This post provides a walkthrough of a privilege escalation to domain admin taking advantage of Veeam backups.
Author: Roberto Soares (during his tenure at Blaze Information Security)
In this blog post, we delve into a technical sequence of steps culminating in achieving control over a domain. This attack was executed with technical rigor, emphasizing the importance of conducting such activities strictly within authorized environments.
The initial step involved utilizing the crackmapexec tool on a specific IP range provided by the client. This tool pinpointed which Windows machines were active and listed their names.
Armed with the list of servers, the next maneuver was to use nmap, scouting for low-hanging fruit using the http-default-accounts script. At this juncture, a Windows Server 2016 Standard running a Tomcat server with default credentials QCC:QLogic66 was identified, offering us a gateway into the environment.
Upon successful authentication on the Tomcat server, our strategy progressed to uploading a customized JSP webshell. This bespoke shell was engineered to bypass the active antivirus detection, granting us command execution on the server. A local reconnaissance revealed that the Tomcat server was running with system-level privileges. Moreover, this server permitted RDP connections. With that in mind, a new local administrator user was crafted, followed by establishing an RDP connection, ensuring persistent system control.
During our exploration, we stumbled upon a drive labeled “Backup Storage (F:),” which contained a directory called “Backups,” housing server snapshots, including that of the main Domain Controller.
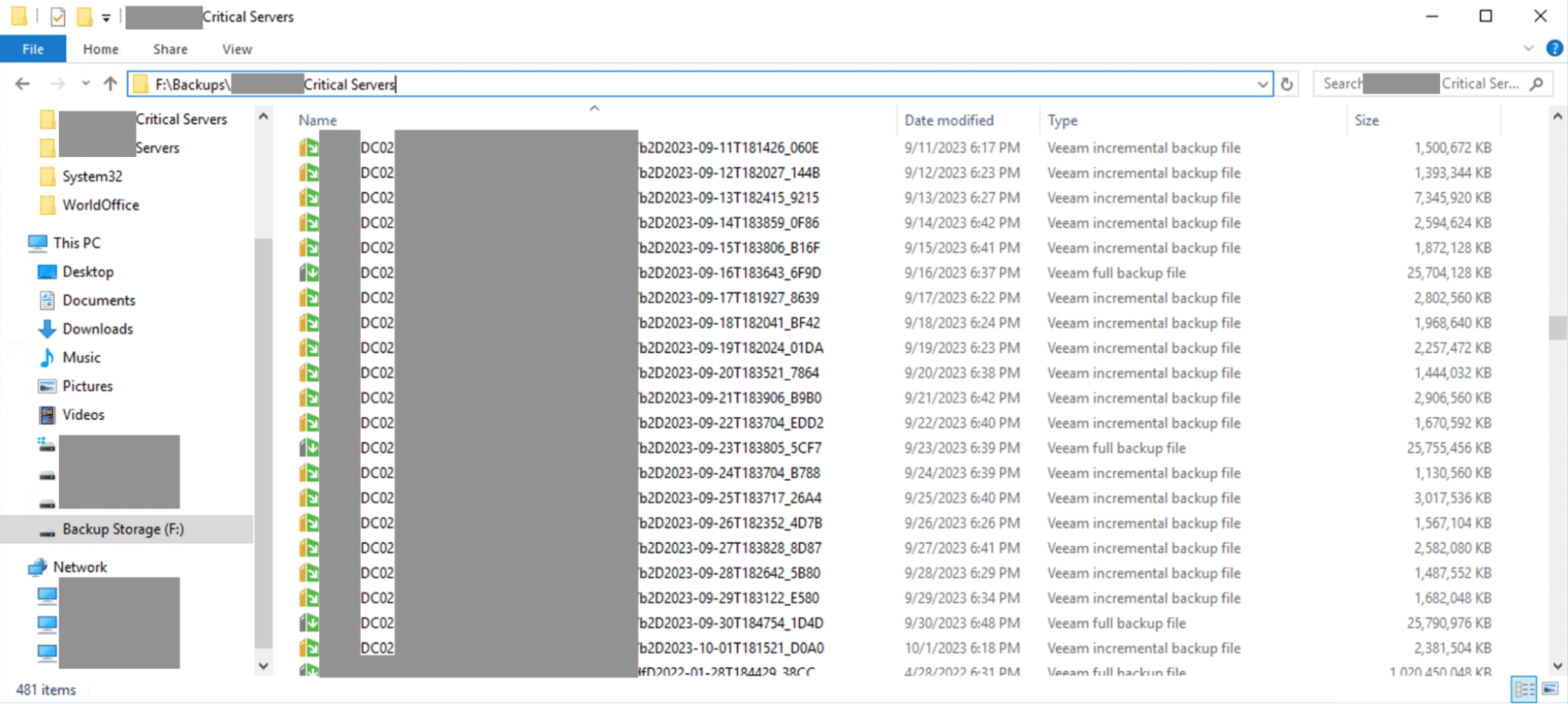
These files could potentially provide a direct route to the Domain Controller if accessed. However, the backup files were encrypted with passwords.
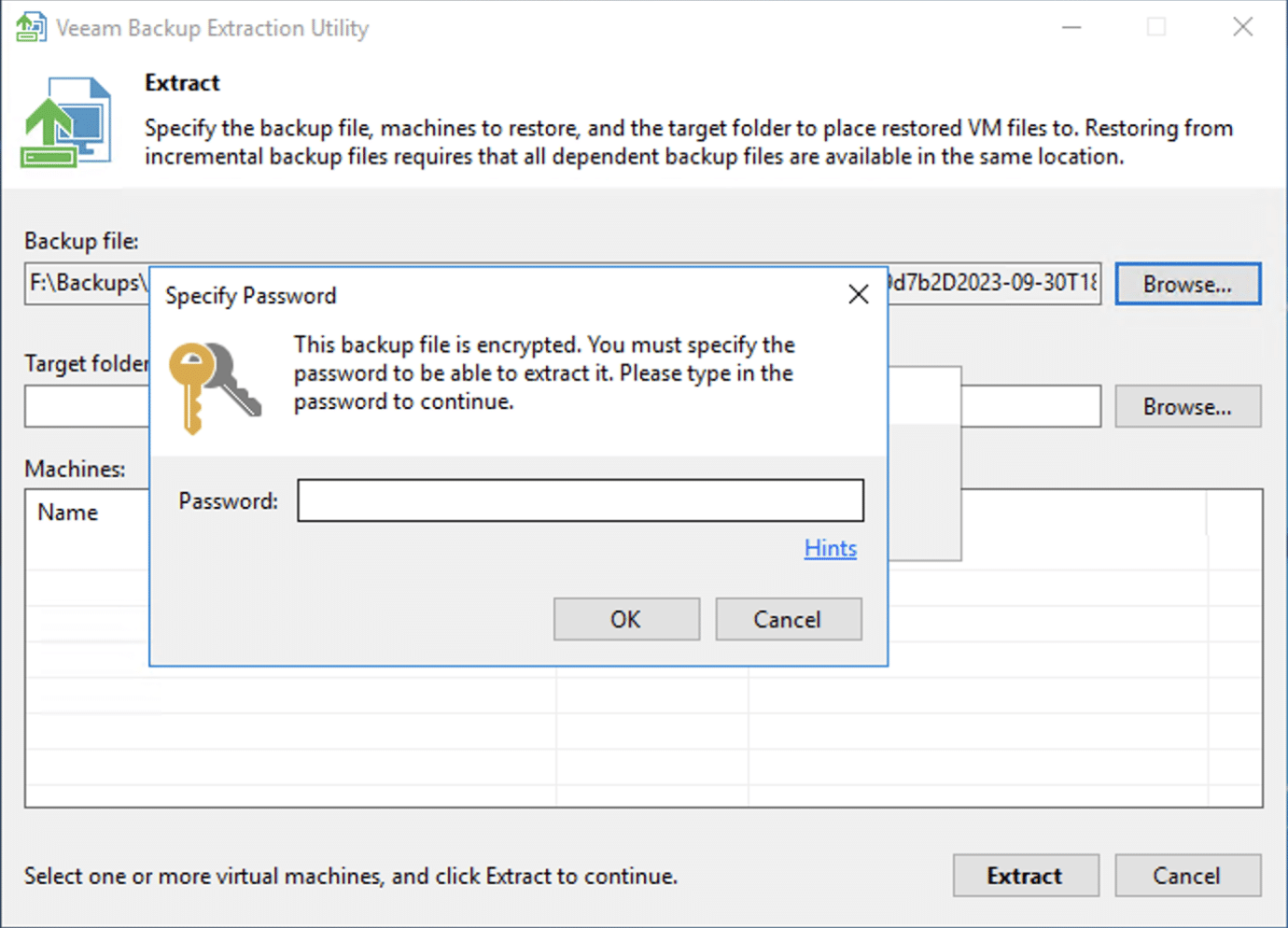
Not to be deterred, we leveraged our RDP graphical interface access, engaging the Veeam Backup software, which permitted any machine user unrestricted access. This newfound access opened up possibilities.
We deeply studied the backup tool’s mechanics, subsequently orchestrating a new backup schedule for the Domain Controller, setting it with a password of our choosing.
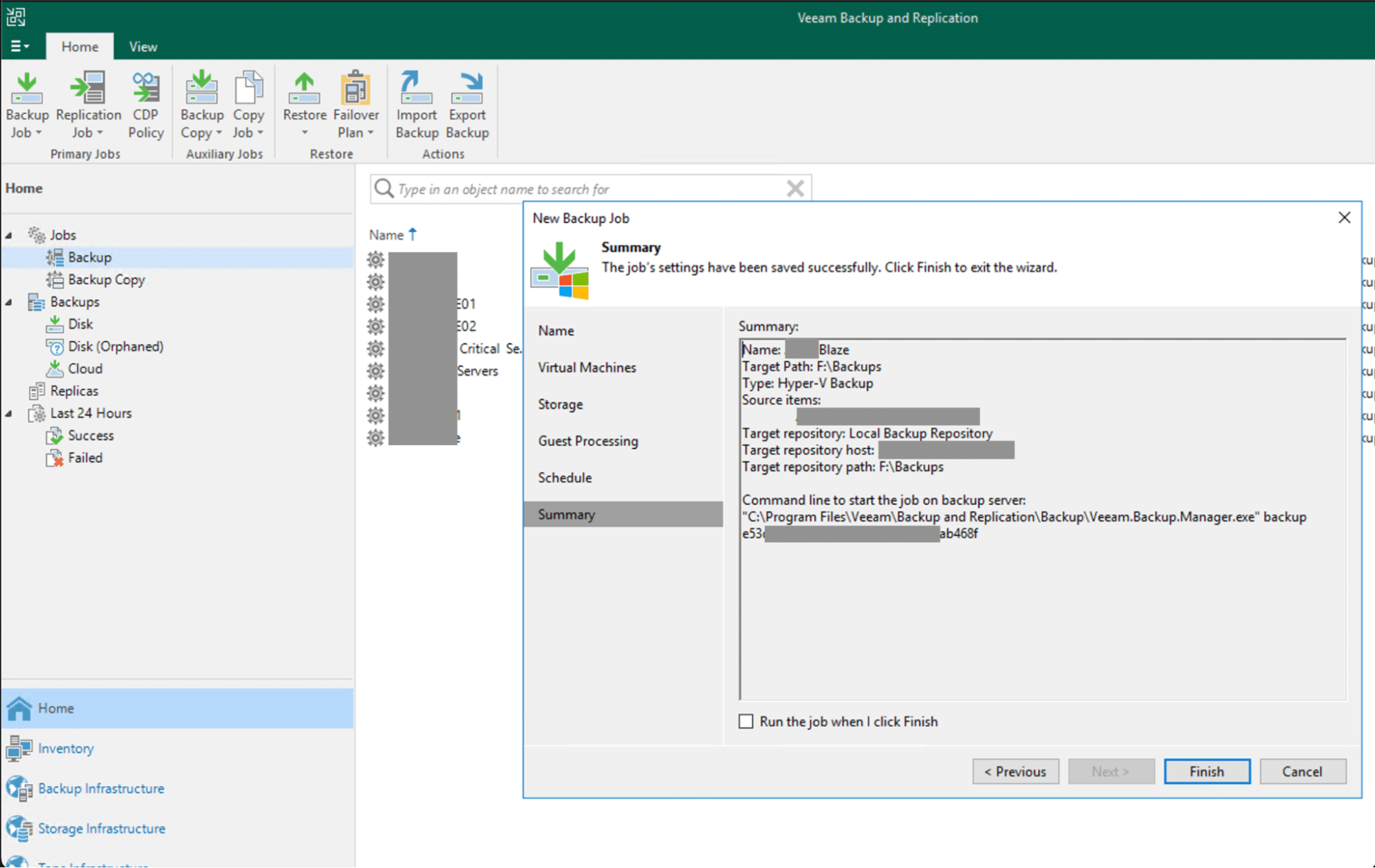
Upon successful execution of the backup process, we employed the VBK Extract Utility tool to gain access to the Domain Controller’s files. Subsequently, we mounted the VHD image using the ‘Disk Management’ utility native to the server itself. This maneuver unveiled the NTDS.dit, SYSTEM, and SECURITY files.
These were then input into the impacket-secretsdump tool, acquiring over 25,000 user hashes, notably those of the Domain Admins. Now, armed with the Domain Admins’ credentials, we turned to xFreeRDP, which supports the Pass-the-Hash (PTH) technique.
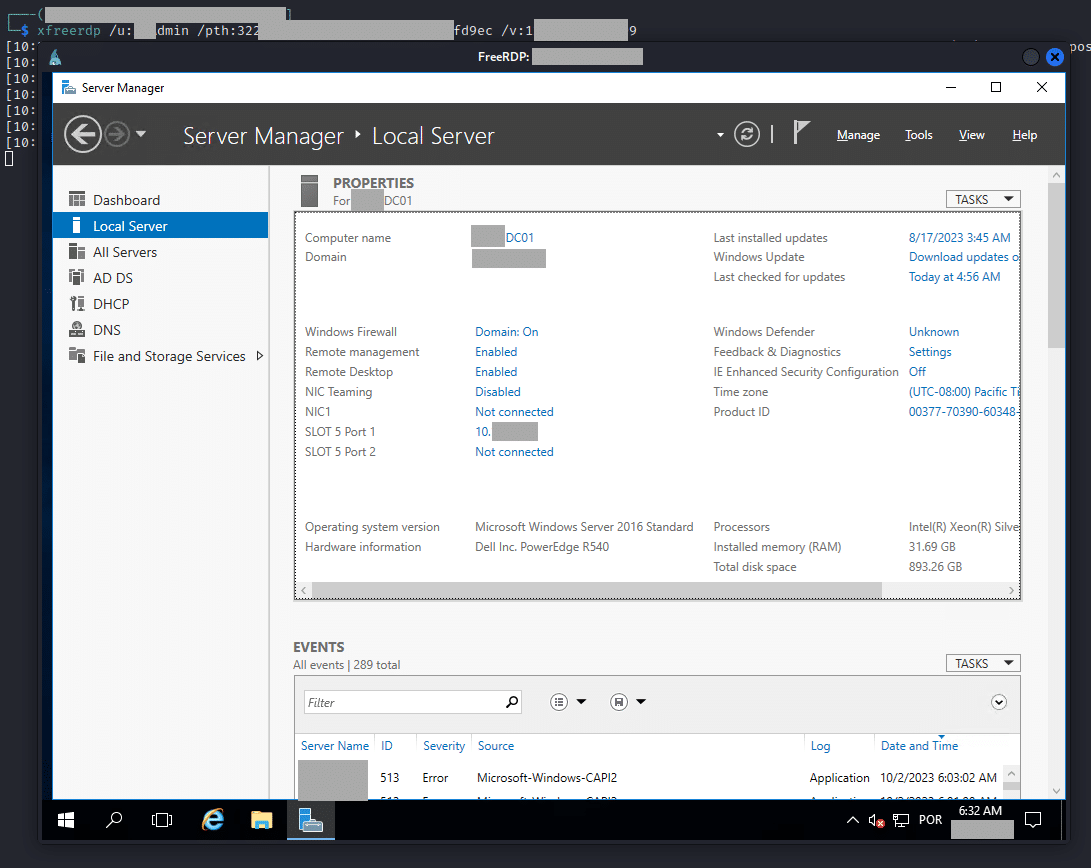
Using this, we accessed the Domain Controller and created a new user in the Domain Admin group, securing full domain dominion. Each of these maneuvers was executed with precision, cumulatively taking roughly 6 hours – with the backup generation and unpacking consuming the bulk of the time.
We also saw that it was possible to decrypt existing Veeam Backup credentials, but it was no longer necessary.
Conclusion
It’s crucial to highlight that the successful execution of this sequence was possible due to the specific circumstances in which it was carried out. In this instance, the contracting company did not have an incident detection and response team in place. This made it feasible to navigate through the various steps of the attack without immediate detection.
However, it’s essential to stress that in a genuine red team exercise or a well-prepared security environment, multiple alarms and defensive mechanisms would likely be triggered throughout this process. These alarms could lead to the swift discovery of the intrusion, loss of access, and potential identification of the threat actor. Therefore, organizations must invest in robust security measures and incident response capabilities to safeguard against such sophisticated attacks.








