Introduction
A cryptocurrency wallet is a software program used to store, send, and receive digital currencies like Bitcoin, Ethereum, and others. These wallets typically use a combination of public and private keys to secure transactions and protect the user’s assets. Public keys are used to receive funds, while private keys are used to authorize transactions. The most popular cryptocurrency wallets are software wallets and hardware wallets.
One of the key aspects of software wallets is that they can be hot wallets or cold wallets. Hot wallets are connected to the internet, allowing for quick and easy transactions, but they may be more susceptible to hacking or cyber-attacks. Cold wallets, on the other hand, are kept offline, providing enhanced security but requiring additional steps to initiate transactions.
Hardware wallets are physical devices used to store private keys offline. The main advantage is the extra layer of security by keeping private keys isolated from the internet and reducing the risk of unauthorized access.
Software wallets are popular among cryptocurrency users due to their ease of use, accessibility, and flexibility, as they are typically free to use and can be downloaded from various sources. Basically, there are three types: Desktop, Mobile and Web wallets.
One of the most popular software wallets is the MetaMask, available as a browser extension in major browsers like Chrome, Firefox, and Edge, as well as Android and iOS applications. It acts as a bridge between regular web browsers and the blockchain, enabling users to easily access and interact with dApps (Decentralized applications).
Hierarchical Deterministic (HD) Wallet
Cryptocurrency wallets generate a single private key for each individual wallet address (but you can have many addresses per key). This implies certain limitations and security risks due to the difficulty of managing multiple addresses, keeping track of balances, and creating secure backups.
In cryptocurrency, an HD wallet offers enhanced security and ease of use for managing multiple digital assets. It is based on a specification called BIP32 (Bitcoin Improvement Proposal 32) and is widely used in the cryptocurrency industry.
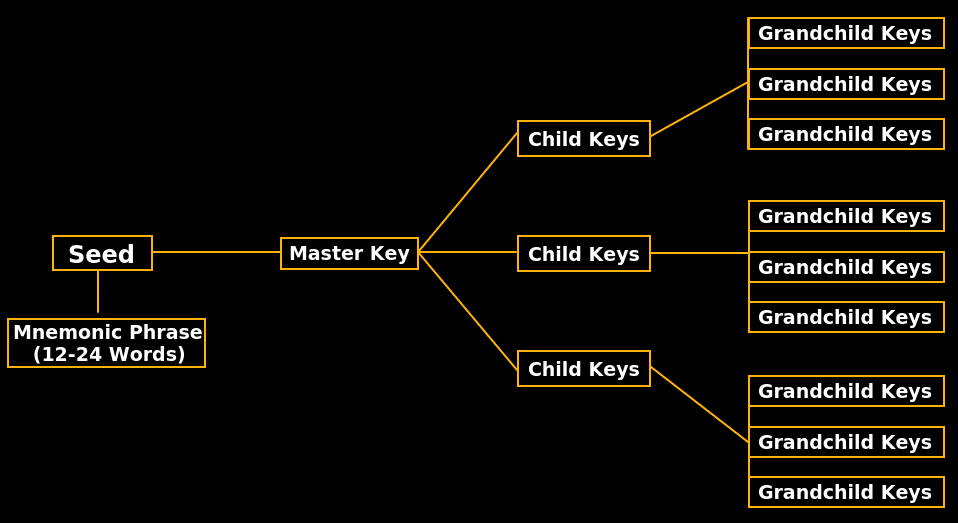
HD wallets address these issues by implementing a hierarchical structure of keys derived from a master key. The master key is generated randomly and securely during the wallet’s initialization process. From this master key, a tree-like structure of child keys is created, hence the term “hierarchical.”
The main advantage of an HD wallet is that it allows users to generate an unlimited number of unique addresses for receiving funds, all derived from a single master key. This eliminates the need to manage multiple private keys manually, simplifying the wallet management process.
Seed Phrase and Private Keys
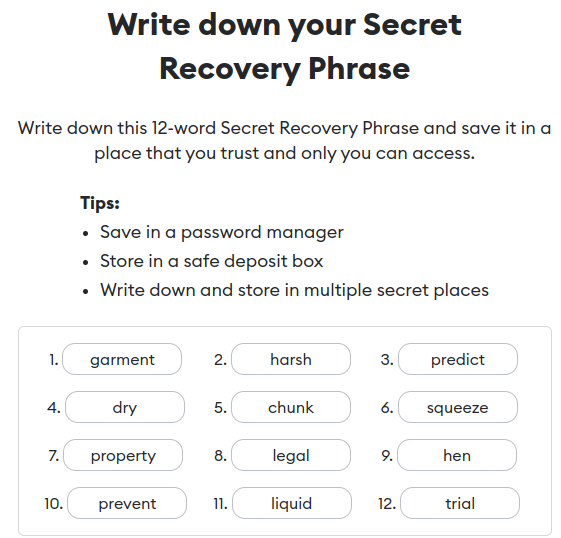
A seed phrase or mnemonic phrase is a set of words used to generate a cryptocurrency wallet’s private keys. Usually, it consists of 12, 18, or 24 words, randomly chosen from a list of thousands of words to ensure they are unique and not easily guessable.
The seed phrase should be kept securely and confidentially since it is a crucial element in securing and managing a cryptocurrency wallet, as it serves as a backup and allows users to recover their wallet in case of loss to their devices.
Below is an example of a seed phrase on MetaMask
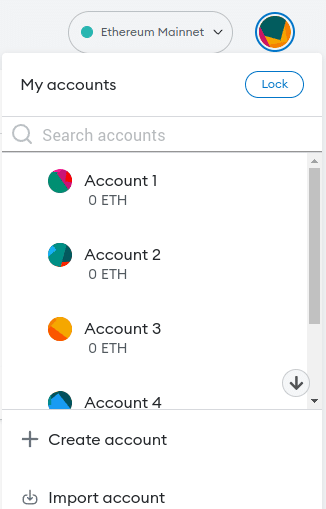
From the seed phrase, it is possible to generate several accounts inside the wallet. Each account will have an associated private key which, like the seed phrase, must be kept secure and confidential.
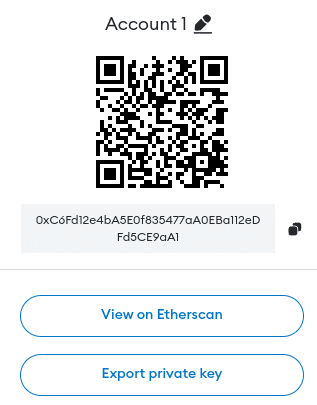
A private key is used to sign a transaction when a user initiates from their wallet, which serves as mathematical proof that the transaction is legitimate and authorized by the wallet owner.
Losing or exposing a private key can result in the permanent loss of funds and is irreversible since anyone with access to it can control the associated wallet and its funds.
While the seed phrase consists of a set of words, the private key is represented by random numbers and letters, as the red strings below:
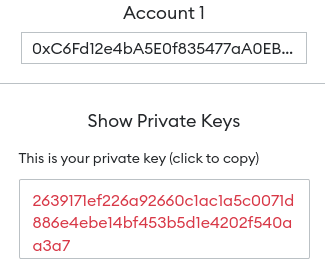
So if the private key is exposed, only the related account will be affected, while the compromise of the seed phrase will affect all the accounts that exist inside the wallet.
Common attacks
The Seed Phrase and Private Keys are very attractive to cybercriminals for a simple reason; it’s relatively easy to steal funds if any of this information was compromised, and, of course, users had valuable assets in wallets like Bitcoin, Ethereum or any asset that can be converted in fiat money. So cryptocurrency wallets can be vulnerable to various attacks, and it’s important for users to be aware of these risks to protect their digital assets. The main vectors of attacks involve the combination of social engineering, phishing scam and fake wallet apps.
In phishing scams, the attackers create fake websites or send deceptive emails that mimic legitimate cryptocurrency wallet services. These phishing attempts aim to trick users into entering their private keys, passwords, or recovery phrases, which the attackers can then use to access and steal funds from the victims’ wallets. Some scams are sophisticated, but many are not.
Social engineering involves manipulating individuals into revealing sensitive information or performing actions that compromise their security. Attackers may impersonate customer support representatives or influential figures within the cryptocurrency community to deceive users into disclosing their wallet seed or private key. Sometimes can be asked to write in the chat, but in some cases, attackers may create counterfeit wallet applications that mimic popular cryptocurrency wallets. These fake apps are usually offered on third-party app stores or websites and can contain malicious code designed to steal users’ private keys and funds.
Real example of an attacker trying to capture the private key
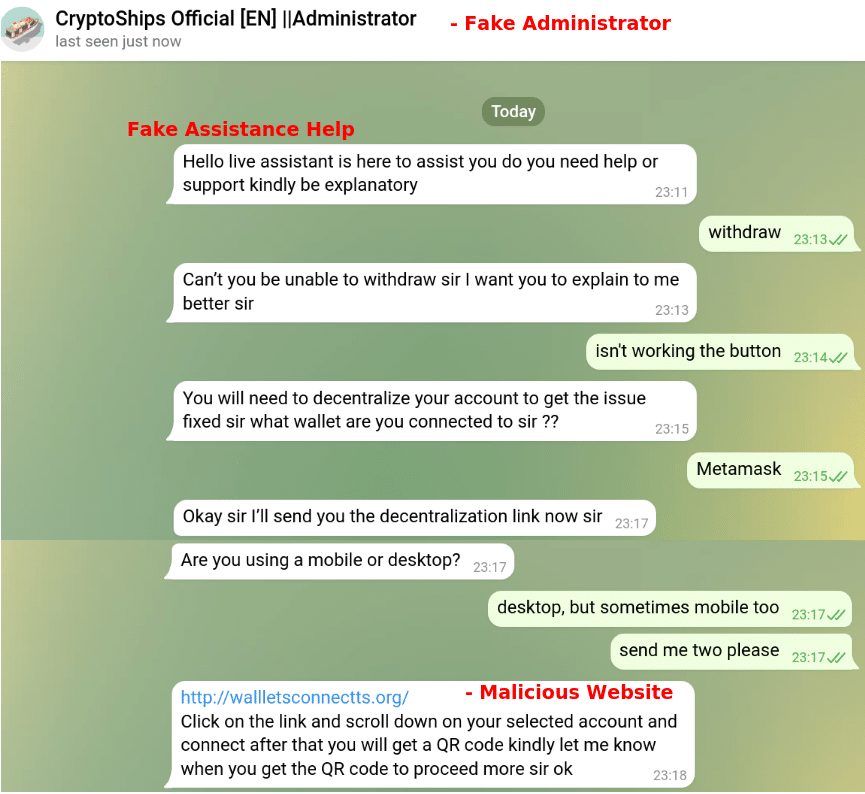
So it’s important to verify the legitimacy of requests through official channels and never share sensitive information with anyone. As a rule, admins never direct message the users first.
The users should always double-check the website’s URL, use bookmarks, and avoid clicking on suspicious links or providing sensitive information. Also, It is crucial to only download wallet apps from official sources and verify the developer’s information before installing any application.
Users should keep securing the Seed and Private Key; writing in clear text on a Desktop or in an email draft isn’t a secure option.
Extra security layer in software wallets
Some common features of cryptocurrency wallets include the ability to view your transaction history, check your balance, and send and receive digital currencies.
The security of a software wallet usually depends on the user’s practices, such as using strong and unique passwords, enabling two-factor authentication, and regularly updating the software. On the other hand, in order to use these additional layers of security, it is important that the applications provide it and that the user can trust these resources at least.
Details about the two security vulnerabilities
This section explains two vulnerabilities (already patched) in the Harmony cryptocurrency wallet. These issues were discovered in 2022 and reported to the vendor before the project shutdown as a whole.
Issue #1: PIN authentication bypass through Local Storage manipulation
The first analysis was in the Harmony Wallet extension (Chrome). The manufacturer offered an additional security feature through a four digits PIN.
Four numerical digits can be very attractive for carrying out a brute force attack, but during analysis, it was possible to bypass the Lock Wallet screen due to a lack of verification on the PIN stored on Local Storage without any automated attack.
After installing the extension on the browser, a screen to set up a new PIN is displayed:
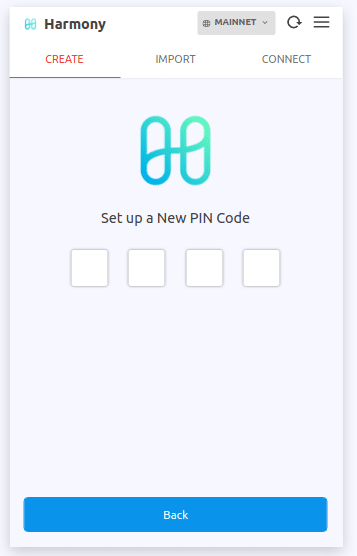
Then, through the Local Storage inspect element on Chrome, it was observed that the PIN code was null since it wasn’t set yet:
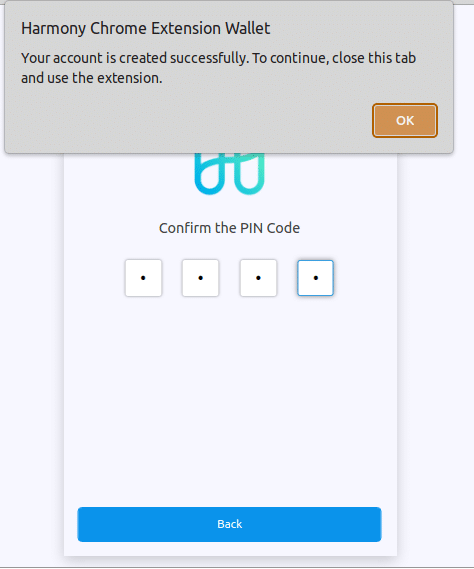
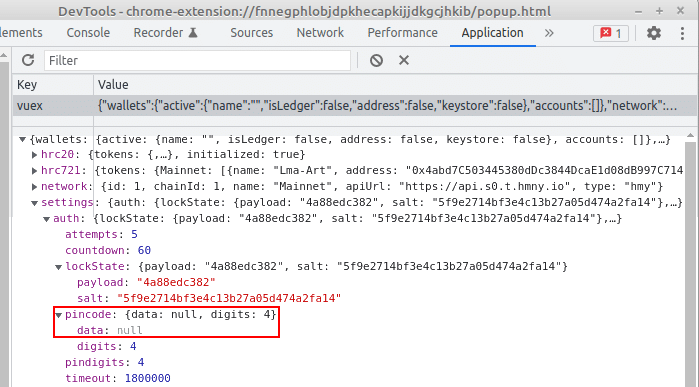
After setting the PIN it’s possible to check the Local Storage has updated the pincode:
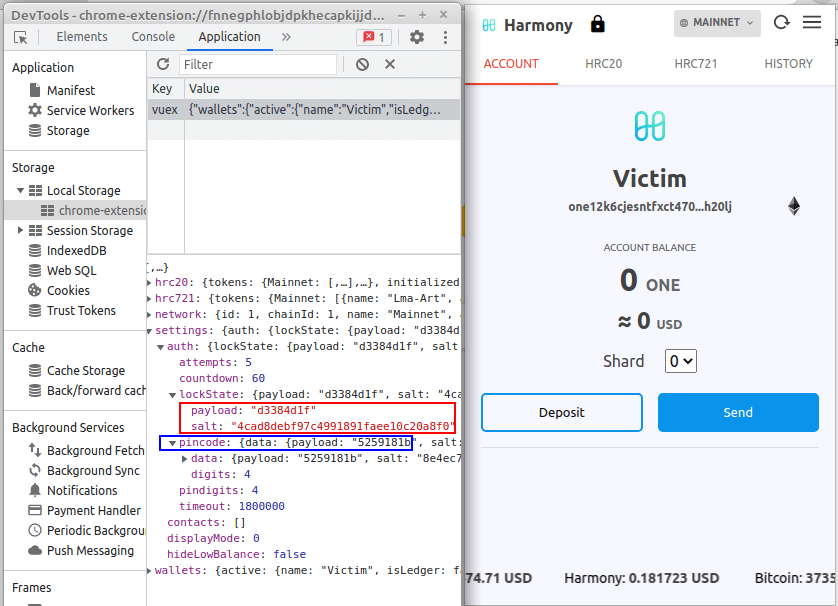
However, the vulnerability occurs in the “LockState” key by just modifying the “payload” parameter. The following image shows the Wallet Locked and the payload from “LockState”
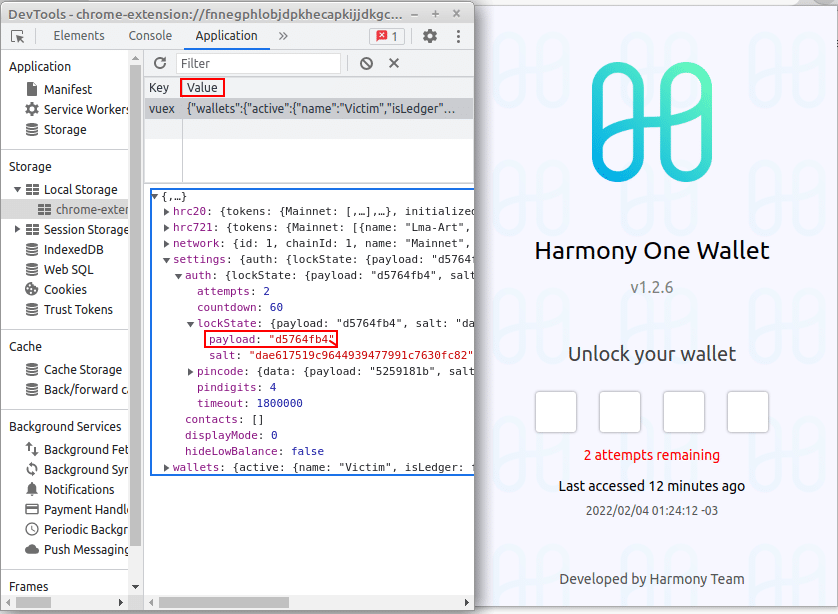
In this example above, the “payload” from “LockState” was modified from d5764fb5 to d5764fb4, just the last character to anything.
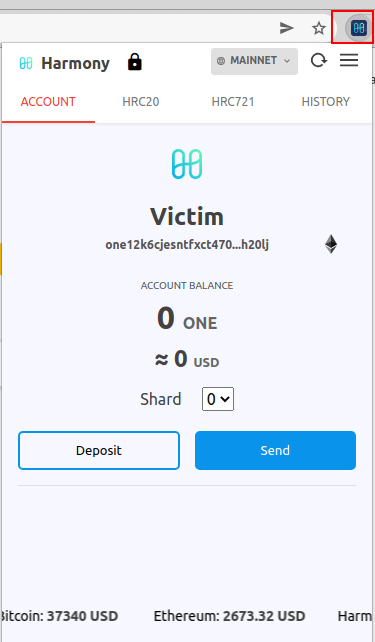
Then, by clicking on the icon of the wallet twice, we can prove the bypass:
Issue #2: Private Key and Seed Words are stored in clear text
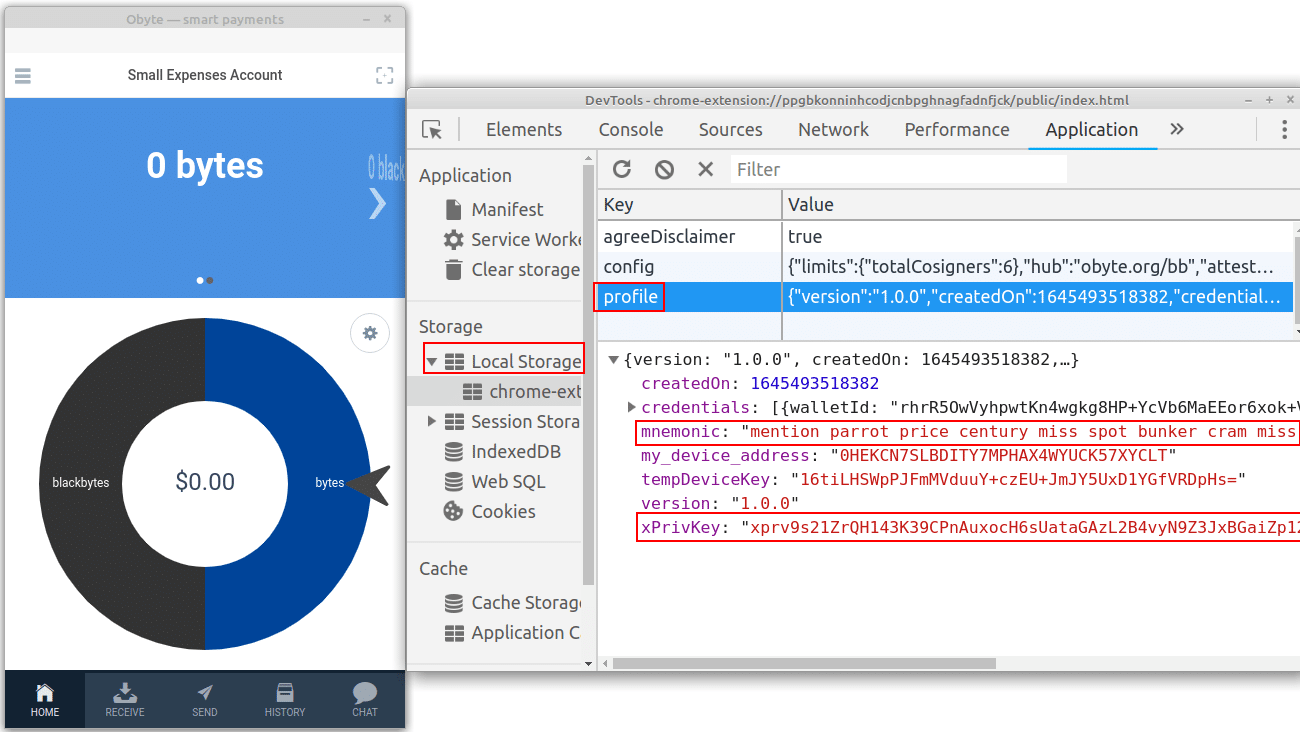
During the assessment of the oByte wallet, it was found a vulnerability that allows an attacker to capture the Private Key and Seed Words from the victim target wallet.
The vulnerability occurs due to the incorrect storage of sensitive information in the log file on ~/.config/byteball/Default/Local Storage/leveldb during a new installation setup from the oByte Wallet.
The following image illustrates the Local Storage Path before starting the new installation:
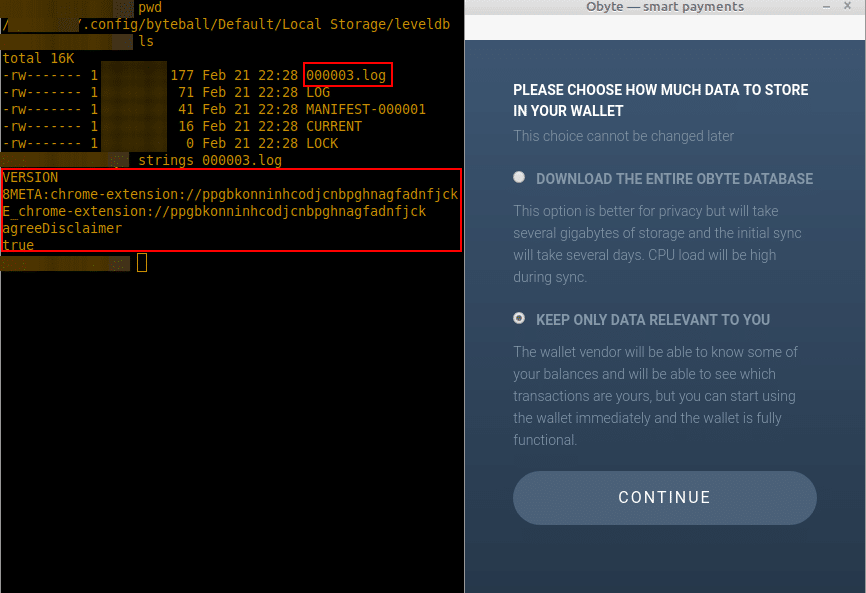
During the Setup, it was observed the new files were created on ~/.config/byteball/Default/Local Storage/leveldb. So far, no sensitive information in 000003.log file:
Just after finishing the setup, it is possible to identify the vulnerability, which are the Private Key (xPrivKey) and Seed Words (mnemonic) stored in 000003.log file:
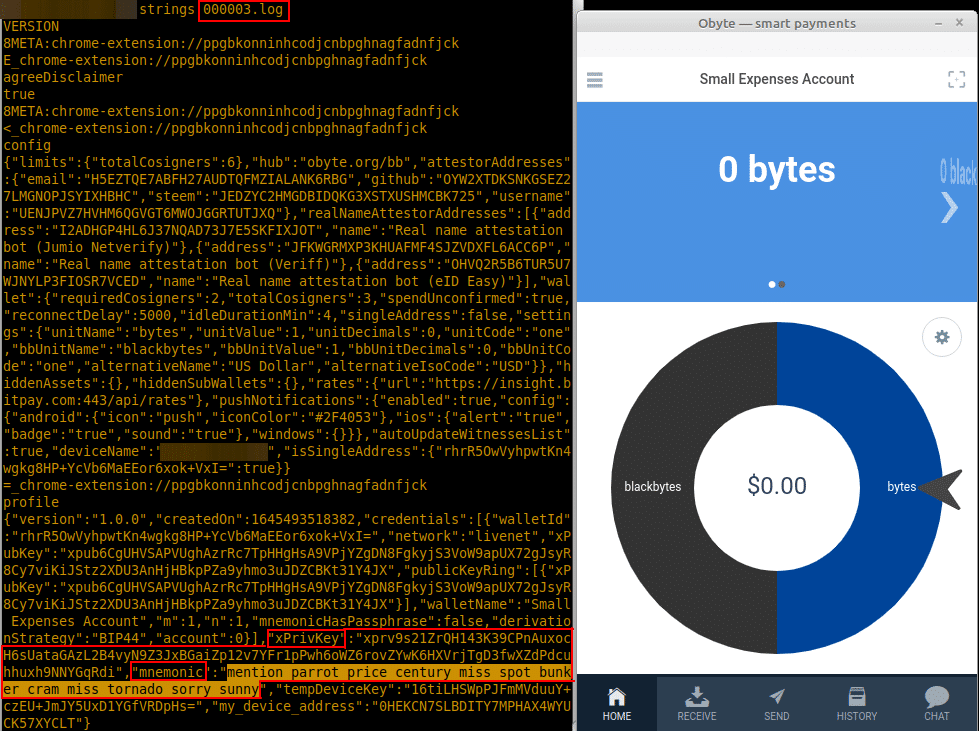
To confirm this information in cleartext just after opening the wallet and then inspecting the Local Storage with DevTools, it’s possible to fetch the seed phrase and private key:
Conclusion
The potential financial value of cryptocurrencies makes security a paramount concern for users, developers, and the entire cryptocurrency ecosystem.
Even with all the security features employed by developers, the weakest link will usually always be the users. So users must treat confidential information like seed phrases and private keys as well users should be alert to avoid attacks like a phishing scam.
On the other hand, developers should always implement security features to prevent attacks and fraud on cryptocurrency wallets. It is also important that these security features utilized are trusted since users will trust their assets.
It is important to point out that although these applications naturally work on the client side, a minimum of sensitive information should be stored, and, of course, they cannot just be forgotten there, like a private key in a cleartext file.








