Learn why lists containing the Top 10 best penetration testing companies are false and how to effectively select the right pentest company for your cybersecurity needs.
As the importance of pentesting and security assurance has grown, so has the number of lists claiming to highlight the ‘Top 10 Best Penetration Testing Companies.’ These lists garner much attention and, at first glance, seem like a helpful source for decision-makers needing high-quality cybersecurity and penetration testing services.
This post aims to delve deeper into the concept of top 10 lists for penetration testing companies and discuss our opinion on why these lists may not be as reliable as they first appear and the reasons why they should not be seen as a credible source of advice.
The flawed concept of ‘Top 10 Penetration Testing Companies’
These Top 10 lists are common across various sectors, and the cybersecurity industry is no exception. A simple online search for the best penetration testing providers will return a barrage of articles, each featuring its own ‘Top 10’ list.
These rankings claim to present the best of the best, the companies at the pinnacle of the penetration testing and cybersecurity industry. They seem to offer an overly simplified solution to the rather complex problem of choosing the right penetration testing service provider.
It’s not difficult to understand why these lists attract attention. They promise a condensed, easily digestible snapshot of the industry, which can be particularly appealing to those who don’t have the time and want a fast quote or those who lack the necessary knowledge to systematically compare providers. But while they might be a convenient starting point, these lists are far from the definitive guide to the penetration testing landscape they purport to be, and in many cases, are categorically misleading.
The problems in ‘Top Penetration Testing Companies’ lists
In this section, we’ll expose the flaws in these Top 10 lists, present our arguments on the main problems surrounding them, and attempt to guide you in choosing a penetration testing provider that suits your organization’s unique needs.
Lack of transparency and objective criteria
The first point to understand is that these Top 10 lists often lack a comprehensive and objective set of criteria to rank the providers. It’s important to ask yourself: How exactly did these companies land on these lists?
In many cases, these rankings are directly influenced by marketing relationships and paid placements, not by the actual quality or breadth of services provided. The criteria used can often be opaque or non-existent, making it hard to determine what factors have been considered.
Several lists prioritize companies that have larger marketing budgets rather than those that provide the most thorough or effective penetration testing services or are reputable penetration testing companies.
Unlike well-known industry accreditation such as CREST, where they establish a minimum threshold of requirements and a set of objective criteria for a penetration testing company to become a member and join their directory of providers (without bragging that those organizations are the best in the world), the so-called ‘Top 10 Best Penetration Testing Companies‘ lists simply have been made up by tech blogs looking to monetize their SEO prowess to sell spots in their list to pentest companies that are willing to pay for them.
The processes used to determine these rankings are often opaque, with little to no information about how data was gathered, what factors were considered when evaluating the penetration testing companies in the list, and how different elements were weighted. This lack of transparency makes it hard to trust the credibility of the rankings.
One-size-fits-all problem
Another flaw with these lists is the assumption that one size fits all. Different organizations have different needs, risks, and vulnerabilities. What works for one may not work for another.
For instance, a small e-commerce business might require a different set of penetration testing services than a large healthcare organization with multiple facilities and vast amounts of sensitive patient data. A top-ranked company may specialize in large enterprise solutions and might not be the best choice for a small business, and vice versa.
Still, on this topic, a firm specializing in cloud penetration testing may not excel at other services, such as security code review or physical security testing. Therefore, it’s hard to establish a credible rank, and it’s misleading for a provider to claim to be the best penetration testing company just like that.
The proliferation of pay-to-play fake security industry awards and magazines
With the growing popularity of cybersecurity, recent years have seen the proliferation of security industry awards that are essentially fake, made up by marketing companies that create these fictitious awards to create demand generation for themselves. Basically, it is a secondary source of revenue, and later, attempts are made to upsell other marketing services to these clients (cybersecurity companies).
There are simply no criteria for these awards and, in many cases, no information about a panel of judges; it’s impossible to tell if reputable cybersecurity professionals and CISOs were involved in judging these providers or not.
Some awards are straight-up sponsored, and on their website, you can see the price tag of how much it will cost for your company to be listed as a contender as a top provider. The same goes for magazines in the area, which charge anywhere from $3,000 for an advertisement to place your organization on its cover as a thought leader in the cybersecurity and penetration testing space. Sadly, we’ve seen more than one penetration testing company engaging in desperate tactics for attention and funding the proliferation of such fake awards.
Speaking from our own experience, we are regularly approached by marketing agencies behind organizing events, magazines and awards that have questionable reputations and veracity. It is only safe to assume that other pen testing companies are also offered to participate in such fake awards, and some companies may decide to accept the offer.
Recently, Mark Curphey from CrashOverride wrote a great piece about this topic named Why you should not give a f*ck about security awards – a recommended read.
The ranks are either sponsored or written by the pentest company itself
As of this writing, out of the top five Google results when searching for “penetration testing companies,” “penetration testing company,” or “best penetration testing companies,” three of them are written by pen testing vendors themselves in their own company blog or can be found in paid placements in industry publications. To no one’s surprise, these vendors rank themselves as the top pentesting provider in the list.
These pentest companies leveraged clever content marketing and search engine optimization (SEO) to trick Google’s algorithm and mislead the public into believing they are the best penetration testing firm. They expect you to believe in a list they compiled themselves or paid a blogger for their spot.
Deliberate comparison between apples and oranges
When reviewing these lists, a keen observer may notice a pattern of deceiving comparisons between providers that don’t offer the same types of services and products.
Both in the paid placement lists and the ones written by the penetration testing companies themselves, almost all other companies they rank in the list are not vendors offering pen testing services but instead automated pentesting tools and scanners; or they rank companies that are not direct competitors because they either operate in a different region or a distinct tier in the market.
Nobody who paid their way through the fallacious list of top penetration testing companies is comparing themselves with their competitors.
Looking for a pentest provider? Let us challenge your cyber defenses.
Talk to our experts for a custom quote
Misleading portrayal of competence
A significant concern is that these lists can give a misleading portrayal of competence. Just because a company is well-known or has a strong brand does not mean it delivers superior penetration testing services. A prime example of this is the fact every Big 4 and large audit and accounting firm offers pentesting as part of their service portfolio, but the truth is the best penetration testers and cybersecurity practitioners in the market never dreamed of working in an audit firm wearing a suit and a tie.
Reputation, while important, is not always a guarantee of the quality of service. Some companies might excel in one area of cybersecurity, such as managed services or incident response, but fall short when it comes to penetration testing. Other companies might simply not live up to their reputation when delivering thorough and accurate security testing assessments. In a worst-case scenario, some companies might even use these lists as a marketing tool, overselling their skills to make it onto the list but under-delivering in practice.
By understanding these flaws, you can see why these Top 10 lists might not be the ideal guide when searching for the best pen testing service providers.
Later in this post, we will discuss the right approach to choosing the right penetration testing company to be your next cybersecurity partner.
Infographic

The right approach to choosing a penetration testing provider
The flaws in the Top 10 lists illustrate the need for a more considered and rigorous approach to choosing a penetration testing provider. So, what should you look for? Here are a few key factors to consider when defining guidelines and criteria for selecting a pentest provider.
Manual penetration testing vs. automated vulnerability scans
Ensure the penetration testing company delivers manual pentesting, not just automated vulnerability assessments. You must understand that some cybersecurity vendors may offer automated scanning, deceptively presented as manual penetration testing services.
In your journey towards improving security, understanding the difference between these two approaches and ensuring you procure the correct service is fundamental.
While automated vulnerability assessments can serve a purpose in pinpointing known patterns of misconfiguration and vulnerabilities, they are no replacement for a security assessment conducted by a seasoned penetration tester.
Know your security testing needs
When engaging with a vendor, know your security testing needs and understand if the provider you’re talking to is really the right choice for them.
For example, it makes little sense to engage a vendor that is known to be good at social engineering testing when all you need is an automated vulnerability scanning service or award a contract to a mobile app security testing project to a company that is more inclined in compliance services and only touches pentesting on the surface, or vendors good at network security audits to perform a pentest of an IoT device.
Industry experience, certifications, and methodologies
The market isn’t lacking in penetration testing certifications. Some are revered in the industry for their high standards and focus on practical, hands-on examinations.
In contrast, some barely pose a challenge and fail to effectively evaluate a candidate’s proficiency to execute a professional-level pentest.
Here are some certifications that guarantee a penetration tester is equipped with the practical skills necessary to conduct a pentest assessment:
- Offensive Security Certified Professional (OSCP) and Offensive Security Web Expert (OSWE)
- Burp Suite Certified Practitioner (focused on web/API security testing)
- SANS GIAC GPEN and GWAPT (favored in the US)
- CREST CRT and CREST CCT (preferred in the UK, Singapore, Hong Kong, and Australia)
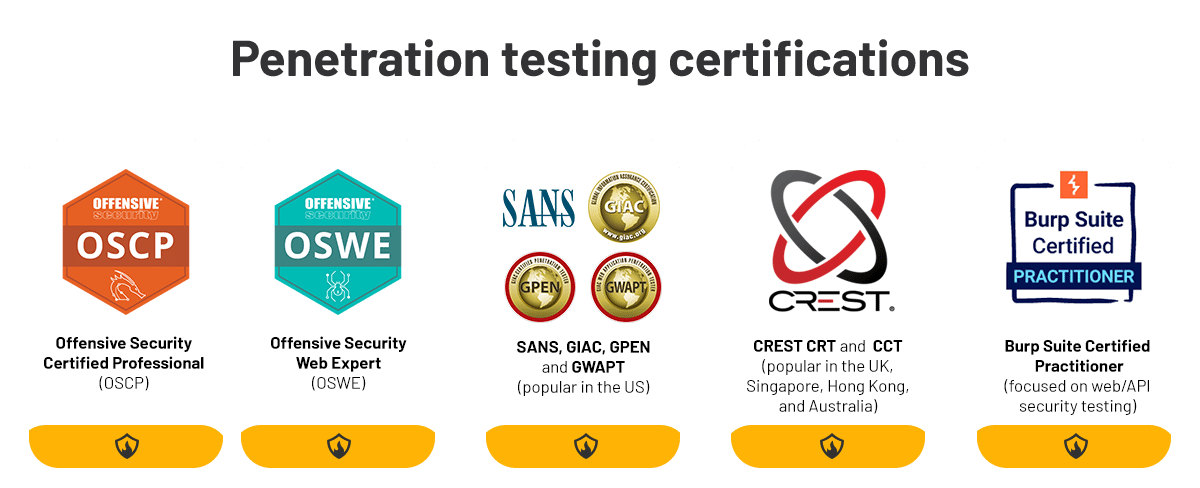
It’s crucial to underscore that the widely recognized Certified Ethical Hacker (CEH) certification frequently garners ridicule from seasoned industry practitioners. Often viewed as inferior quality, this certification lacks a hands-on component and is generally perceived as easy to attain.
Also, when evaluating a potential provider for penetration testing services, it’s imperative to confirm their adherence to best practices and established methodologies. Equally important, the provider should possess a ‘hacker mindset’ and creative problem-solving abilities that enable them to transcend conventional checklists.
Commonly adopted methodologies encompass PTES, OSSTMM, SANS CWE 25, NIST SP 800-115, or the OWASP Top 10. The latter specifically includes methodologies for pentesting web applications, mobile apps, APIs, IoT devices, AI, and large language models.
Ask for sample penetration test report and deliverables
Request the penetration test company to share examples of their pentest reports, attestation letters, and any other deliverables they might produce.
These documents are necessary to gauge the caliber of their findings and the extent of their testing, along with insights and recommendations for mitigating vulnerabilities. The quality of the reporting is paramount; after all, the report is the primary output you will obtain from the penetration test service you just hired.
For more information on what to look for in a penetration test report, refer to our blog post, which delved into the specifics of this topic.
Prefer boutique providers with a proven track record of security research
To summarize Google’s own recommendation for penetration testing provider selection, it is preferable to engage with companies specializing in cybersecurity consulting, with a primary focus on penetration testing services, as they often deliver superior results compared to those for whom pentesting is merely an offer in their service portfolio, such as IT Managed Service Providers (MSPs) and Big 4 accounting and audit firms.
According to Google’s security team, a dependable indicator of a high-quality penetration testing provider is their engagement in sharing knowledge through blogs detailing recent vulnerabilities and security research. Look for their contributions to the identification of ‘CVEs’ or vulnerabilities in standard software. Also, their presence in reputable industry conferences, such as BlackHat, DEFCON, CCC, etc., helps legitimize their expertise and experience.
Ask for case studies and client references
Ask for case studies or references from past clients. This will give you an idea of how they work, the type of organizations they are used to working with, what vulnerabilities they have found, and how effective their recommendations are.
Look for reviews or testimonials from previous clients to gain insight into the provider’s quality of service. Check if they have a reputation for being thorough, transparent, and timely in their assessments.
Conclusion
Selecting a penetration testing provider is not a decision to be taken lightly or based on superficial rankings. Remember, Top 10 lists often reflect SEO and digital marketing prowess more than actual competence in delivery penetration tests and other types of cybersecurity services.
Instead, your decision should be guided by carefully analyzing the provider’s services, industry experience, methodologies, and client feedback. By carefully selecting a provider, you can ensure that your organization’s security is in capable hands.
If your organization is looking to engage with a penetration testing company founded by experienced cybersecurity engineers, employs qualified staff that include CTF winners, has a proven track record of security research and doesn’t live off the hype and digital marketing, get in touch with our experts today.
FAQ
What are the best penetration testing companies?
No one knows. Best penetration companies lists are misleading, and tougher criteria for selecting the right pentest provider for your company should be applied.
What are the right criteria for selecting a reputable penetration testing provider?
Look for boutique pentesting providers specializing in cybersecurity services, sharing knowledge via technical blogs, identifying 0days and CVEs, presenting at industry conferences, and offering senior security consultants.








