Advisory information
Title: Signal IDN homograph attacks
Advisory reference: BLAZE-01-2019 (CVE-2019-9970)
Product: Signal
Disclosure mode: Coordinated disclosure
Product Description
The signal is an encrypted communications app for Android and iOS. A desktop version is also available for Linux, Windows, and macOS. It uses the Internet to send one-to-one and group messages, including files, voice notes, images, and videos, and make phone calls.
Signal uses standard cellular mobile numbers as identifiers and end-to-end encryption to secure all communications with other users. The applications include mechanisms by which users can independently verify the identity of their messaging correspondents and the integrity of the data channel. (from Signal’s Wikipedia page)
Vulnerability details
Signal Desktop and Android are vulnerable to an IDN homograph attack when displaying messages containing URLs.
A homograph attack is a security vulnerability that can deceive users into thinking they are visiting a certain website when they are directed to a different, but homograph, domain name. This vulnerability can be used to weaponize social engineering, significantly increasing the chances of a successful attack.
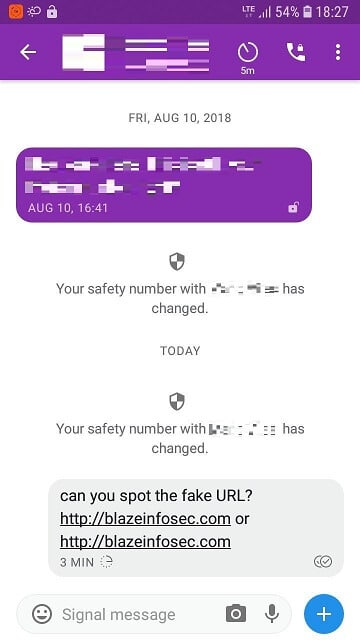
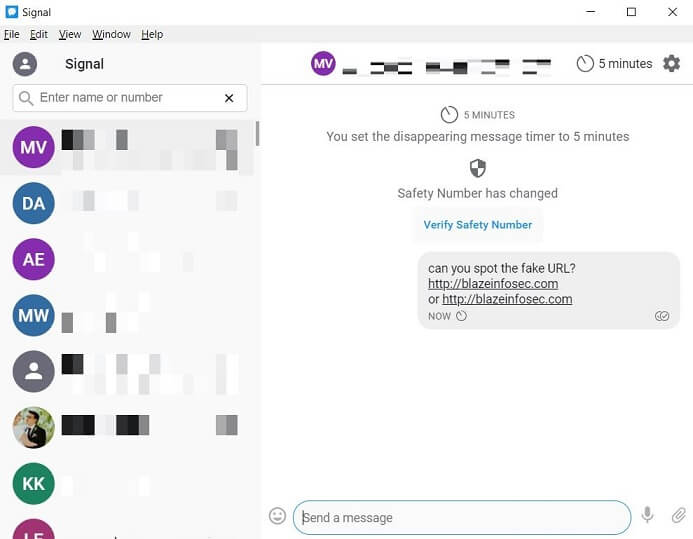
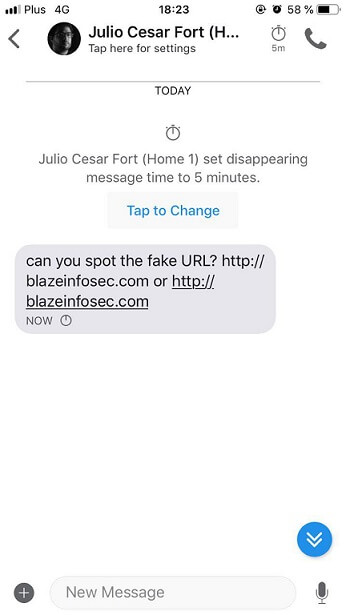
Upon receiving a message with a link, Signal renders it in a clickable format, and the font used to display the message makes it impossible to distinguish between the legitimate URL and the malicious URL, for example:
- Legitimate URL:
- Malicious URL: – with the ‘a’ as a Cyrillic character, not Latin
Upon clicking on the malicious link, a user will be taken to https://blаzeinfosec.com/ instead of the real https://blazeinfosec.com, despite the fact the link is displayed exactly as the expected website.
A sample attack scenario against a Signal mobile user:
- An activist or person of interest uses Signal for Android
- The person receives a URL in a Signal message disguised as a legitimate one and clicks on the link
- The malicious URL serves a one-click browser exploit
- Target gets infected with mobile malware
Additionally, the mobile version of Tor Browser (Orfox, in Android) is vulnerable to the same class of attack. Therefore, users of Signal with Tor Browser (which does not seem to be a rare combination) are vulnerable to full-blown phishing attacks.
Fix and recommendations
Blaze Information Security recommends Signal to “defang” URLs just like it is done in its iOS version.
URLs with mixed scripts (e.g., Latin and Cyrillic in the same domain name) or URLs using scripts not installed or enabled in the device should be displayed in the message as un-clickable.
Alternatively, Signal could implement the same strategy used by WhatsApp to mark the link as insecure, with a clear warning message to the user when an IDN homograph domain name is encountered in the message.
The vulnerability has been addressed by Signal, at least in version 4.35.3 for Android. As of now, Windows-based Signal for Desktop is still vulnerable. Users should upgrade Signal to its latest version.
Credits
This vulnerability was discovered and researched by Julio Cesar Fort from Blaze Information Security
Disclosure timeline
31/01/2019: Initial contact asking for the vendor’s PGP key
31/01/2019: Vendor responded, asking for details of the vulnerability to be sent, surprisingly, via unencrypted e-mail
31/01/2019: Vulnerability details sent via unencrypted mail
01/02/2019: Signal responds, “it seems like standard behavior here is to rely on the browser to disambiguate
these names (and the registrar to prevent issuance of ambiguous names).”
01/02/2019: Blaze responds, citing one-click exploits and the case of Ahmed Mansoor and Pegasus malware as a credible attack scenario
03/02/2019: Blaze sends a report to Signal informing Tor Browser for Android is vulnerable, turning it into a full phishing chain
12/02/2019: Signal responds, “We don’t consider this a ‘vulnerability’ or ‘bug'”, despite evidence showing otherwise.
Unknown 2019: A fix was released – the vendor never informed Blaze about the fix.
23/03/2019: Advisory released
References
Signal:
IDN homograph attack:
The Homograph Attack:
About Blaze Information Security
Blaze Information Security is a privately held, independent information security firm born from years of combined experience. With a presence in South America and Europe, Blaze has a team of senior analysts with experience in leading information security consulting companies worldwide and a proven track record of published security research.
E-Mail: [email protected]
Wildfire Labs blog:
Twitter:
Github:
PGP key fingerprint: DB53 D9D9 F0E1 E513 4F52 8219 C33B C7FA C5D0 E926