In an age where data breaches and cyber-attacks are increasingly commonplace, maintaining the integrity and confidentiality of sensitive patient health information is crucial. The Health Insurance Portability and Accountability Act (HIPAA) is the backbone of health information security and privacy in the United States. The HIPAA Security Rule is central among its many provisions, specifically designed to safeguard electronic protected health information (e-PHI).
For compliance officers and cybersecurity personnel, understanding and implementing this rule is crucial to any healthcare organization’s operations and reputation.
What is the HIPAA Security Rule?
The HIPAA Security Rule establishes standards to protect electronic personal health information managed by covered entities. It ensures the confidentiality, integrity, and availability of e-PHI by mandating robust administrative, physical, and technical safeguards. This rule is designed to secure e-PHI against unauthorized access or disclosures, protecting patient health information in the digital healthcare environment.
In 1996, the U.S. Congress passed HIPAA in response to growing concerns about the privacy and security of health information. The advent of digital record-keeping systems, including but not limited to computerized physician order entry (CPOE) systems, electronic health records (EHR) platforms, and an overall growing reliance on technology in healthcare, necessitated this legislation. However, it wasn’t until February 2003 that the Department of Health and Human Services (HHS) published the HIPAA Security Rule as an integral component of this landmark act. To quote HHS, “compliance with the Security Rule was required as of April 20, 2005 (April 20, 2006 for small health plans).”
It’s important to note that in December 2023, HHS announced that updates will come to the HIPAA Security Rule in spring 2024. This article will be updated with the latest requirements as soon as they’re officially released.
Key terms and definitions associated with the Rule
Before delving into the details of the HIPAA Security Rule, it’s important to understand key terms:
- Covered Entities: This term refers to health plans, healthcare clearinghouses, and healthcare providers who transmit health information electronically. These organizations are directly subject to HIPAA rules.
- Business Associates: These are persons or entities who perform certain functions or activities on behalf of or provide certain services to. This covered entity involves the use or disclosure of PHI.
- Electronic Protected Health Information (e-PHI): This is any protected health information that is created, stored, transmitted or received in any electronic format or media.
Main components of the rule: Administrative, Physical, and Technical Safeguards
The HIPAA Security Rule comprises three main components: Administrative Safeguards, Physical Safeguards and Technical Safeguards.
- Administrative Safeguards entail implementing risk management policies and procedures that actively manage and reduce the potential risks to e-PHI. This includes having a designated security official to develop and implement these policies.
- Physical Safeguards involve the physical measures, policies and procedures necessary to protect a covered entity’s electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion.
- Technical Safeguards pertain to the technology, policy, and procedures that protect e-PHI and control access to it. This can include encryption, access controls like usernames and passwords, data transmission security, activity logs and audit controls.
In the upcoming sections, we’ll explore the significance of the rule for healthcare organizations, delve into the specific steps for effective implementation, and discuss best practices for staying compliant.
Who is covered by the Security Rule?
Several healthcare-related organizations are considered covered entities under the Health Insurance Portability and Accountability Act, such as:
Health plans
- Health insurance companies
- Employer-sponsored health plans
- Health maintenance organizations (HMOs)
- Government-funded healthcare programs, such as Medicare, Medicaid, and military and veterans’ health programs
Healthcare clearinghouses
Clearinghouses process health information, transforming nonstandard data into standard formats, or vice versa, for other organizations, ensuring it meets specific content and format standards. They are considered covered entities as they deal with electronic protected health information.
Providers
Providers who submit HIPAA transactions electronically, such as claims, are considered covered entities. These include, but are not limited to:
- Doctors
- Dentists
- Chiropractors
- Nursing homes
- Clinics
- Psychologists
- Pharmacies
The Centers for Medicare & Medicaid Services released the Covered Entity Decision Tool to help organizations understand whether they are considered covered entities.
The importance of the HIPAA Security Rule for healthcare organizations
The HIPAA Security Rule is one of the first lines of defense in protecting patient data. It ensures that only authorized individuals can access e-PHI, reducing the risk of breaches that could jeopardize patient data. Implementing these standards is a necessary step in improving the security of health records.
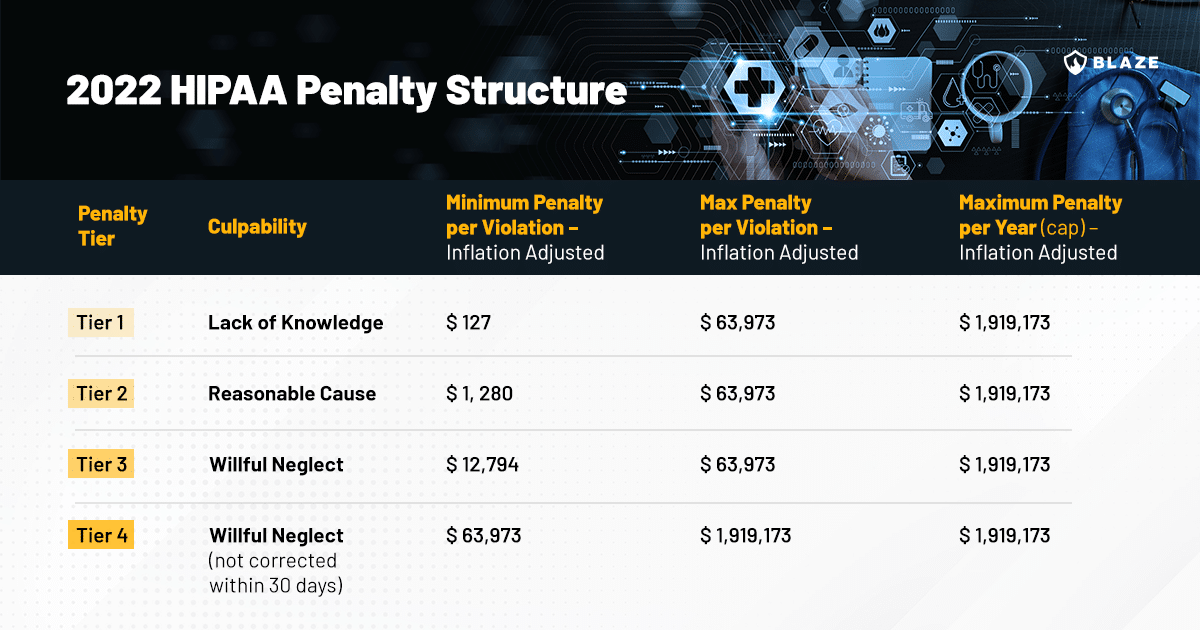
Consequences of non-compliance for a covered entity
Non-compliance with the HIPAA Security Rule can have severe repercussions, including financial penalties, criminal charges, and significant damage to an organization’s reputation.
Monetary fines can range from $100 to $50,000 per violation, with a maximum penalty of $1.5 million per year for violations of an identical provision. Moreover, a data breach resulting from non-compliance can lead to a loss of patient trust, which can be devastating for a healthcare organization.
Several case studies highlight the importance of complying with the HIPAA Security Rule. For example, early in 2023, Banner Health agreed to pay $1.25 million for failing to comply with the HIPAA Security Rule. Specific violations discovered by OCR included:
- Lack of an analysis to determine risks and vulnerabilities to electronic protected health information across the organization
- Insufficient monitoring of health information systems’ activity to protect against a cyberattack
- Failure to implement an authentication process to safeguard its e-PHI
- Failure to have security measures in place to protect e-PHI from unauthorized access when it was being transmitted electronically.

Steps to implement the HIPAA Security Rule
Risk analysis
- First step in HIPAA Security Rule implementation.
- Identify and analyze potential e-PHI risks.
- Determine mitigation strategies.
- Conduct risk assessments and document security measures.
Developing security measures
- Post-risk analysis step.
- Create and implement measures against identified risks.
- Tailor measures to fit the organization’s size, complexity, and technical infrastructure.
Staff training
- Crucial for HIPAA Security Rule compliance.
- Educate all members about the rule and their compliance roles.
- Ensure training is comprehensive and ongoing.
Penetration testing and vulnerability assessments
Although not mandatory, they help achieve compliance with many aspects of HIPAA, especially the items outlined in Technical Safeguards.
- Involves authorized simulated cyber-attacks to evaluate security.
- Exposes vulnerabilities, misconfigurations, and weaknesses.
- Assesses susceptibility to various cyber threats and e-PHI exposure.
- Validates security of patches and updates.
Best practices for staying compliant with the HIPAA Security Rule
Adopting a culture of compliance within the organization
Compliance with the HIPAA Security Rule should not be considered a one-off project but rather an ongoing process that requires active participation from all organization members. This is where the idea of a “culture of compliance” comes into play. It involves cultivating an environment where policies and procedures are followed and embedded in the organization’s DNA. Regular training sessions, open communication about changes in regulations or technology, and a proactive approach to data security can help foster this culture.
Regular audits and reviews to ensure continued compliance
Regular audits and reviews are necessary to maintain compliance with the HIPAA Security Rule. These should aim to verify that all security measures are functioning as intended and identify any areas that need improvement. The results of these audits should be used to update and improve the organization’s security measures.
The role of continual training and security awareness programs
Keeping staff informed and up-to-date about HIPAA requirements and potential security risks is paramount. Regular training sessions should be held to refresh their understanding of the HIPAA Security Rule and to inform them about the latest threats and defense mechanisms. In addition, awareness programs can help instill a sense of shared responsibility, where every individual understands their role in keeping e-PHI secure.
Video: How the Security Rule can help HIPAA-regulated entities defend against cyber-attacks
In October 2023, HHS released a 43-minute video on YouTube that discusses real-world incidents and trends in cyberattacks, compiled from OCR breach reports. The video explores how the Security Rule, when properly implemented, can help decrease the chances of such attacks.
Conclusion
The HIPAA Security Rule operationalizes the protection of sensitive patient data, particularly e-PHI, in healthcare organizations. Amid increasing cyber threats, effectively implementing this rule is crucial.
This rule mandates the implementation of administrative, physical, and technical safeguards to protect individually identifiable health information. Essential actions include risk analysis, staff training, and regular security audits. Cultivating a compliance culture and integrating advanced cybersecurity tools enhances defense against breaches.
Collaborating with cybersecurity experts can offer additional protection and guidance, helping organizations implement technical security measures to better navigate the HIPAA Security Rule and maintain compliance.
In the age of rampant cyberattacks against healthcare organizations, safeguarding patient data is a collective responsibility.








