How should organizations prepare for NIS 2 directive, the new European cybersecurity requirement?
What is NIS 2?
NIS 2 (Network and Information Systems Directive 2) is a directive on measures for a high common level of cybersecurity across the EU aimed at all public and private entities that are critical to the economy or society. It officially entered into force on 16 January 2023.
NIS 2 expands the scope of the original NIS Directive to include more sectors while giving member states some flexibility to add more entities that are considered critical to the economy and society.
Unlike its predecessor (the original NIS directive), NIS2, for the first time, tackles the security of supply chains. It also includes more specific provisions for incident reporting and for the designation of competent national authorities.
NIS2 directive – which handles only the cyber dimension – is accompanied by Critical Entities Resilience (CER) directive that affects the physical security of critical entities.

What is the subject matter of NIS 2
NIS 2 directive proposes measures to improve cybersecurity across the whole European Union by:
- Putting an obligation on member states to adopt cybersecurity strategies and to establish competent authorities, cyber crisis management authorities, single points of contact and Computer Security Incident Response Teams (CSIRTs)
- Introducing cybersecurity risk-management measures and reporting obligations for essential and important entities as well as for entities identified as critical entities under Directive (EU) 2022/2557
- Imposing rules and obligations on cybersecurity information sharing
- Imposing supervisory and enforcement obligations on member states.
Who is in scope of NIS 2 directive
While NIS1 affected such critical sectors as healthcare, energy, transport, digital infrastructure, or financial market infrastructures, NIS2 includes more entities, such as the food sector (production, processing and distribution), social networking services platforms, cloud computing services and data centers.
Importantly, the new legislation introduces a clear size cap that excludes most small and micro companies from its scope. Mostly medium-sized (having more than 50 employees and with an annual turnover exceeding EUR 10 million) and large enterprises will be affected.
However, certain organizations will fall under NIS2 regardless of their size, such as entities providing domain name registration services, trust services providers, DNS service providers, or entities whose services, if disrupted, could have a significant impact on public safety.
Essential and important entities

NIS 2 – main objectives
- Increasing the cyber resilience level of businesses and entities that are critical to the economy and society across the EU
- Reducing inconsistencies in resilience among the member states by aligning the scope of the directive, incident handling requirements, specifying the rules for national supervision and enforcement and capabilities of member states authorities
- Improving the ability of EU member states to prepare for and respond to cyber threats by improving trust between competent authorities, sharing more information, and creating procedures for the event of a large-scale incident or crisis.
Differences between NIS1 and NIS2 directive
Broader scope. NIS2 introduces at the same time a broader and more specific scope. The entities that will fall under the new law, as well as organizations exempt from it, are more clearly defined than in NIS1.
OESs and DSPs are gone. The NIS1 operators of essential services and digital services providers are replaced by more specific categorizations – highly critical and other critical entities.
It reduces the power of EU member states to impose their own regulations/change the scope etc.
More specific reporting rules. Reporting obligations, contents of the reports, and reporting timelines are more clearly defined.
Supply chain security. NIS2, for the first time, addresses the ICT supply chain security.
Cybersecurity risk-management measures
Article 21 of NIS2 requires member states to ensure that essential and important entities take appropriate measures to manage cybersecurity risks and prevent or minimize the impact of incidents on their services and recipients of those services. These measures should be based on an all-hazards approach and include policies on:
- risk analysis and information systems security;
- incident handling;
- business continuity, such as backup management and disaster recovery, and crisis management;
- supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers;
- security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure;
- assessment of the effectiveness of cybersecurity risk-management measures;
- basic cyber hygiene practices and cybersecurity training;
- the use of encryption;
- human resources security, access control and asset management;
- the use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications
While deciding which of the above cybersecurity measures are appropriate, entities should consider the vulnerabilities and security practices (including secure development) of their direct suppliers and service providers. Entities are also required to take into account the results of the coordinated security risk analysis of critical supply chains.
By October 2024 The Commission will adopt implementing acts laying down technical and methodological requirements for certain service providers (such as DNS service providers, cloud computing service providers, data center service providers, content delivery network providers, managed security service providers, providers of online market places, of online search engines and of social networking services platforms) and sector-specific requirements for other essential and important entities.
Obligations and responsibilities of management
The new law places a particular responsibility on the management bodies of essential services to approve and oversee the implementation of cybersecurity risk management measures, and it holds them liable for failing to do so.
Additionally, members of the management bodies of essential and important entities will be required to undergo cybersecurity training themselves, as well as encourage their organizations to offer their employees similar regular training on risk-management practices.
Reporting obligations
NIS 2 directive obliges companies and relevant authorities to report all significant cyber incidents.
An incident will be considered significant when “it has caused or is capable of causing severe operational disruption of the services or financial loss for the entity concerned” or
“it has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage.”
The reporting requirements for entities
The directive proposes a two-stage approach to incident reporting. Companies have 24 hours from when they first discover the threat to submit an initial report and a month from that to present a final, more detailed report.
Entities must report significant cybersecurity incidents to their CSIRTs or other relevant authorities without undue delay and within 24 hours of becoming aware of the threat.
Entities’ obligations to CSIRTS/reporting timeline
- Within 24 hours of becoming aware of the significant incident, the entities will submit an early warning indicating if the threat was caused by criminal or malicious acts or could affect other member states.
- Within 72 hours of discovering the significant incident, the entities will provide an incident notification, updated with information on the severity, impact, and, where available, the indicators of compromise.
- After that, CSIRT or the competent authority may request an intermediate report on relevant status updates.
- Not later than one month after the submission of the incident notification, entities must submit a final report including:
- a detailed description of the incident, including its severity and impact
- the type of threat or root cause that is likely to have triggered the incident
- applied and ongoing mitigation measures
- where applicable, the cross-border impact of the incident
If after one month the incident continues, then entities must submit a progress report and a final report within one month after handling the incident.
Entities’ Obligations towards recipients of their services
Entities have to notify the recipients of their services about the significant incidents that are likely to disrupt the provisions of the services.
NIS2 recognizes that the right to an effective remedy extends to the recipients of services provided by essential and important entities.
Therefore, the entities are obliged to notify their recipients of any measures or remedies they may take in response to the threat.
The European vulnerability database
As one of the goals of NIS2 is to improve information sharing between the member states, The European Union Agency for Cybersecurity (ENISA) will be tasked with developing a vulnerability database where all entities, even those not in the scope of the directive, will be able to voluntarily disclose and register publicly known vulnerabilities in ICT products or services.
All stakeholders will be able to access the information about the vulnerabilities contained in the database. That database will include:
- vulnerability description
- the affected ICT products or services and the severity of the vulnerability and how it may be exploited
- information on available patches and risk mitigation guidance provided by the competent authorities or the CSIRTs addressed to users of vulnerable ICT products and services.
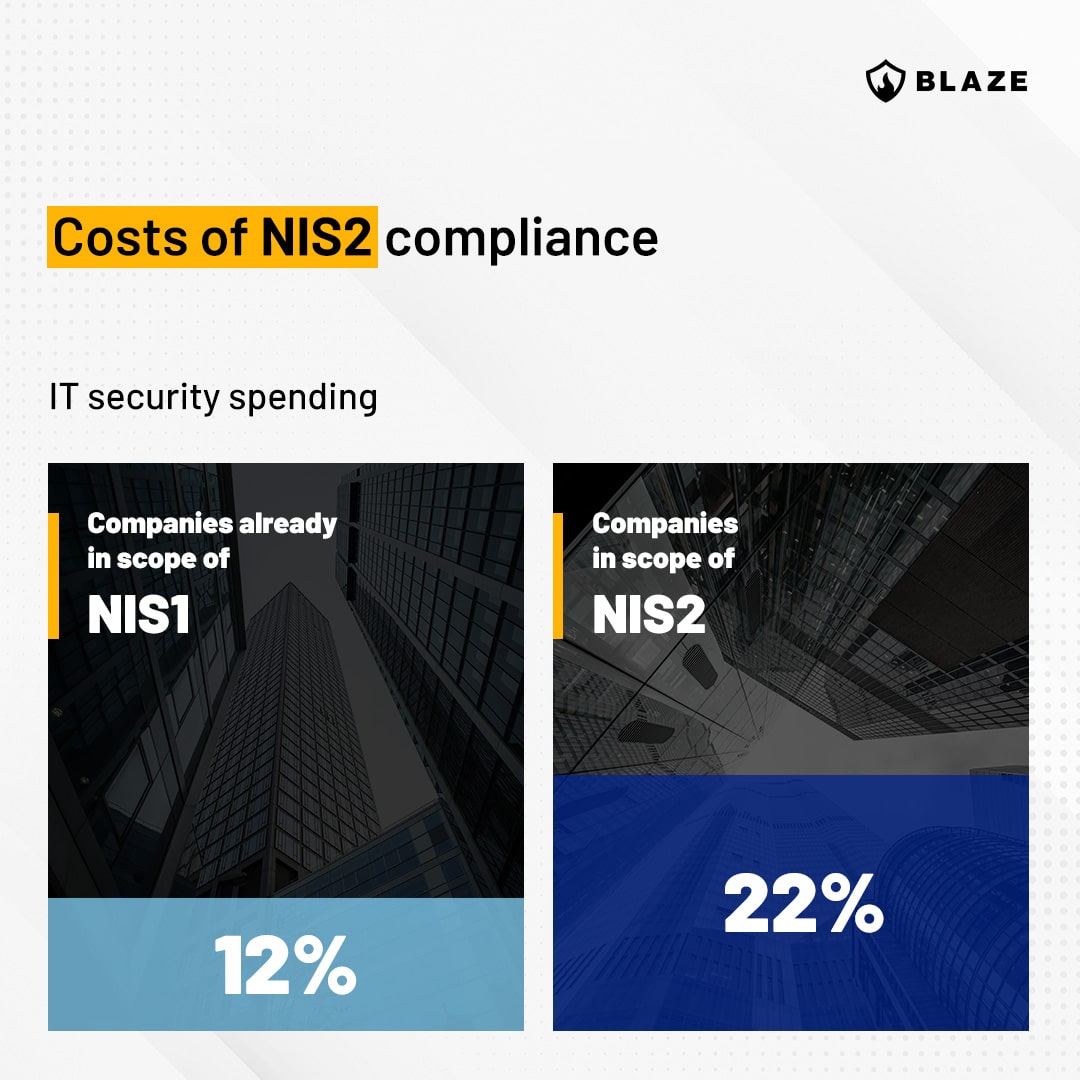
What will be the costs for the affected organizations?
According to the impact assessment accompanying the directive, the companies falling under the scope of the NIS2 framework would need an increase of up to 22% of their current IT security spending for the first years following the introduction of the new NIS framework. Whereas for companies already under the scope of NIS 1 it would be 12%.
However, it is expected that a significant reduction in costs of cybersecurity incidents will offset the new security spending. Additionally, ENISA’s 2020 NIS investments report showed that European operators of essential services and digital service providers spent 41% less on cybersecurity than their US counterparts, exposing a security spending gap between the EU and the US.
Consequences of non-compliance
NIS 2 directive predicts fines for failing to implement its provisions. Essential and important entities that don’t implement cybersecurity risk-management measures or neglect reporting obligations face fines of up to 10 million euros (or 2% of their annual turnover, whichever is higher) for essential entities and 7 million euros for important entities.
Members of management bodies of essential entities can also be held responsible for failures to implement risk management measures.
How to select a cybersecurity provider to assist you in NIS 2 implementation?
NIS 2 directive emphasizes the special role that managed security service providers play in helping organizations fulfill their obligations to manage cyber incidents.
Third-parties hired to assist in incident response, security audits or penetration testing should be selected with increased caution, as they can also be targeted by cyberattacks.
It is particularly important to select managed security providers who are reputable and have the necessary certifications and experience in assisting critical entities.
Conclusion
The new legislation is an attempt by the EU to catch up with the fast-evolving threat landscape and to prepare critical organizations and infrastructure for future threats.
By improving the cyber resilience of critical entities, addressing issues related to underreporting cyber threats and incidents by companies, and enhancing cooperation and sharing practices between EU member states, NIS 2 directive will raise cyber resilience levels across the whole EU.
Successful implementation of NIS 2, combined with the Digital Operational Resilience Act (DORA), Cyber Resilience Act, and CER Directive, will bring benefits to the economy and society and improve the national security of European Union member states.
FAQ
Who is affected by NIS 2 directive?
NIS2 directive is aimed at all public and private entities operating in the EU that are critical to the economy and society.
Which sectors are within the scope of NIS 2?
Sectors such as healthcare, energy, transport, digital infrastructure, financial market infrastructures, the food sector (production, processing and distribution), social networking services platforms, cloud computing services, data centers, and more will fall under NIS 2 directive.
When will NIS 2 enter into force?
NIS 2 entered into force on 16 January 2023. The individual member states will have until 17 October 2024 to transcribe it into national laws.








