Learn everything about compliance pentest with our buyer’s guide to SOC 2 penetration testing and make better-informed decisions on your next assessment.
Services organizations that handle sensitive data are often subject to stringent compliance requirements, one of which is SOC 2. To achieve and maintain SOC 2 compliance, organizations must undergo a rigorous, sometimes time-consuming, preparation process and a third-party audit of their security procedures.
AICPA’s Trust Services Criteria sections CC 4.1 and CC 7.1 advise organizations to consider technical assessments as part of the process, making pentesting an important component of SOC 2’s security controls.
The idea for creating this guide came up from the realization that many organizations that engaged with us in the past at some point found themselves in a situation where they needed to perform penetration testing as part of their SOC 2 audit but struggled to find informative and accurate guidance.
This guide attempts to answer the most frequently asked questions related to SOC 2 and penetration testing that we collected from these interactions and help buyers make a more informed decision when selecting services and picking a cybersecurity company to support their compliance objectives.
Who will benefit from this SOC 2 penetration testing guide?
This guide is intended for organizations and decision-makers tasked with procuring penetration testing services as part of their SOC 2 compliance and needs to meet the requirements of customers, partners, and auditors regarding cybersecurity standards.
We created this guide to bring relevant information on the topic of penetration testing for SOC 2 audits for leaders in the following audiences:
- Executives responsible for IT security in an organization (CISO, VP of security, CIO)
- Upper-level management, such as C-level executives (CEO, CTO, COO, CFO)
- Senior members of an audit team and audit committees
- Compliance managers
- Cybersecurity engineers and analysts (AppSec, SecOps, InfraSec, etc.)
- Engineering managers and product owners
What is SOC 2 compliance, and why is it important?
SOC 2 compliance refers to standards organizations must meet to ensure appropriate controls for protecting sensitive data. The framework includes five principles:
- Security
- Availability
- Confidentiality
- Privacy
- Processing integrity
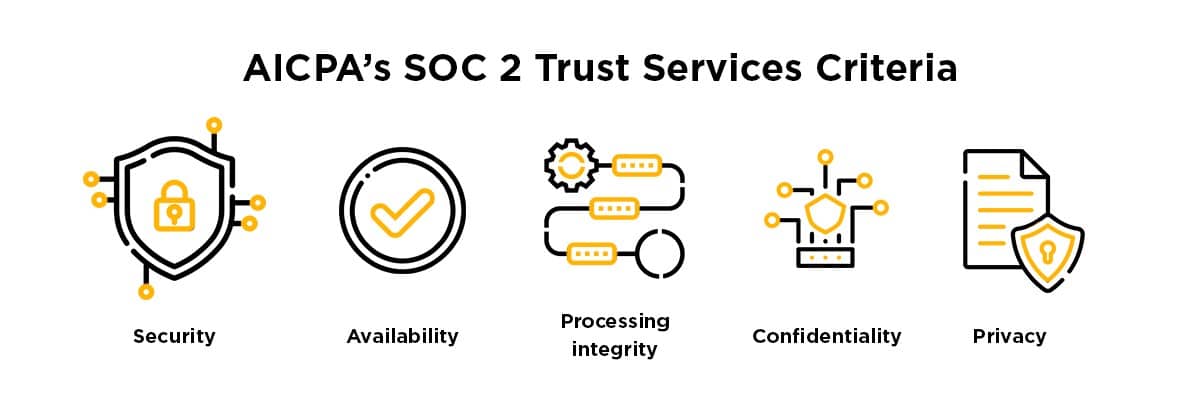
Organizations must implement the appropriate controls to meet these principles to be compliant.
The SOC 2 framework was developed by the American Institute of Certified Public Accountants (AICPA), providing a comprehensive set of guidelines for companies that handle sensitive information. To become SOC 2 compliant, an organization must undergo a rigorous audit process and demonstrate that it has adequate controls to effectively protect customer data and other sensitive information it may handle.
SOC 2 compliance has become increasingly important in recent years as data breaches have continued to rise. Many organizations now require their service providers to be SOC 2 compliant to protect their customers’ data. While achieving compliance can be challenging, it is essential for any company that handles sensitive information, especially for SaaS companies that operate in the cloud.
By meeting the highest standards for security, integrity, privacy, and confidentiality, SOC 2-compliant organizations can give their customers peace of mind knowing that their data is handled securely, backed by numerous procedures and by industry best practices.
What is SOC 2 penetration testing?
A penetration test, often called pentest or ethical hacking, is a type of security testing used to assess the security of a system, application, network, cloud, or an entire company by performing a simulated attack.
A pentest assessment can be conducted using a variety of approaches, each of them taking into account a different point of view:
- Black-box: In black-box testing, the pentester has no prior knowledge of the system or application under test. Security vulnerabilities are identified from the point of view of a complete external attacker.
- Gray-box: This type of testing is a blend of black-box and white-box testing. In gray box testing, the tester has some limited knowledge of the system or application under test. This might include high-level information about the system’s architecture, data flows, and test credentials. No source code access is given.
- White-box: In this approach, the security engineer has complete access to the source code, blueprints, and design of the system under test. This allows the pentester to identify security vulnerabilities that may not be apparent from observing the system’s behavior from an outside perspective.
Most professional pentesting firms will advise against a pure black-box perspective. Sometimes systems are a tough nut to crack from the outside, but with authenticated access, even on a basic permission level, security may be far below optimal. Our experience is that gray-box testing is the preferred approach for most SOC 2 penetration testing engagements.
Penetration tests can be augmented using automated tools, but skilled and professional pentesters will go beyond automation and conduct manual tests. Although more labor-intensive, they often find hidden security vulnerabilities that automated tools would miss. Automation is suitable for routine tasks, such as scanning for open ports or probing for known vulnerabilities. Still, automated pentesting is not yet fit to replace an experienced, ethical hacker who is well-trained in identifying vulnerabilities and risks.
The client typically determines the scope of a penetration test. The customer will usually specify which systems or applications are to be assessed and what types of tests are to be conducted.
We feel it is important to highlight that in the context of SOC 2 compliance, there are no significant differences from pentesting for other purposes or compliance requirements.
Are penetration testing and vulnerability scanning required for SOC 2 compliance?
The answer is simple: penetration testing is not mandatory to achieve SOC 2 compliance. Whether or not to include it in your assessment is a decision that should be made based on your organization’s specific needs, threat profile, and risk appetite.
Nevertheless, the Trust Services Criteria sections CC 4.1 and CC 7.1 of the AICPA advise companies undergoing SOC 2 to consider various types of cybersecurity assessments, such as pentesting and vulnerability scanning:
- COSO Principle 16: “The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning.”
- CC4.1 point of focus – “Management uses a variety of different types of ongoing and separate evaluations, including penetration testing, independent certifications made against established specifications (for example, ISO certifications), and internal audit assessments.”
- CC7.1: “To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities”
- CC7.1 point of focus: “Conducts Vulnerability Scans — The entity conducts vulnerability scans designed to identify potential vulnerabilities or misconfigurations on a periodic basis and after any significant change in the environment and takes action to remediate identified deficiencies on a timely basis”
Several organizations and auditors find that pentests and regular vulnerability scanning can supplement the audit and meet the needs to accomplish compliance with the added benefit of an additional step to increasing their cyber defenses.
If you do decide to include penetration testing in your SOC 2 type I or type II assessment, there are a few things to keep in mind:
- Make sure you work with a reputable and experienced cybersecurity provider.
- Create a scope appropriate for your organization’s size and risk profile.
- Be prepared to promptly address any weaknesses identified during the security testing process.
We have written an extensive blog post about the topic of SOC 2 vulnerability scanning and penetration testing requirements if you are interested in reading more.
Penetration testing vs. vulnerability scanning in the context of SOC 2
Penetration testing and vulnerability scanning are essential tools for managing cybersecurity risk, as they can help identify security weaknesses in systems and networks. However, there are critical differences between the two approaches.
Vulnerability scanning is typically automated, while penetration testing is usually manual. Vulnerability scanners can be run frequently to look for new security weaknesses, while penetration tests are typically only conducted occasionally. Scanners identify potential security issues that follow a repeatable pattern, while pentesting involves exploiting vulnerabilities to gain access to systems or data.
In general, penetration testing is more comprehensive and sophisticated than vulnerability scanning. However, both techniques can help manage cybersecurity risk. Organizations should use a combination of penetration testing and automated scanning to get the best possible picture of their security posture.
It is essential to know that less reputable cybersecurity firms may offer automated vulnerability scanning disguised as penetration testing. You must understand the difference between the two and ensure you get the correct service to help with your compliance goals. A “too good to be true” pricing structure may hint at this practice.
What are the benefits of performing penetration testing for SOC 2 compliance?
Despite not being required for SOC 2, pentests can be helpful for various reasons beyond simply being compliant with a security framework.
A thorough pentest assessment can provide valuable insights into an organization’s cybersecurity posture. A pentest can help identify weaknesses in an organization’s defenses by simulating an attack. As a result, pentests can play an essential role in helping organizations to improve their cybersecurity, comply with regulatory compliance requirements and satisfy vendor risk assessments.
Looking for a SOC 2 pentest?
Stay secure and compliant.
Talk to our experts for a quote
How to define the scope of a SOC 2 penetration test?
The scope of a pentest outlines the boundaries of the engagement, which often entails a list of assets the pentesting team is allowed to attack while excluding assets that are not supposed to be attacked.
Undoubtedly, defining the scope of a penetration test can be a tricky process. After all, the whole point of a pentest is to find vulnerabilities that an attacker could exploit. As such, it’s vital to ensure that the scope of the test is broad enough to identify potential threats but not so broad that it becomes hard to manage or cost-prohibitive.
From our experience, organizations undergoing SOC 2 compliance usually have the following in mind for their pentest scope:
- The company’s flagship product, user-facing SaaS platform
- APIs (REST, GraphQL) and microservices
- Security testing of mobile apps, if applicable
- Any administrative panel or back office behind the user-facing SaaS
- Internet-facing server infrastructure (usually cloud-hosted)
- The company’s internal network, servers, key infrastructure such as Active Directory, Kubernetes clusters, etc.
Organizations frequently perform pentests in a staging environment to avoid any potential disruption to production a pentest might cause. As long as your staging environment is close to production, this is an acceptable and popular approach. Nevertheless, before engaging a pentest, it is advisable to ask your SOC 2 auditor if they feel this approach is acceptable.
What security testing methodologies suit a SOC 2 pentest?
The methodology used will depend on the specific goals of the test. With the added factor that SOC 2 does not define exact guidelines for penetration testing and the procedures that should be used, it is often left open to interpretation.
However, a few standard methodologies are often used in SOC 2 penetration testing. One of the most popular is the OWASP Top 10. This methodology focuses on the most common web, API, mobile, and even IoT security risks, making it a perfect choice for organizations looking to identify and address potential threats. Combining OWASP Top 10 with OWASP Testing Guide should satisfy nearly all pentest requirements for SOC 2 audits.

Other popular methodologies include SANS 25, OSSTMM, and PTES, which go beyond application security but include network security too. Finally, the NIST 800-115 methodology can also be used in compliance pentests. This methodology focuses on identifying and assessing risk, making it a good choice for organizations that want a comprehensive view of their security posture.
How long does a SOC 2 penetration test assessment take?
The duration of an average SOC 2 pentest engagement is between 5 to 25 person days, depending on the scope of the assessment.
A pentest of a single website or web application might take a few days only. In contrast, a comprehensive pentest of an extensive network or a complex SaaS platform could take several weeks. Most pentests, especially for SaaS companies, can be completed within a little over a week or two but can exceed this estimate when a larger scope is defined.
Buyers should be suspicious of providers offering “express” pentests that only last one, two, or three days. These “pentests” are most likely performed almost exclusively using automated scanners, or at best, they blindly follow a basic pentest checklist without any adversarial mindset or creativity. In such situations, there’s a good chance subtle vulnerabilities, especially those pertaining to an application’s business logic, were missed.
A good rule of thumb is that any pentest for SOC 2 performed under 40 hours for a small to medium-sized scope means there was not enough time for a pentester to manually inspect your systems and turn over every stone as it should.
How much does SOC 2 penetration testing cost?
On average, the price of a penetration test assessment for SOC 2 performed by a reputable and accredited cybersecurity firm will fluctuate between $8,000 and $25,000. However, the cost of a SOC 2 penetration test can vary depending on the scope size and complexity.
In some cases, the cost may be even higher if the organization requires a more comprehensive assessment or lower for a small scope. Many reputable pentest providers start at a ballpark figure of $250 to $300 per hour – with niche and specialized work, such as product security assessments or reverse engineering, having a higher hourly price tag (but these are rarely in scope for SOC 2 pentests).
Buyers should be suspicious of providers charging dramatically low prices: most likely, they perform the bulk of the work using automated scanners, which often yield false positives and miss high-risk issues or have unqualified staff to deliver pentest assessments.
While these low-quality pentest reports may sometimes be sufficient to satisfy an auditor, they bring a false sense of security. They can leave your systems vulnerable to attacks, as the assessment probably only scratched the surface.
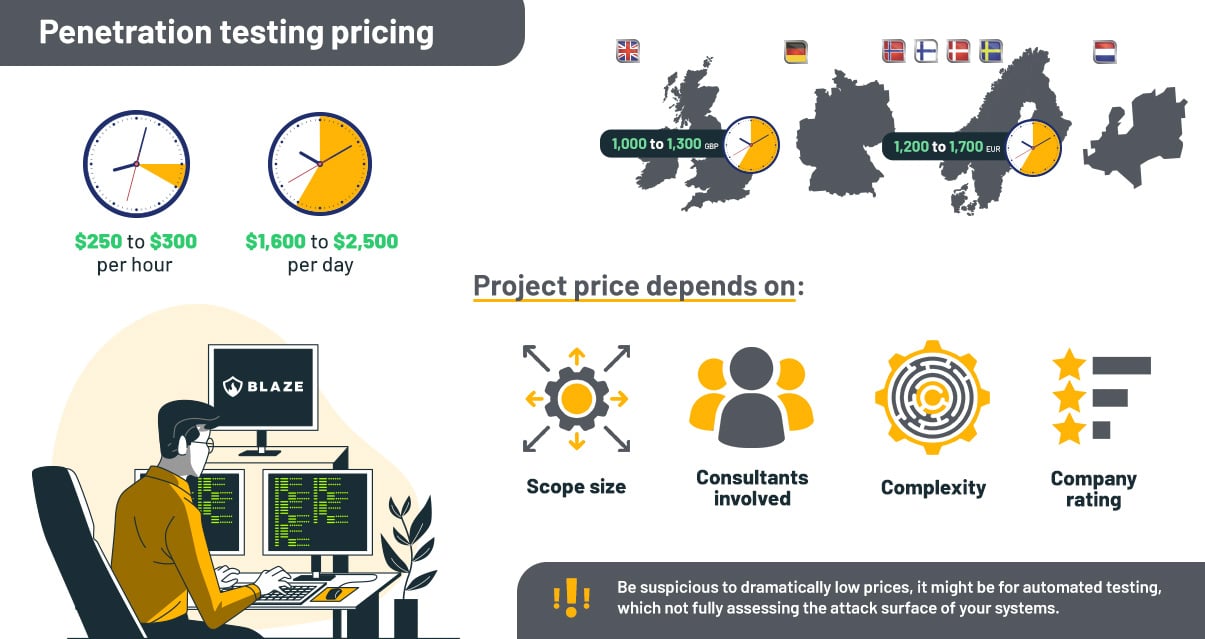
Ultimately, the cost of a penetration test is a small price to pay for the peace of mind that comes with knowing your systems are secure and achieving your SOC 2 compliance goals.
How to select a reputable penetration testing firm?
When it comes to ensuring the security of your organization’s data and systems, there is no substitute for a thorough and adequately scoped pentest executed by experienced experts. But with so many pentesting vendors on the market, how can you be sure you’re choosing a reputable one to fulfill your SOC 2 pentest audit requirements? We have written a detailed post on this topic with the top 10 tips for finding a good pentest provider, but below, you can find a summary.
Here are a few things to look for:
- A reputable pentesting vendor should have a proven track record with experience pentesting similar organizations to yours.
- Working with a provider specializing in cybersecurity services can be beneficial as they often provide superior pentest services.
- Qualified penetration testing firms usually have a technical blog, Github, or other channels displaying their technical expertise and research.
- Ensure the vendor has adequate liability insurance to cover damages if something goes wrong during the pentest.
- The vendor’s staff should be full-time employees rather than freelancers, and they should have robust security procedures protecting your data during the test.
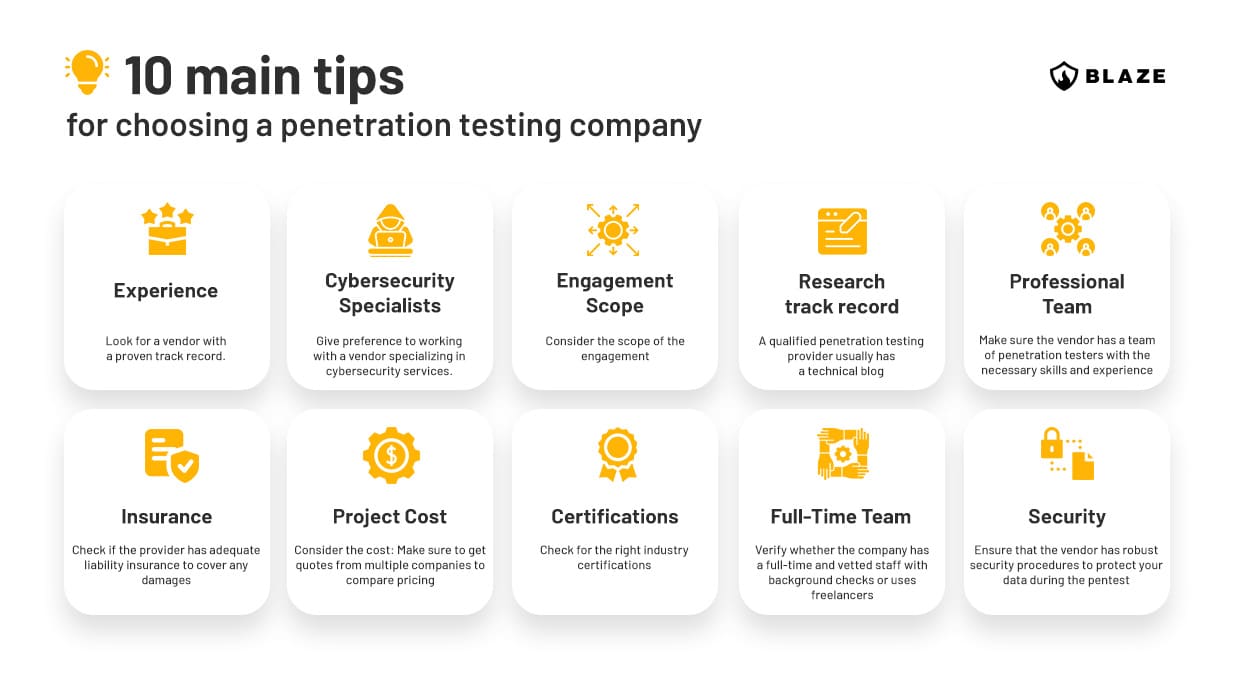
By following the guidelines above, you can be confident that you’re choosing the right penetration testing partner.
How often should I conduct a pentest for SOC 2 compliance?
Most organizations undergo SOC 2 audits annually, meaning the reports are valid for 12 months. If your organization follows this cycle of audit, penetration testing for SOC 2 should be conducted at least once a year to ensure a strong company’s security posture and continuous compliance.

However, there are service organizations that are audited every six months, and it is recommended that your pen test requirements should align with this shorter timeframe.
What to expect from a SOC 2 penetration test report?
A penetration test report is the main deliverable of a pentest assessment. The document usually contains elements such as the following:
- A high-level summary of the findings
- An executive summary explaining the risk and impact of each vulnerability for non-technical audiences
- Scope, testing methodology, and duration of testing
- Detailed information about the vulnerabilities discovered during testing
- Recommendations for fixing each issue or mitigating their respective risk.
A pentest report should provide a comprehensive analysis of the results of the findings encountered during the assessment, with a clear and concise explanation of the impact and likelihood of an attack.
We have written a separate blog post with more information about what to expect from a pentest report, and we encourage readers of this guide to read our article for more details.
How can Blaze help your organization with SOC 2 compliance and penetration testing?
Here at Blaze Information Security, we are experts in offensive cybersecurity. From the senior leadership to the security consulting team, we’re all ethical hackers who believe in technical excellence.
Our service portfolio is composed almost exclusively of penetration testing and application security services. Blaze’s team routinely publishes original research in our Labs, and we constantly deliver penetration testing assessments focused on SOC 2 for many customers across North America, Europe, and beyond. On top of that, we have partnered with leading compliance automation platforms to provide our customers with full support in their SOC 2 journey.
Contact us for your SOC 2 pen test requirements or automated compliance needs.
Final words
By following these guidelines, you can ensure that your SOC 2 audit goes smoothly and that your organization remains compliant with the best-in-class security frameworks.
Penetration testing can help organizations improve their cybersecurity posture and achieve compliance with the latest security standards, including SOC 2.
Contact us today to learn more about how Blaze’s penetration testing services can help your organization achieve your SOC 2 goals and increase cyber resilience.
FAQ
What should be the frequency of a SOC 2 pentest?
Pentesting for SOC 2 should be conducted at least once a year to ensure continuous compliance.
How much does a pentest for SOC 2 cost?
Usually, a reputable firm will charge between $8,000 and $25,000, depending on the scope.
What is the timeframe of a SOC 2 pentest assessment?
Usually between 5 to 25 business days, depending on the scope of work.
Is penetration testing a requirement for SOC 2?
No, it is not a requirement, but it is frequently used to satisfy AICPA’s CC4.1 and CC7.1.









