EU DORA: What are the new cybersecurity requirements for the European financial sector?
What is Digital Operational Resilience Act (DORA)?
The EU’s Digital Operational Resilience Act (DORA), which entered into force in January 2023, aims to improve financial entities’ cyber resilience levels and harmonize the cybersecurity requirements for the financial sector across the whole union.
It is one of a trio of EU’s recent acts – next to CER (Critical Entities Resilience Directive) and NIS2 (Network and Information Security Directive 2) – aimed at improving cyber resilience levels of entities critical to the economy and society.
DORA’s scope is broad, as it applies to such institutions as banks, investment firms, crypto-asset service providers, insurance companies, trading venues, and ICT (Information Communication Technologies) third-party providers.
The main goals of the Digital Operational Resilience Act:
As specified in the impact assessment and European Commission’s document “Shaping Europe’s Digital Future,” DORA will ensure operational resilience of the single market for financial services by harmonizing the rules regarding information security.
- improving ICT risk management of financial firms
- increasing supervisors’ knowledge of threats and incidents;
- improving financial institutions’ testing of their systems;
- better overseeing risks from third-party ICT providers, such as cloud service providers
Who is in the scope of the Digital Operational Resilience Act (DORA)?
The regulation applies to the following entities in the financial sector:
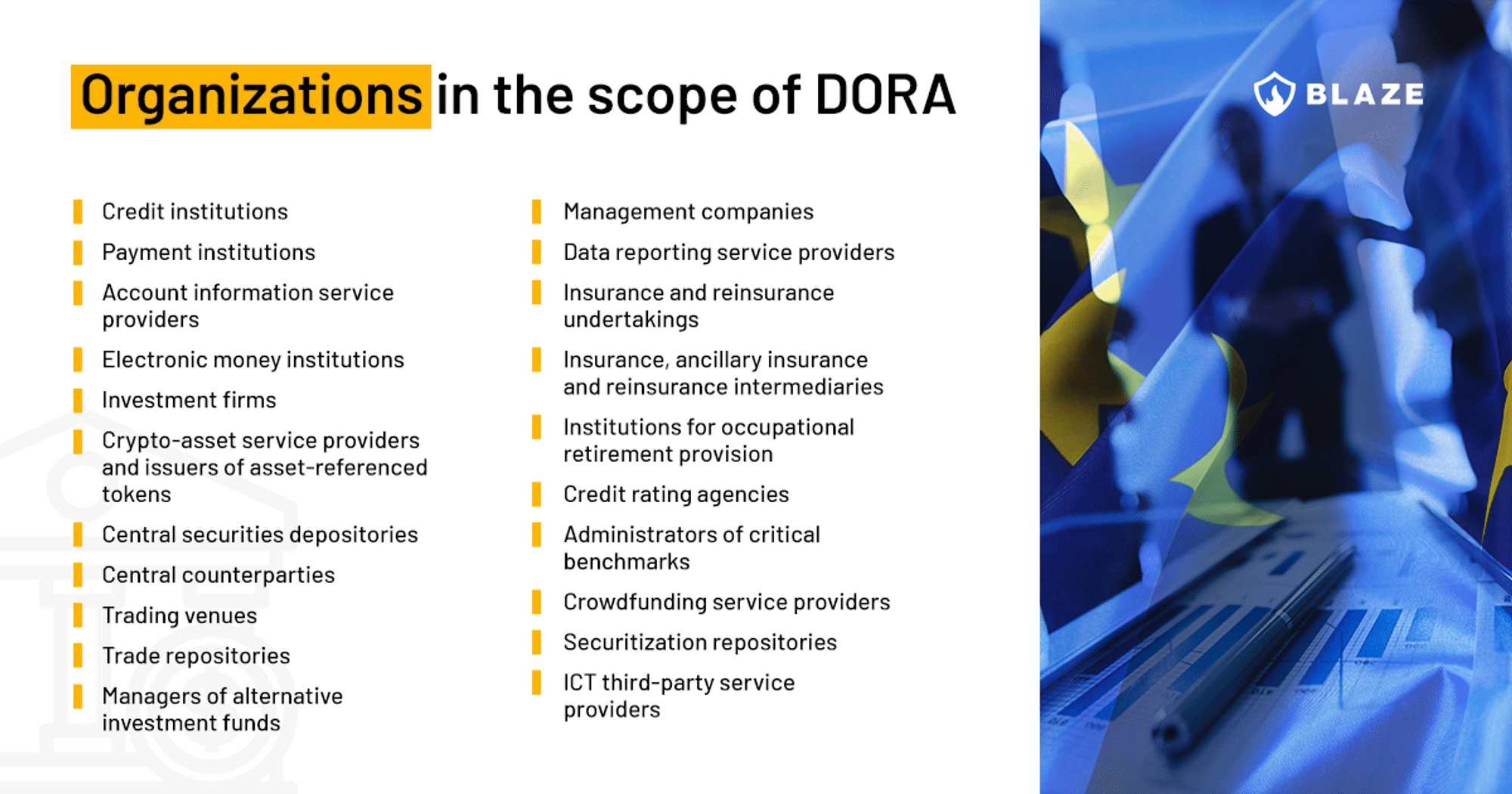
Some entities excluded from the regulation are:
- institutions for occupational retirement provision which operate pension schemes (under 15 members in total)
- small and medium-sized insurance intermediaries, reinsurance intermediaries, and ancillary insurance intermediaries
- Post office giro institutions
Will organizations of all sizes be affected?
The final draft of DORA introduces the proportionality principle, according to which financial institutions will implement the new rules “according to their size and overall risk profile, and the nature, scale and complexity of their services, activities and operations.”
Similarly, the impact assessment accompanying DORA states that incident reporting and testing measures would be less stringent for smaller financial firms.
ICT risk management requirements
ICT risk management framework
DORA obliges EU financial entities to have an ICT risk management framework, enabling them to address risks quickly and efficiently. The framework will have to include a digital resilience strategy specifying such elements as:
- the risk tolerance level of the financial entity, and the impact tolerance of ICT disruptions
- clear information security objectives
- mechanisms used to detect, protect and prevent impacts of ICT incidents;
- recording of reported significant ICT-related incidents and the effectiveness of preventive measures
- ICT multi-vendor strategy showing key dependencies on ICT third-party services providers and explaining the rationale for using such vendors
- implementing digital operational resilience testing
- communication strategy in case of ICT-related disruptions
ICT systems, protocols and tools
Financial organizations must use and maintain updated systems, protocols and tools that are reliable, technologically resilient and equipped with sufficient capacity to process the data necessary to provide their services.
Identification
As far as risk identification is concerned, all entities affected by DORA have to:
- Continuously identify all sources of ICT risk, especially the risk exposure to and from other financial entities,
- Assess cyber threats and vulnerabilities relevant to their ICT-supported business functions and assets. Financial entities must regularly (and at least once a year) review their risk scenarios.
- Perform a risk assessment after each major change in the networks, infrastructure, or in procedures affecting their ICT-supported business functions, information and ICT assets (except for microenterprises)
- Conduct regular specific ICT risk assessments on all legacy systems. They will be performed at least once a year and always before and after connecting technologies, applications or systems.
Protection and prevention
DORA imposes an obligation on financial entities to continuously monitor and control the security and functioning of ICT systems and tools and to minimize the impact of ICT risk on ICT systems.
Financial organizations must design, procure and implement ICT security policies, procedures and tools that aim to ensure the resilience, continuity and availability of ICT systems.
The ICT solutions and processes used to achieve the above objectives will have to:
- Ensure the security of the means of transfer of data
- Minimize the risk of corruption or loss of data, unauthorized access and technical flaws that may hinder business activity
- Prevent the lack of availability, the impairment of authenticity and integrity, the breaches of confidentiality and the loss of data
- Ensure that data is protected from risks arising from data management, including poor administration, processing-related risks and human error.
Detection
DORA dictates that financial entities use mechanisms to quickly detect anomalous activities, such as computer network performance issues and ICT-related incidents, and identify potential material single points of failure.
All detection mechanisms must be regularly tested.
The detection mechanisms must enable multiple layers of control and define alert thresholds and criteria to initiate incident response processes, including automatic alert mechanisms for staff in charge of incident response.
Financial entities will allocate sufficient resources to monitor user activity and the occurrence of ICT anomalies and incidents, in particular cyber-attacks.
Response and recovery
As part of their ICT risk management, financial services institutions will:
- Test the ICT business continuity plans and the response and recovery plans in relation to ICT systems supporting all functions at least yearly, as well as in the event of any significant changes to computer systems supporting critical or important functions
- Test the crisis communication plans
- Include in the testing plans scenarios of cyber-attacks and switchovers between the primary ICT infrastructure and the redundant capacity, backups and redundant facilities.
Furthermore, financial entities will regularly review their ICT business continuity policy and response and recovery plans, taking into account the results of tests and recommendations stemming from audits or supervisory reviews.
The role of management
One of the main objectives of DORA is to increase the awareness and knowledge of cyber risk among management.
Management bodies of financial institutions will inevitably have to raise their awareness of cybersecurity, as they will be officially responsible for the following:
- ICT risk management
- setting clear roles and responsibilities for all ICT-related functions
- determining the appropriate risk tolerance level of ICT risk of the financial entity
- approving, overseeing and regularly reviewing the implementation of the financial entity’s ICT Business Continuity Policy and ICT Disaster Recovery Plan
- approving and reviewing the ICT audit plans, ICT audits and material modifications
- allocating and periodically reviewing appropriate budgets to fulfill the financial entity’s digital operational resilience needs, including training on ICT risks and skills for all relevant staff
- approving and periodically reviewing the financial entity’s policy on arrangements regarding the use of outsourced ICT services
- staying informed of the arrangements with ICT third-party service providers on the use of ICT services, of any changes regarding the ICT third-party service providers, and on the potential impact of such changes on the critical functions, including receiving a summary of the risk analysis to assess the impact of these changes
- Staying informed about ICT-related incidents and their impact and about response, recovery and corrective measures.
The relevant European Supervisory Authorities (ESAs) will develop common draft regulatory technical standards specifying:
- rules on the testing of business continuity plans
- elements to be included in the ICT risk management framework
- elements in relation to systems, protocols and tools to minimize the impact of ICT risk, “with a view to ensuring the security of networks, enabling adequate safeguards against intrusions and data misuse and preserving the availability, authenticity, integrity and confidentiality of data.”
ICT-related incident management, classification and reporting
Under Digital Operational Resilience Act, financial entities will have to implement an incident management process to detect, manage and notify of ICT-related incidents. The process must include early warning indicators and “procedures to identify, track, log, categorize and classify ICT incidents according to their priority and severity and the criticality of the services impacted.”
All cybersecurity incidents will have to be recorded. Financial institutions will have to have procedures and processes for monitoring, handling and follow-up on cyber incidents to ensure their causes are identified, documented and addressed.
The management bodies of financial firms will have to be informed of at least major ICT-related incidents, with reports explaining the impact, response and additional controls regarding the incident.
Major ICT incidents will also have to be reported to the relevant national authorities.
Credit institutions classified as significant will report cyber incidents to the relevant national competent authority, which will then inform the European Central Bank (ECB).
Digital operational resilience testing
Organizations affected by Digital Operational Resilience Act will have to test all critical systems and applications at least yearly by an independent party. The testing program should include a full range of appropriate tests, including
- vulnerability assessments and scans
- open source analyses
- network security assessments
- gap analyses
- physical security reviews
- questionnaires and scanning software solutions
- source code reviews
- scenario-based tests
- compatibility testing
- performance testing
- end-to-end testing
- penetration testing
Threat-led penetration testing – TLPT
Financial entities will be obliged under Digital Operational Resilience Act (DORA) to undergo threat-led penetration testing at least every 3 years. Such pentesting will cover the critical functions and services of a financial entity (including those outsourced to ICT third-party providers) and will be performed on live production systems.
Microenterprises from the financial sector will be exempt from this requirement.
The European Supervisory Authorities (ESAs) will develop further technical testing standards in accordance with the TIBER-EU framework.
Threat-led penetration testing will be more relevant for core financial entities such as banks and payments institutions and less relevant for other subsectors (for example, asset managers and credit rating agencies).
Requirements for pentesters carrying out TLPT
For carrying out the threat-led penetration testing (TLPT), the financial entities will only use pentesting providers that:
- Are reputable
- Have technical and organizational capabilities and have specific expertise in threat intelligence, penetration testing, and red teaming;
- Are certified by an accreditation body in a Member State or adhere to formal codes of conduct or ethical frameworks;
- Provide independent assurance, or an audit report, about the sound management of risks associated with the carrying out of TLPT, including the protection of the financial entity’s confidential information and redress for the business risks of the financial entity;
- Are covered by relevant professional indemnity insurance, including against risks of misconduct and negligence.
Managing ICT third-party risk
DORA requires financial entities to incorporate ICT third-party risk management into their risk management framework.
Rules regarding pre-deal due diligence and performing risk assessments on third-party service providers are largely not new. What DORA introduces, however, is the function of a Lead Overseer, appointed by ESAs, that will have the power to audit providers of third-party services supporting critical or important functions.
What’s NIS2 got to do with it?
NIS2 directive already covers certain entities in the financial sector, including credit institutions, operators of trading venues, and central counterparties; however, as regulations of the Digital Operational Resilience Act (DORA) are more specific, it is considered lex specialis and therefore overrides NIS2 when it comes to ICT risk-management and ICT risks reporting.
Where NIS2 and DORA overlap is in the information sharing departments.
The DORA competent authorities would be able to consult and share relevant information with the Single Point of Contacts (SPOCs) and CSIRTs established under NIS2.
The competent authorities, SPOCs, or the CSIRTs established under NIS2 would also receive details of major ICT-related incidents from the competent authorities under DORA.
Penalties for non-compliance
Competent national authorities will have the power to impose penalties and establish remedial measures for any breaches of the regulation. DORA doesn’t specify minimum nor maximum fines that may be imposed; it states only that those penalties and measures must be effective, proportionate and dissuasive.
What will be the costs for financial institutions?
According to the impact assessment conducted in 2020, the new requirements would give rise to both one-off and recurring costs. Some large financial firms have already made significant investments in their computer systems, and for them, the costs of implementing the measures of this proposal are likely to be low.
For smaller firms, the costs are expected to be lower as well, as they would be subject to less stringent measures proportionate to their lower risk.
When it comes to testing, the European Supervisory Authorities have estimated that the costs related to threat-led penetration testing range between 0.1% and 0.3% of the total ICT budget of affected organizations.
Costs related to incident reporting would be drastically reduced, as there would be no overlaps with NIS in this regard.
Towards compliance with EU DORA – steps you need to take

Conclusion
As specified in the impact assessment and European Commission’s document “Shaping Europe’s Digital Future,” DORA will ensure operational resilience of the single market for financial services by harmonizing the rules regarding security.
By addressing the gaps and overlaps in such areas as third-party risk management, ICT-related incident reporting, and digital operational resilience testing, EU DORA will contribute to creating a more resilient operating environment for all financial market participants.
Provisions will apply from 17 Jan 2025.








