Introduction
The Global System for Mobile Communications (GSM) is a mobile technology and the most popular standard for mobile phones worldwide.
Originally known as Groupe Spécial Mobile, the GSM came through the CEPT (Conférence des Administrations Européenes des Postes et Télécommunications), that in 1982, worked to develop a standard for European digital cellular telecommunications.
In 1987, a memorandum was signed to develop and implement a common digital cellular telecommunications system throughout Europe, turning GSM into a mandatory standard.
Currently, GSM is an open standard maintained and developed by 3rd Generation Partnership Project (3GPP).
Throughout the past decade, a number of security concerns have arisen and practical attacks against GSM were publicly discussed and demonstrated, especially at the Chaos Communication Congress. However, it wasn’t until a few years ago that these security vulnerabilities could be exploited using affordable hardware and open-source software.
This is the first of a series of three blog posts about security and practical attacks against GSM networks.
Part 1 will elaborate on the theory as well as discuss relevant technical details to impersonate a cell tower, whilst also demonstrating a practical spoofing attack that could be used to impersonate a legitimate mobile operator.
DISCLAIMER: All experiments were performed in a controlled environment at the offices of Blaze Information Security in Recife, Brazil. No active spoofing attacks were performed against mobile phones or other mobile devices not located within a small radius covering our lab space. This experiment did not affect any legitimate subscribers of mobile operators.
Impersonating a cellular base station with SDR
With the flexibility, relatively low cost of Software Defined Radio (SDR) and abundance of open source projects that emulate a cell tower, successfully impersonating a GSM Base Station (BTS) is not a difficult task these days.
Fake base station attacks can be useful in legitimate security research. For instance, in a scenario where a device such as SCADA field equipment connects to the Internet via GSM and is necessary to intercept the traffic between the device and the back end. A prime example of security testing that was made viable through a similar attack is the hack of BMW’s Connected Drive by Dieter Spaar.
In a nutshell, in order to impersonate a GSM BTS the attacker needs the following equipment and information:
- An SDR capable of operating in specific GSM frequencies
- Compile, install and run a software-based BTS
- Knowledge of the parameters used to identify the real mobile network operator
In the upcoming sections, we will discuss each and every element of the list of requisites to perform a BTS impersonation attack.
Software Defined Radio (SDR) Comparison
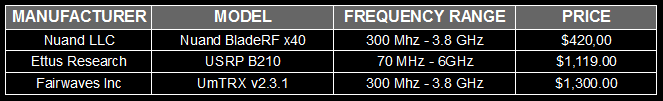
As we can see in the table above, Nuand bladeRF x40 SDR is a good choice for its cost-benefit.
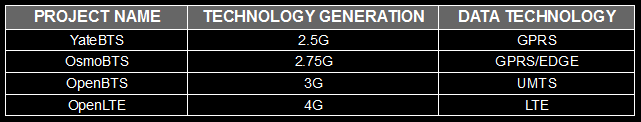
Software-defined base station projects
There are several open-source projects that allow for the deployment of software-defined base stations.
Some of these projects are:
Our lab setup
In Blaze’s mobile security labs we decided to use Nuand bladeRF x40 with two Quad-band Cellular Duck Antennas SMA.

In our experiment, we decided to use the YateBTS due to its maturity as a project, flexibility, support to Nuand BladeRF x40, its scalability, and easy implementation of new features.
For details on how to set up Nuand bladeRF X40 with YateBTS, see this blog post by a researcher known as strcpy.
Technical details
In order to spoof a base station of a real mobile operator, an adversary needs to simulate the Home Network Identity (HNI) of the target carrier. This section discusses the required parameters to achieve this goal.
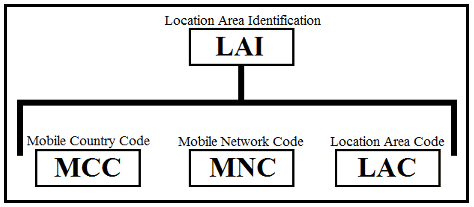
HNI is the combination of the MCC (Mobile Country Code) and MNC (Mobile Network Code). This is the number that identifies the “home” network of subscribers, also known as PLMN (Public Land Mobile Network).
NOTE: The combination used to identify the mobile network operator is also called MCC / MNC tuple.
Mobile Country Code (MCC)
The acronym MCC stands for Mobile Country Code. This parameter is used to define information about the country and geographical region.
The MCC is composed of three decimal digits, where the first digit identifies the geographic region, as can be seen in the following table:
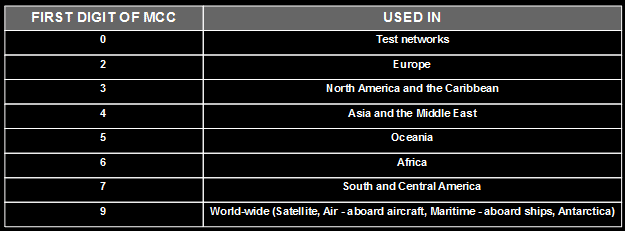
NOTE: The digits 1 and 8 are not used.
Mobile Network Code (MNC)
MNC is an abbreviation for Mobile Network Code. This parameter is used to uniquely identify a specific PLMN in a particular country (decided by the MCC). The MNC was composed initially of two decimal digits, ranging from 00-99. With the expansion of GSM networks, nowadays MNC may contain up to 3 decimal digits.
IMPORTANT: MNC 01 is not treated the same as MNC 001. The MNC is used in the International Mobile Subscriber Identity (IMSI) and Location Area Identity (LAI).
Location Area Code (LAC)
Location Area Code (LAC) is a unique number of current location areas. A location area is a set of base stations that are grouped together to optimize signaling.
Location Area Identification (LAI)
Location Area Identification (LAI) is the concatenation of the MCC, MNC, and LAC.
This information is transmitted periodically in each cell system information. Here the MNC indicates the PLMN network number. The mobile station uses this received information as an important basis for selecting the network.
Details about Brazilian mobile operators
As our main office is located in Brazil, just like most of our team, picking this country as an example was a natural course of action for these experiments.
The following table contains some technical specifications of mobile networks in Brazil:
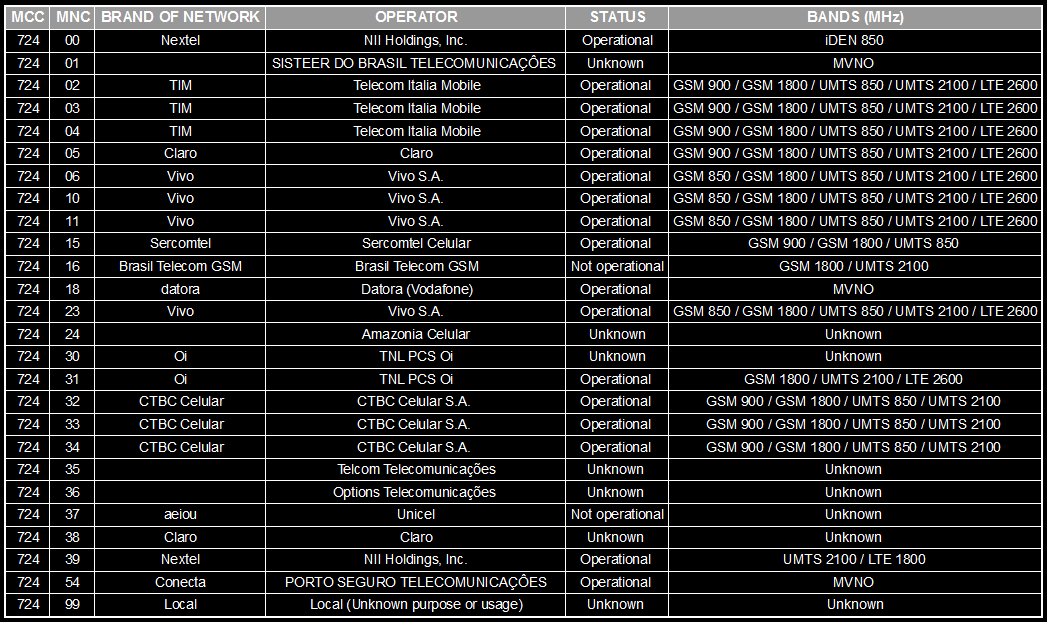
MCC, MNC, and network names
Many articles related to GSM do not explain how the mobile stations attribute names to the MCC/MNC tuples, always leaving the same question… Since the networks are identified by concatenation of the MCC + MNC (numbers only), how does a mobile station know and correctly display the network operator name?
First of all, the mobile station will search in its internal memory hoping to have some information about the network in question.
Generally, the information about 001 01 tuple (Test PLMN 1-1) is stored in the internal memory of the mobile station. If the mobile station does not find information about the network in the internal memory, it will then search for such information on the SIM card.
The SIM card usually has information about mobile carriers operating in the geographic region where it was purchased. Lastly, if the mobile station is unable to find any information about the network in the internal memory or in the SIM card, some mobile stations may receive this information over the air after registering on the network.
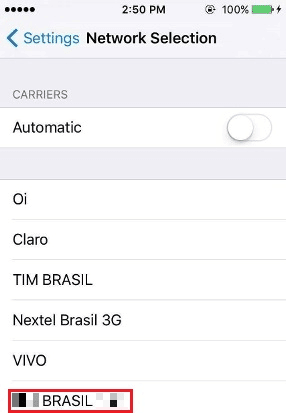
To better illustrate the explanation above, we scanned the networks around our labs to observe what the mobile station could find:
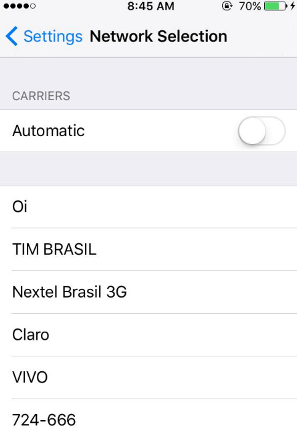
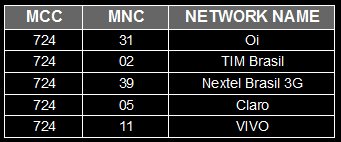
Note that network 724-666 is not automatically associated with a name, being identified only by the MCC / MNC tuple. This leads us to the conclusion that there is no information about this network neither in the internal memory of the mobile station nor in the SIM card. We can infer that the SIM card contains the following information:
Practical spoofing attack
This section demonstrates a practical BTS spoofing example against a popular Brazilian mobile provider. It’s worth mentioning again this is for illustrative purposes only and no legitimate customer was affected during this demonstration, as the radio was configured in a low-power mode in order to work only within the lab space.
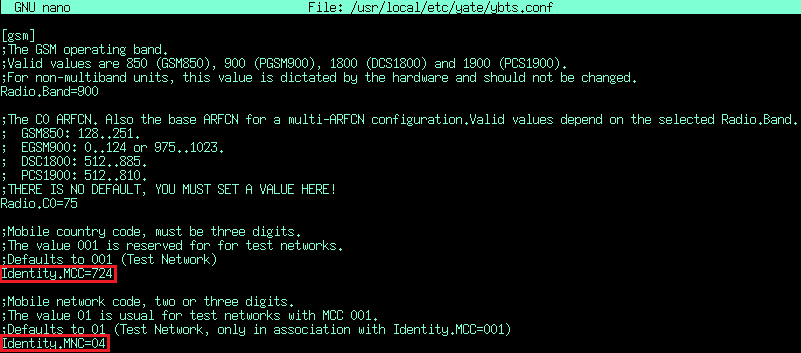
In YateBTS we set the config file to the MCC and MNC of the legitimate mobile operator, as can be seen below:
After the phone search for networks, we will have a new network, blurred in the screenshot below:
This shows the fake BTS is configured and active and can now be used to lure customers of mobile operators into connecting to the attacker-controlled BTS instead of the real carrier-operated cell tower. This can serve as a base for active and passive attacks, such as call, SMS, and GPRS data eavesdropping.
Conclusion
The first part of this post showed how easy it can be to spoof a legitimate base station using affordable equipment and open-source software. With an environment properly set up and configured, an adversary can spoof a legitimate GSM-based mobile operator, forcing customers within the radio coverage area to connect to the fake BTS instead and subsequently eavesdrop on calls, SMS texts, GPRS traffic, and more.








