What is the European Cyber Resilience Act?
The European Cyber Resilience Act is the proposed new law by the European Commission aimed at products with digital elements. It is part of a larger cybersecurity framework that already includes such regulations as the EU Cybersecurity Act, NIS Directive, and in particular NIS2 Directive, which it will complement.
The main goal of the Cyber Resilience Act is to protect consumers and businesses from inadequate cybersecurity features of hardware and software products with digital elements. Most crucially, the act places the responsibility for the cybersecurity of digital products on economic operators (mostly on manufacturers but in some cases also on importers and distributors) during the whole lifecycle of a product.
Meeting the new act’s cybersecurity requirements will also be obligatory for obtaining the CE mark. The CE marking will be the only marking guaranteeing conformity with the Cyber Resilience Act.
The draft of the Cyber Resilience Act, created after extensive consultations with users, manufacturers, and other stakeholders, was published on 15 September 2022. It is now awaiting approval by the European Parliament and Council. After that, manufacturers of hardware and software products will have 24 months to conform to the new regulation and 12 months to start reporting on actively exploited vulnerabilities.
What are the main objectives of the Cyber Resilience Act?
The new law was developed to tackle the two main issues of digital products in the European market, which are:
- Insufficient cybersecurity measures and widespread vulnerabilities
- Users need more knowledge and access to information about the cybersecurity features of products.
The four main objectives of the Cyber Resilience Act are:
- to ensure the manufacturers design and develop secure products and maintain their security throughout the whole life cycle;
- to introduce a coherent cybersecurity framework;
- to make cybersecurity features of products with digital elements transparent for users
- to enable businesses and consumers to use products with digital elements securely
What kind of products will be affected by the EU Cyber Resilience Act?
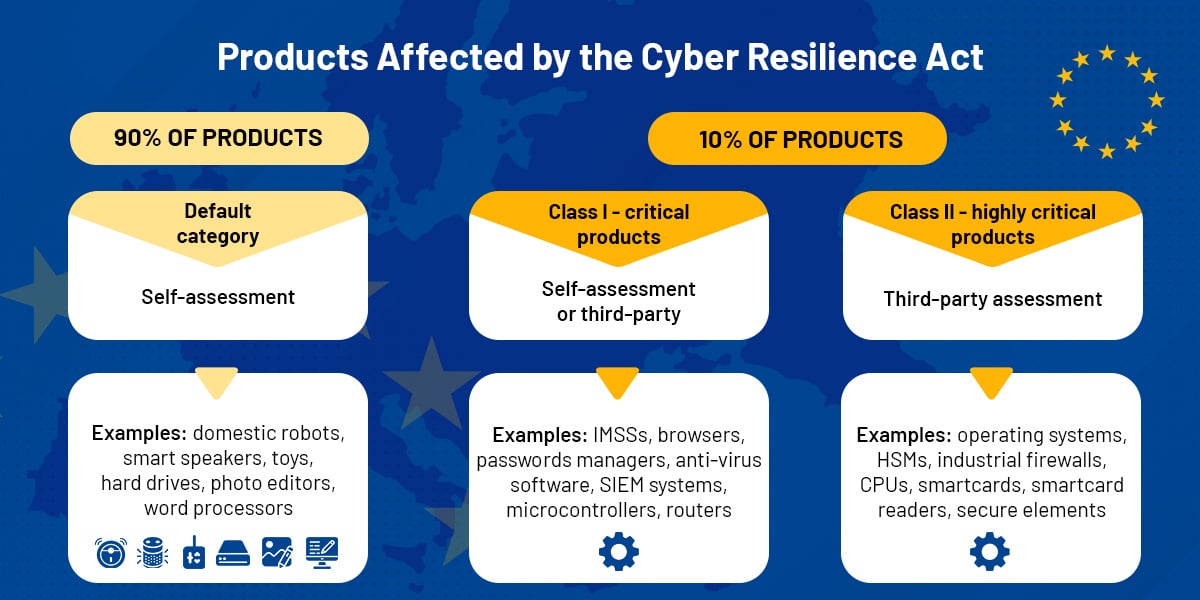
All hardware and software products with digital elements requiring a direct or indirect logical or physical data connection to a device or network will fall under the Cyber Resilience Act. The new legislation divides connected devices into the Default, Class I, and Class II category.
It is expected that 90% of the affected products will belong to a default category – IoTs such as domestic robots, smart speakers, toys, and hard drives.
Products with higher cybersecurity risk will belong either to Class I or Class II.
- Class I – critical products with digital elements, for example, IMSSs and PAMSs, browsers, password managers, anti-virus software, SIEM systems, microcontrollers, and routers.
- Class II – highly critical products with digital elements – will include operating systems, HSMs, microprocessors, smartcards, smartcard readers, and secure elements.
Download the list of all critical products Pdf here.
Products excluded from Cyber Resilience Act, already covered by other EU regulations, are motor vehicles, aviation systems, and medical devices intended for human use or SaaS (Software as a Service) products covered by NIS2. The European Commission will have the power to update and specify the list of products falling under the act.
All the hardware and software products with digital elements belonging either to Class I, Class II, or the default category will have to meet the new cybersecurity requirements. How can conformity to the new law be assessed?
Manufacturers of Class I critical products will have two options: applying existing security standards, such as the EU cybersecurity certification scheme, or going through a third-party assessment. Producers of highly critical products (Class II) will have to undergo third-party assessment, while manufacturers of IoTs from the default category will be able to perform self-assessments.
What will happen to open-source software?
Open-source software developers have expressed concern over the financial burden the new law would impose on free software creators. Since many open-source projects belong to the critical products category, they would have to go through a third-party assessment.
According to the proposed Cyber Resilience Act, free not-for-profit open-source products “supplied outside the course of a commercial activity” will be excluded from the act “so as not to hamper innovation and research.” However, questions remain over what constitutes “commercial activity,” and calls have been made for a more explicit exclusion of open source from the new legislation.
What are the Essential Cybersecurity Requirements of the Cyber Resilience Act?
There are two sets of regulations for products with digital elements – security requirements related to the features of the products and vulnerability handling requirements. Both are essential and must be met by all classes of digital products.
Security requirements relating to the properties of digital products put an emphasis on the secure design and development of products. The products have to enter the market without any vulnerabilities and possess such cybersecurity checks in place as minimization of data, access protection, data encryption, or protection against DoS attacks.
Vulnerability handling requirements have been imposed to ensure the products remain safe after being placed on the market. The requirements introduce the obligation to regularly test for vulnerabilities, report them to the public without delay and provide remediation and security updates. All discovered cybersecurity risks have to be reported to ENISA (the European Union Agency for Cybersecurity).
1. SECURITY REQUIREMENTS RELATING TO THE PROPERTIES OF PRODUCTS WITH DIGITAL ELEMENTS
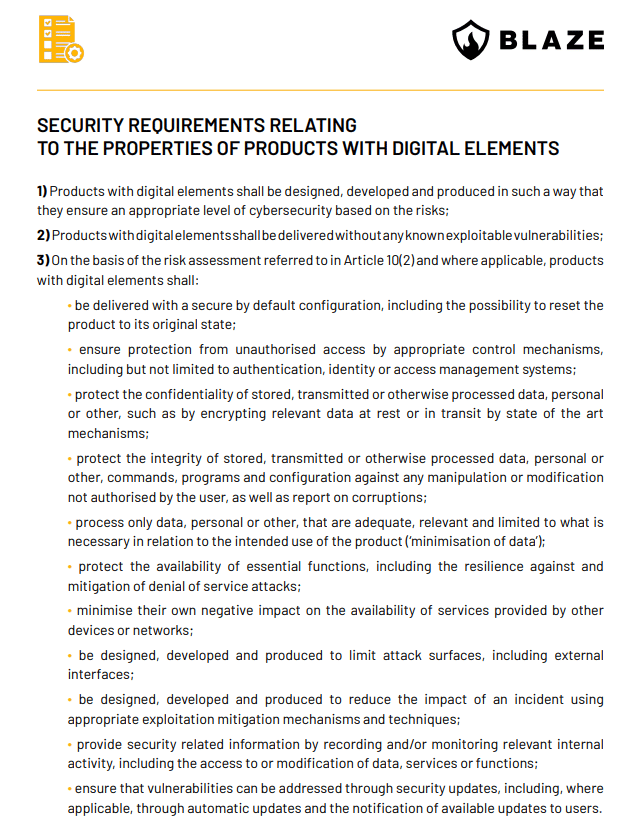
Original at https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A52022PC0454
2. VULNERABILITY HANDLING REQUIREMENTS

Additional obligations
Articles 10 and 11 of the Cyber Resilience Act text impose additional obligations on hardware and software producers, requiring them to perform a cybersecurity risk assessment and:
“take the outcome of that assessment into account during the planning, design, development, production, delivery and maintenance phases of the product with digital elements with a view to minimising cybersecurity risks, preventing security incidents and minimising the impacts of such incidents, including in relation to the health and safety of users.”
A cybersecurity risk assessment will have to be included in the technical documentation of a product with digital elements.
Manufacturers will also be obliged to exercise due diligence while integrating components sourced from third parties so that they don’t compromise the security of the digital product.
Penalties for non-compliance with EU Cyber Resilience Act
The individual European states will be responsible for enforcing the act and also for imposing fines for failure to comply with it. The most severe fine of up to 15,000,000 EUR or 2.5% of the offender’s worldwide annual turnover will be imposed on those failing to comply with the essential cybersecurity requirements and the obligations laid down in Articles 10 and 11 regarding performing security risk assessments and including the reports in the technical documentations. The market surveillance authorities will also be able to order the withdrawal of a product from the market or restrict its distribution and conduct “sweeps” detecting infringements to the regulation.
How can manufacturers prepare for the new law?
Manufacturers will have 24 months to comply with the essential cybersecurity requirements of the regulation once it is passed. The vulnerability handling requirements, however, will have to be met after 12 months. What can product makers do in preparation for the new legislation?
- Determine to which category their product belongs: default, Class I, or Class II
- Execute cybersecurity risk assessment to identify relevant risks and discover which essential requirements they have to meet
- The cybersecurity risk assessment will also allow manufacturers to meet vulnerability handling requirements.
Is penetration testing necessary for Cyber Resilience Act compliance?
Cybersecurity assessment performed during planning, design, development, integration, and due diligence will be a part of staying compliant with the Cyber Resilience Act. Its results are to be included in the documentation of the digital product. Depending on the specific cybersecurity risks the IoT carries, penetration testing may be necessary.
Annex 2 to the CRA mentions penetration testing backup infrastructure annually, testing reinstallation of backups periodically, as well as, for critical products, periodic recertification/testing of hardware and software products by independent 3rd parties and government entities.
Conclusion
The EU legislation EU Cyber Resilience Act is a response both to the growing number of cyberattacks around the world and to the increased use of IoT devices, in an attempt to reduce cybersecurity risk. In recent years, we’ve seen many high-profile attacks that have crippled companies, caused massive financial damage, and also affected private users.
Yet, almost 50% of IoT manufacturers knowingly put products with vulnerabilities on the market. The Cyber Resilience Act will help secure the whole supply chain of digital products, reducing the costs of handling the effects of cyberattacks and increasing the public’s trust in hardware and software products entering the European market.
While the act puts more pressure on manufacturers to secure their products and to share more information regarding cybersecurity with customers, it is expected to help boost demand for IoT devices, by creating more confidence in their cyber resilience.
If you are a device manufacturer interested in increasing the cybersecurity of your products, contact us to learn more about our product security services.








