my SOC 2 compliance audit?
It is true penetration testing and vulnerability assessments are not required to achieve SOC 2 compliance. Nevertheless, they can be an essential part of an organization’s cybersecurity efforts to bolster resilience and improve defenses against ransomware, data breaches, and other emerging threats that affect businesses worldwide.
Vulnerability scanning and penetration testing can help you assess the effectiveness of your security controls and identify areas where your IT security needs improvement. Combined, they are an essential part of any comprehensive security program. By regularly conducting such activities, you can ensure that your systems are protected against various cyber threats.
My organization decided to go ahead and perform a pentest as part of our SOC 2 audit. What else do I need to know?
First of all, congratulations! A penetration test is a vital step in ensuring your organization’s security and, indeed, helps you get compliant with SOC 2 standards. Below are the following extra questions you might be asking regarding pentesting for SOC 2 compliance purposes:
The average duration of a SOC 2 pentest
The typical SOC 2 penetration test timeframe ranges from 5 to 25 person days, based on the project’s scope. Cybersecurity assessments for a single website or web application may require just a few days, while large cloud infrastructures or intricate SaaS platforms might require several weeks. Most penetration tests for SaaS companies are completed in one to two weeks, though larger scopes may take longer.
Beware of providers offering “express” penetration tests lasting one to three days, as these assessments likely rely on automated scanners or basic checklists without sufficient attention to detail. Consequently, such tests may miss subtle vulnerabilities, especially in an application’s business logic. In our experience, a penetration test for SOC 2 that takes less than 40 hours to complete for a small to medium-sized scope may not provide the necessary level of scrutiny.
The estimated cost of a SOC 2 penetration test
The average estimated price for a SOC 2 pentest conducted by a credible and accredited cybersecurity firm may vary between $7,000 and $25,000, depending on the scope and complexity. The price may be higher for more comprehensive security audits or lower for smaller scopes. Reputable penetration test providers often charge around $250 to $300 per hour.
Exercise caution when considering providers with significantly lower prices, as they may rely heavily on automated scanners or employ unqualified pentesters for such assessments. While such low-quality pentest reports might appease an auditor, they can create a false sense of security and leave systems vulnerable due to superficial evaluations.
Final remarks
SOC 2 can be a valuable tool for organizations looking to enhance their information security procedures, protect customer data, and demonstrate that strong controls are in place.
Penetration testing and vulnerability scanning are essential for assessing an organization’s systems and data security. However, neither pentests nor vulnerability scans are mandatory for SOC 2 compliance. When used as part of a SOC 2 compliance audit, they can help identify potential risks and vulnerabilities and ensure that appropriate controls are in place to mitigate those risks.
Whether or not to include penetration testing and vulnerability scanning as part of a SOC 2 audit should be based on each organization’s specific risk profile, needs, and security objectives. Providing pentesting reports and evidence of quarterly vulnerability scans will make your audit experience smoother and the auditor confident about your organization’s cybersecurity practices.
Blaze has partnered with Vanta and Drata, two leading automated compliance firms, to provide organizations with full support in their SOC 2 compliance journey. If your company is considering penetration testing or vulnerability scanning as part of your SOC 2 audit process, contact us to discuss your needs.
If you want to learn more about the topic, we recently published the complete buyer’s guide to SOC 2 penetration testing. It contains everything you need to know about pentesting for SOC 2 compliance. Click here to read the full guide.
FAQ
Does SOC 2 require penetration testing?
Penetration testing is not required for SOC 2. However, auditors often recommend pentesting to fully satisfy AICPA’s Trust Service Criteria CC4.1.
Is vulnerability scanning a requirement for SOC 2?
The answer is no, but it can be used to meet the requirement outlined in AICPA’s Trust Service Criteria CC7.1.
Should I perform a pentest as part of my SOC 2 audit?
While a pentest is not mandatory, it can augment the audit and increase the auditor’s confidence in your cybersecurity controls.









