As businesses increasingly depend on web applications for their core operations, securing them against potential threats and vulnerabilities becomes essential. Penetration testing for web applications is thus vital for any organization developing or maintaining web-based services and SaaS applications.
At Blaze Information Security, we conduct hundreds of SaaS and web application penetration testing assessments every year. We often encounter first-time clients with several questions about web application pen testing – particularly regarding preparation for these assessments, the type of information required by the pentesters, the tools employed, approach and methodologies, common security vulnerabilities found in SaaS web apps, timelines, etc.
To address these frequently asked questions, we’ve compiled this educational guide to assist organizations in arranging and preparing for a web app penetration test.
What is web application penetration testing?
Web application penetration testing is a form of assessment designed to evaluate the security of a web app. This process involves simulating cyber attacks against a web application to uncover vulnerabilities malicious actors could exploit. The ultimate objective is to increase the attack resilience of the web application, securing the target system in scope against cyber threats.
This type of security assessment examines various components, such as user input fields, authentication mechanisms, and session management. It also scrutinizes security features such as encryption, input validation and access control measures. Web application penetration testing is applicable regardless of the underlying technologies used in the web app, be it HTML5, JavaScript frameworks, server-side scripts, single-page applications or any other web technologies.
The primary goals and tangible benefits of web app penetration testing include:
- Identifying security weaknesses: This involves discovering vulnerabilities in the web application’s design and implementation. These vulnerabilities could range from simple misconfigurations to complex logical flaws.
- Evaluating security controls: The test assesses the effectiveness of the security measures implemented within the web application. This includes evaluating how well the application can resist attacks and protect sensitive data.
- Ensuring compliance: Web penetration testing helps ensure the application adheres to industry frameworks and regulations, such as GDPR, HIPAA, SOC 2, ISO 27001, and PCI DSS, which are crucial for maintaining trust and compliance requirements.
- Providing actionable recommendations: The pentest results in detailed findings and actionable recommendations, enabling organizations to mitigate and fix all identified vulnerabilities effectively.
- Integrating security into the development lifecycle (SDLC): Web app penetration testing also plays a vital role in integrating security practices into the software development lifecycle.
- Maintaining customer trust and brand integrity: A company’s reputation can be severely damaged in a data breach. Regular penetration testing demonstrates a commitment to security, helping to maintain customer trust and protect the brand’s reputation.
- Cost-effective and proactive risk management: Addressing vulnerabilities post-attack can be costly. Penetration testing proactively identifies and resolves security weaknesses, making it a cost-effective strategy for risk management.
- Enhancing security posture: Through regular testing and continual improvements, organizations can strengthen their overall security posture, making their web applications resilient against evolving threats.
Preparing for a web application penetration test
Preparing for a web app pen testing is a critical phase that ensures the test is comprehensive, relevant to the threat model of the system, and effectively covers the web application’s attack surface. The following are some key steps to prepare for the assessment:
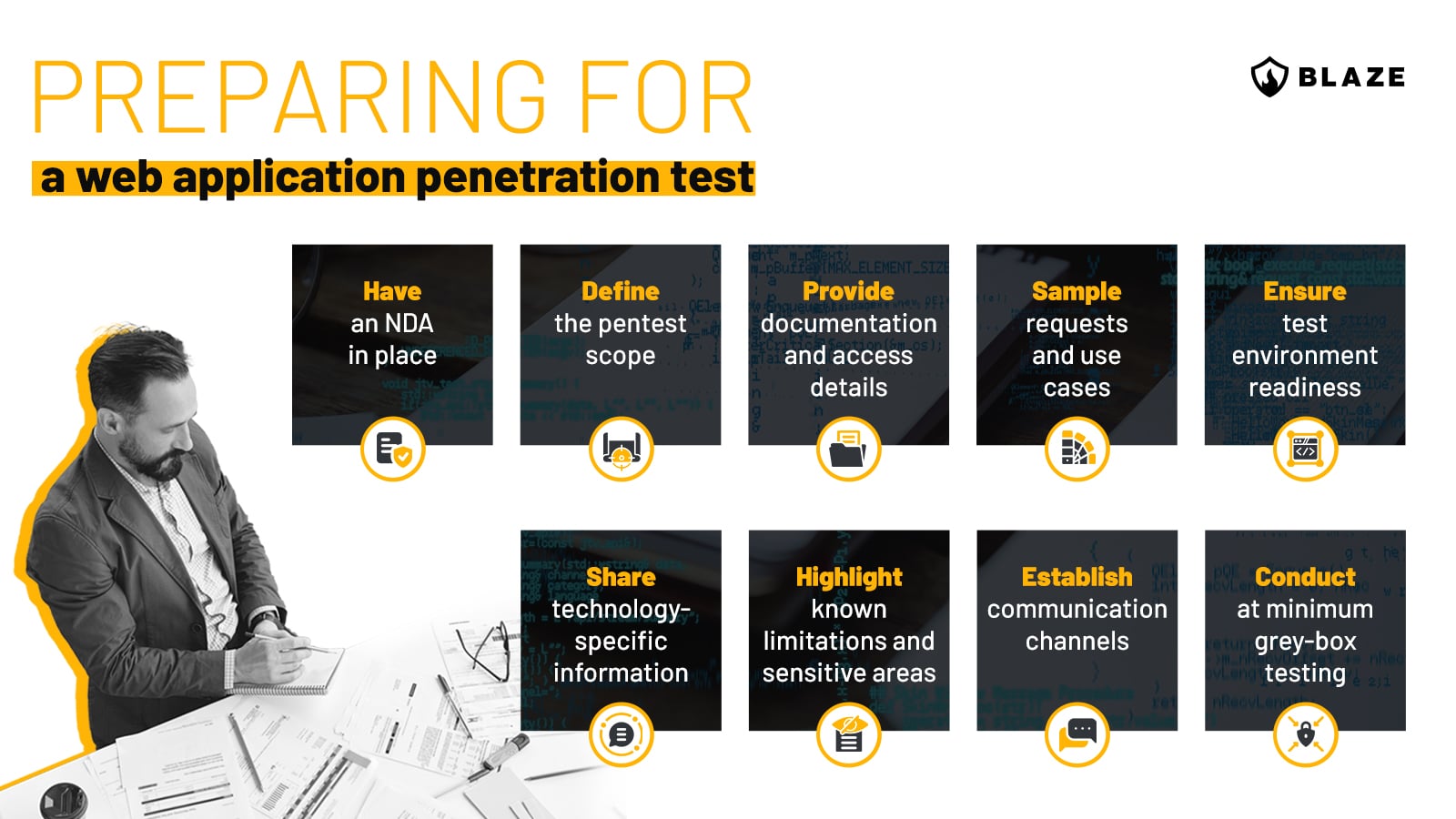
Organizations might opt for a full white-box test for a more in-depth assessment. In this scenario, the penetration testing team is given access to the web application’s source code. This allows for a thorough understanding of the application’s architecture and logic, often uncovering vulnerabilities that are difficult or impossible to detect in grey-box or black-box testing.
Leveraging OWASP methodologies in web app penetration testing
The Open Web Application Security Project (OWASP) heavily influences industry-wide methodologies in web application security. OWASP is a cornerstone in our industry, providing comprehensive, open-source frameworks to guide web app pen testing.
Central to the approach is the OWASP Top 10, a widely recognized document outlining the ten most critical web application exploits and security risks. This list, updated every couple of years based on evolving threats (the last update was in 2021), serves as a roadmap for identifying and prioritizing common vulnerabilities.
Equally important is the OWASP Testing Guide, a detailed manual that offers a complete methodology and checklist for the security testing of web applications. It encompasses various test cases, techniques, and best practices that are invaluable for any application penetration tester. This guide is structured to cover all aspects of a web app, from initial mapping and information gathering to vulnerability exploitation and post-exploitation analysis.
Also valuable is the OWASP Application Security Verification Standard (ASVS), which sets a security controls and requirements framework for development teams. This is particularly useful for aligning security testing with industry best practices and ensuring comprehensive coverage of all security aspects of a web application.
For testing, OWASP Cheat Sheets is a useful reference comprising a series of concise, practical guides for specific topics within security. These cheat sheets are handy for quick references on best practices and recommended security measures.
Integrating these OWASP resources into testing methodologies ensures our assessments are thorough, up-to-date, and aligned with global best practices.
Looking for a pentest provider? Let us challenge your cyber defenses.
Talk to our experts for a custom quote
Common vulnerabilities in web applications
Vulnerabilities can originate from various sources, including improper configuration, software implementation flaws, and design errors. As discussed earlier, OWASP provides a regularly updated list of the most critical risks known as the OWASP Top 10. This list is an essential resource for understanding the threats faced by web applications:
- Broken Access Control: Inadequate enforcement of access controls allows unauthorized users to access sensitive data or functionalities. Attackers might exploit these flaws to access other users’ data, perform unauthorized actions, or access administrative functions.
- Cryptographic Failures: Previously known as “Sensitive Data Exposure.” This vulnerability occurs when sensitive data is inadequately protected, allowing attackers to intercept or access financial details, personal information, or business secrets.
- Injection: Flaws, such as SQL, NoSQL, or command injection, happen when untrusted data is sent to an interpreter as part of a command or query. Attackers can exploit these flaws to execute unauthorized commands or access data.
- Insecure Design: This category focuses on vulnerabilities arising from design flaws, emphasizing the importance of proactive security measures and secure design principles to mitigate potential risks.
- Security Misconfiguration: This happens when security settings are not properly configured or are left to default, potentially exposing sensitive information and system functionalities to unauthorized access.
- Vulnerable and Outdated Components: Using outdated or vulnerable software components can lead to severe security breaches. This vulnerability stresses the importance of updating and patching all components, like libraries and frameworks.
- Identification and Authentication Failures: These refer to weaknesses in the authentication and identity management process. Weak password policies, flawed session management, or improper authentication checks can lead to identity theft or unauthorized access.
- Software and Data Integrity Failures: This new category highlights the risks associated with insecure software updates, CI/CD pipelines, and data integrity issues, where proper verification can lead to system compromise.
- Security Logging and Monitoring Failures: Inadequate logging and ineffective monitoring can prevent or delay the detection of security breaches, allowing attackers to further exploit systems without detection.
- Server-Side Request Forgery (SSRF): SSRF occurs when a server is manipulated to send requests to unintended locations or systems. This can lead to unauthorized access to internal systems, information disclosure, or other malicious activities.

Depending on the context, these vulnerabilities can lead to significant impacts, including data breaches, loss of functionality, reputational damage, and regulatory non-compliance. Understanding these vulnerabilities is the first step towards effectively protecting web applications against them.
An in-depth look at common vulnerabilities
- Injection attacks: At its core, an injection attack happens when an application processes unvalidated user input as part of a command or query. This untrusted input can trick the application into executing unintended actions or accessing unauthorized data. SQL injection is the most notorious form, where hackers manipulate SQL queries to retrieve sensitive information directly from the database or even modify its contents.
- Cross-Site Scripting (XSS): XSS attacks occur when an application includes untrusted data in its output, which is then rendered by a web browser. This can allow an attacker to execute arbitrary JavaScript code in the context of the victim’s browser session. The consequences can range from session theft to delivering malware or even defacing websites.
- Broken Authentication and Session Management: This vulnerability occurs when authentication and session management functions are implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens or to exploit other implementation flaws to gain access to other users’ identities.
Explanation of the potential impact of these vulnerabilities
The potential impact of these vulnerabilities can be severe, causing anything from mild inconvenience to significant disruptions and financial losses.
- SQL injection attacks can lead to unauthorized data access, potentially revealing sensitive information such as usernames and passwords, credit card details, personal addresses, or proprietary business information. In extreme cases, an attacker might gain full control over a system by leveraging functionalities in database servers.
- XSS attacks can compromise user accounts on the victim’s web application, leading to unauthorized actions carried out on their behalf. In more severe cases, an attacker can use XSS to spread malware, perform actions as the user, or even steal identities.
- IDORs, Broken Authentication and Session Management can lead to unauthorized access to user accounts or even system-wide access if administrative accounts are compromised. This can lead to unauthorized data access and manipulation or the execution of privileged commands.
Addressing these vulnerabilities requires a combination of coding practices, regular vulnerability scanning, effective use of security frameworks and libraries, and thorough security testing and code review.
Commonly used web application penetration testing tools
Penetration testing tools play a vital role in the assessment process. Here’s an overview of some tools widely used in web application penetration testing:
- Burp Suite Professional: A comprehensive web application security testing tool offering automated and manual testing capabilities. It includes features like proxying requests, analyzing traffic, and exploiting vulnerabilities. Open-source alternatives can be ZAP and Caido.
- ffuf (Fuzz Faster U Fool): ffuf is a highly efficient web fuzzer written in Go. It’s used for discovering elements and directories on a web server and is particularly effective for brute-forcing directories and filenames in web applications.
- Amass: An advanced tool for subdomain enumeration, useful for discovering external assets associated with a target web application.
- Postman: Commonly used for API development, Postman is also valuable for exploring and testing APIs within web applications, aiding in identifying API-related vulnerabilities.
- Aquatone: A domain flyover tool that collects visual data on web-based assets, giving a quick overview of a web application’s external surface area.
- XSStrike: A specialized tool for detecting and exploiting Cross-Site Scripting (XSS) vulnerabilities in web applications. It uses fuzzing and advanced analysis techniques.
- SQLMap: An open-source penetration testing tool for automating, detecting, and exploiting SQL injection vulnerabilities in web applications.
- Param Miner: A tool for discovering hidden, unlinked parameters in web applications, which can reveal security issues often overlooked. Arjun is also an alternative to Param Miner with similar capabilities.

Each tool brings unique capabilities to the web application penetration testing process, from initial reconnaissance to vulnerability exploitation. They are essential for bug bounty hunters and application security professionals focused on identifying and mitigating web application vulnerabilities.
It’s important to note that while automated tools can augment the penetration testing process by helping to quickly identify common vulnerabilities, they cannot yet replace the nuanced and context-specific analysis provided by manual pentesting. A balanced approach combining automated and manual testing is essential for a thorough and effective web application security assessment.
The right certifications for web application pentesting
There’s no shortage of penetration testing certifications in the market, but only a handful have a strong focus on web application penetration testing. When engaging a penetration test provider or investing in upskilling your internal team with relevant web app pentesting capabilities, make sure to check out the following certifications:
- OffSec Web Expert (OSWE – WEB-300)
- GIAC Web Application Penetration Tester (GWAPT)
- Burp Suite Certified Practitioner (BSCP)
- eLearnSecurity Web application Penetration Tester Extreme (eWPTX)
- OffSec Web Assessor (OSWA – WEB-200)
- Pentester Lab Pro labs

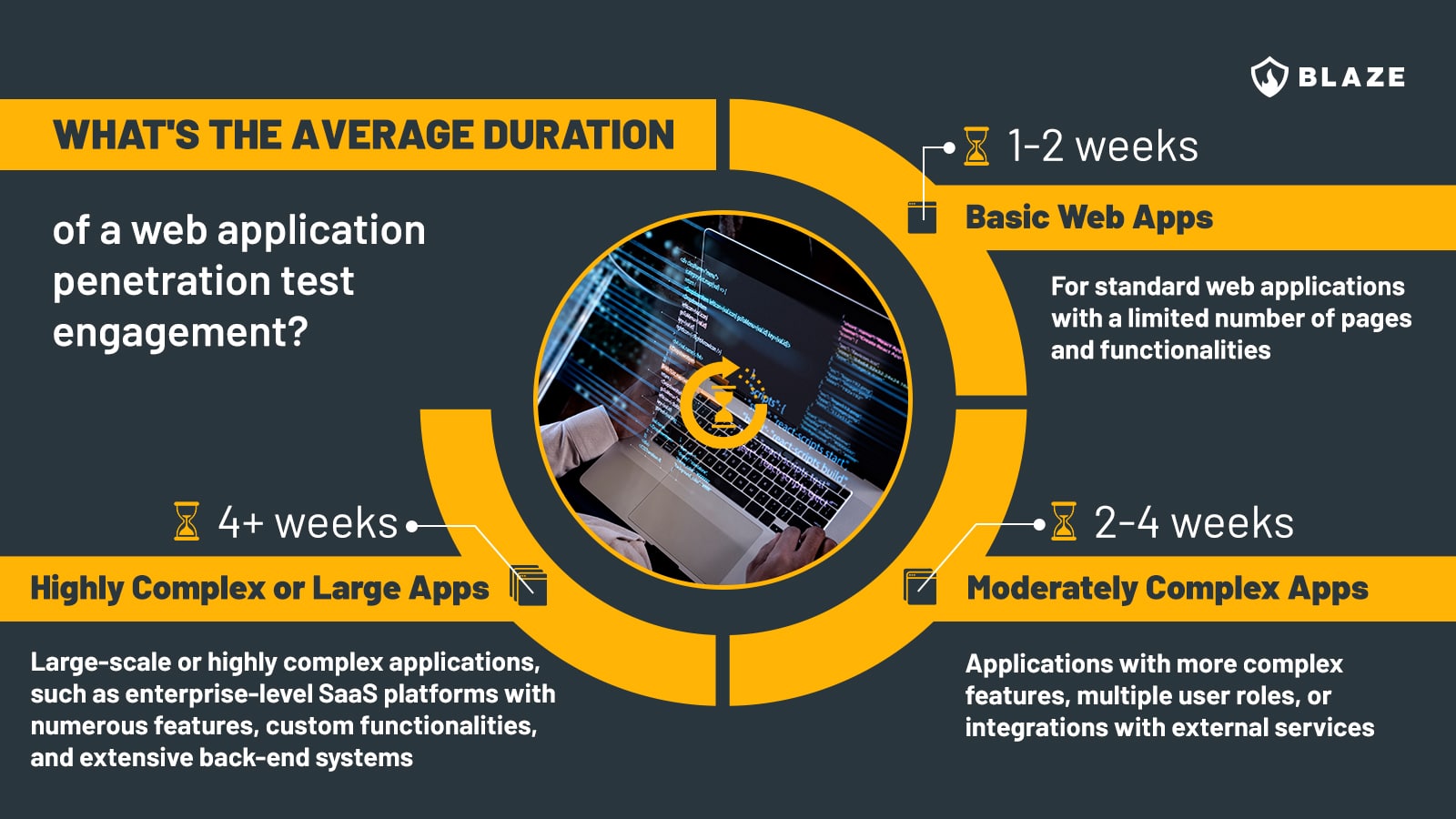
What’s the average duration of a web application penetration test engagement?
While general timeframes can be estimated, the specific duration of a web application or SaaS penetration test greatly depends on the unique characteristics and requirements of the application under scope. Below, we’ll break down the most common timeframes based on our experience.
- Basic web applications (1-2 weeks): For standard web applications with a limited number of pages and functionalities, the testing typically takes between one to two weeks. For example, a simple blog site or a small e-commerce site falls into this category.
- Moderately complex applications (2-4 weeks): Applications with more complex features, multiple user roles, or integrations with external services usually require two to four weeks. An example is a mid-sized SaaS platform with various user permissions and API integrations.
- Highly complex or large applications (4+ weeks): Large-scale or highly complex applications, such as enterprise-level SaaS platforms with numerous features, custom functionalities, and extensive back-end systems, might take four weeks or more.
Factors influencing the duration of a web app pentest assessment:
- Application size: The number of pages, features, API endpoints and user roles directly impacts the time required. More elements mean more ground to cover during testing.
- Complexity: Custom functionalities, sophisticated user interfaces, and complex back-end logic increase testing time.
- Security maturity: Applications with numerous previously identified and patched vulnerabilities may take longer to test, as testers must verify past fixes.
- Integration with third-party services: Numerous integrations (like payment gateways and external APIs) require additional time to assess the security of these interactions.
- Regulatory compliance needs: If the application must adhere to specific security standards and frameworks, such as PCI DSS, SOC 2, ISO 27001, HIPAA, GDPR, etc., additional time may be required to thoroughly assess the application in line with the compliance framework.
- Client collaboration: The speed of client responses to queries and the provision of necessary information can also affect the timeline.
What to expect from a web application pentest assessment
This list outlines a typical web application penetration test process, and it is designed to be accessible and informative for someone new to this type of cybersecurity assessment.
- Initial consultation and scope definition: Before testing begins, expect a brief discussion to define the scope of the test. This will set the expectations and determine the best approach for the application security evaluation.
- Reconnaissance phase: The testers will gather information about your application, such as its technology and structure, to help them plan their testing strategy.
- Automated scanning for vulnerabilities: The team will use specialized tools to scan your web application for known vulnerabilities. This step helps identify potential weak points.
- Manual testing and exploitation: Beyond automated tools, expect manual testing where experts attempt to exploit identified vulnerabilities. This demonstrates how an attacker might breach your application.
- Regular updates and communication: Throughout the process, the testing team will maintain communication with you, providing updates and explaining their findings in understandable terms.
- Comprehensive report: After the test, you will receive a detailed report. This document will list identified vulnerabilities, their severity, and the potential impact on your application.
- Remediation guidance: The report will also include recommendations for fixing the vulnerabilities. These suggestions will be practical and prioritized based on risk.
- Post-pentest debriefing: Often, the testing team will offer a debriefing session to go over the findings, answer your questions, and discuss the next steps for securing your application.
- Fix validation: After you fix the vulnerabilities, you may have the option to retest, ensuring that the remedial actions were effective.
Final remarks
Web application penetration testing is indispensable to ensure the effectiveness of your app’s security controls. It’s essential not only for uncovering current vulnerabilities but also for anticipating future threats and reducing overall security risks.
By regularly conducting comprehensive web app penetration tests, businesses can stay vigilant against evolving cyber threats, safeguard data, reduce the likelihood of security breaches, and maintain customer trust in their digital services.
If your organization seeks expert guidance to enhance your web application security posture, consider hiring a company specializing in penetration testing services and providers with cybersecurity assessments as their primary business offer.
FAQ
How long does a web application penetration test take?
A typical web application penetration test lasts 5 to 15 days, but the duration can vary depending on the application’s complexity and the breadth of its components.
Can web application security testing be automated?
Partially, yes. Automated scanners and tools play a role in web application security. However, they should not be seen as a replacement for manual pentesting.
Should internal applications be pentested?
Yes, internal applications should be subjected to internal penetration testing. This is crucial for uncovering vulnerabilities that could be exploited by insiders or attackers who have breached the network.








