With the increasing digitalization of modern healthcare and the fact patient health information is nowadays almost exclusively stored and transmitted in an electronic manner, safeguarding sensitive patient data has never been more crucial. This necessity has led to the implementation of data security and compliance measures, one of the most prominent being the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
This article is primarily dedicated to compliance officers and IT security managers working in the healthcare industry. Its purpose is to guide these professionals, who are tasked with maintaining the delicate balance between adhering to stringent HIPAA regulations and ensuring robust security measures in their organizations. The content is also relevant to healthcare administrators, third-party service providers such as penetration testing companies, and any other stakeholders interested in understanding the intersection of HIPAA Business Associate Agreements and cybersecurity practices, especially penetration testing, in the healthcare setting.
As we delve into the intersection of the HIPAA Business Associate Agreement (BAA) and its connection with penetration testing, we shed light on how these elements converge to protect healthcare information and why it’s essential for compliance officers and cybersecurity professionals to comprehend their interconnected roles.
What is a Business Associate Agreement?
A Business Associate Agreement (BAA) is a legally binding contract between a healthcare provider that is considered a Covered Entity and a third-party entity, known as a Business Associate, that requires access to Protected Health Information (PHI) to provide a service on behalf of the healthcare provider. The BAA is designed to protect PHI in accordance with HIPAA guidelines.
The agreement stipulates how PHI can be used and disclosed and mandates that the Business Associate will implement necessary safeguards to prevent unauthorized access. Furthermore, the BAA sets forth the obligation for the Business Associate to report any breaches of PHI to the healthcare provider, aiding in maintaining transparency and trust.
Under HIPAA, a Business Associate (BA) is any organization or person working in conjunction with a Covered Entity (CE) that handles or discloses Protected Health Information (PHI). Covered Entities typically include healthcare providers, health plans, and healthcare clearinghouses. BAAs obligate these Business Associates to protect PHI to the same degree as the Covered Entity itself. We will get into further details on clear examples of CEs and BAs in the next section.
Who needs to be compliant with HIPAA?
Compliance with HIPAA is required for two primary types of organizations within the U.S. healthcare sector: Covered Entities and Business Associates.
A Covered Entity under HIPAA refers to healthcare providers, health plans, and healthcare clearinghouses that transmit any health information in electronic form for transactions for which the Department of Health and Human Services (HHS) has adopted standards. In essence, any organization that electronically stores, processes, or transmits Protected Health Information (PHI) is considered a Covered Entity and is required to be HIPAA compliant.
Examples of Covered Entities include:
- Hospitals: These include general hospitals, psychiatric hospitals, and specialized hospitals, such as cardiac or orthopedic institutions.
- Doctors’ offices: These can range from small practices to large multi-specialty groups.
- Dental practices: These include all types of dental care providers.
- Pharmacies: This includes both independent pharmacies and those located within larger retail establishments.
- Health insurance companies: Any company providing health insurance coverage falls under this category.
- Healthcare clearinghouses: These entities process nonstandard health information they receive from another entity into a standard format or vice versa.
Each of these entities has a responsibility under HIPAA to protect the privacy and security of the PHI they handle, whether it’s being stored, processed, or transmitted.
Examples of Business Associates under HIPAA
A Business Associate under HIPAA is any third-party service provider that performs activities involving the use or disclosure of Protected Health Information (PHI) on behalf of a Covered Entity. These may include a variety of services across different sectors, with numerous IT-related providers often falling under this classification. Some examples of HIPAA Business Associates, including IT-related providers, are:
- IT service providers: These are companies or individuals providing IT support and services, including but not limited to network management, infrastructure support, and software maintenance. This is the category where most penetration testing service providers fit in.
- Cloud services and storage providers: These are companies offering cloud-based storage solutions where Protected Health Information might be stored or backed up. Practical examples are Amazon AWS, Microsoft 365 and Microsoft Azure. These providers have extensive materials about HIPAA compliance and do sign BAA when needed.
- Electronic Health Record (EHR) system providers: These companies provide EHR software that stores patient medical records electronically.
- Data analysis firms: These are companies that assist healthcare organizations in making sense of their data, often requiring access to PHI.
- Email encryption service providers: These services provide encryption for emails containing PHI, ensuring secure communication and data transfers of patient data that cannot be eavesdropped.
- Billing companies: These organizations manage billing and claims on behalf of healthcare providers, requiring access to PHI.
- Medical transcription services: These are services that transcribe medical voice recordings into written reports, often dealing with PHI in the process.
- Health Information Exchange (HIE) providers: These organizations enable the exchange of health information electronically across different healthcare systems.
- E-prescribing services: These are services that electronically send prescriptions from healthcare providers to pharmacies.
- Patient safety organizations (PSO): PSOs conduct analyses of patient safety events to improve patient outcomes and thus may have access to PHI.
- Telehealth platforms: Telehealth gained significant popularity during the COVID pandemic and will likely remain the norm for the foreseeable future. Many healthtech startups have been developing patient care videoconference platforms suitable for remote medical consultation, and most of them need to be in compliance. A prominent example is Zoom, which has a tier of its product that is HIPAA compliant.
Each of these service providers must sign a Business Associate Agreement with the healthcare organization, ensuring they are aware of their responsibilities to protect PHI under HIPAA regulations, including but not limited to HIPAA security rule and HIPAA privacy rule.
Looking for a pentest provider? Let us challenge your cyber defenses.
Talk to our experts for a custom quote
HIPAA BAA main elements
Creating a Business Associate Agreement (BAA) tailored to penetration testing services involves careful consideration of the specific role and responsibilities of the testing entity and the unique security concerns that the process introduces.
The primary aim of a BAA is to ensure that the Business Associate, in this case, the penetration testing company, understands their obligations under HIPAA in terms of protecting the privacy and security of Protected Health Information (PHI).
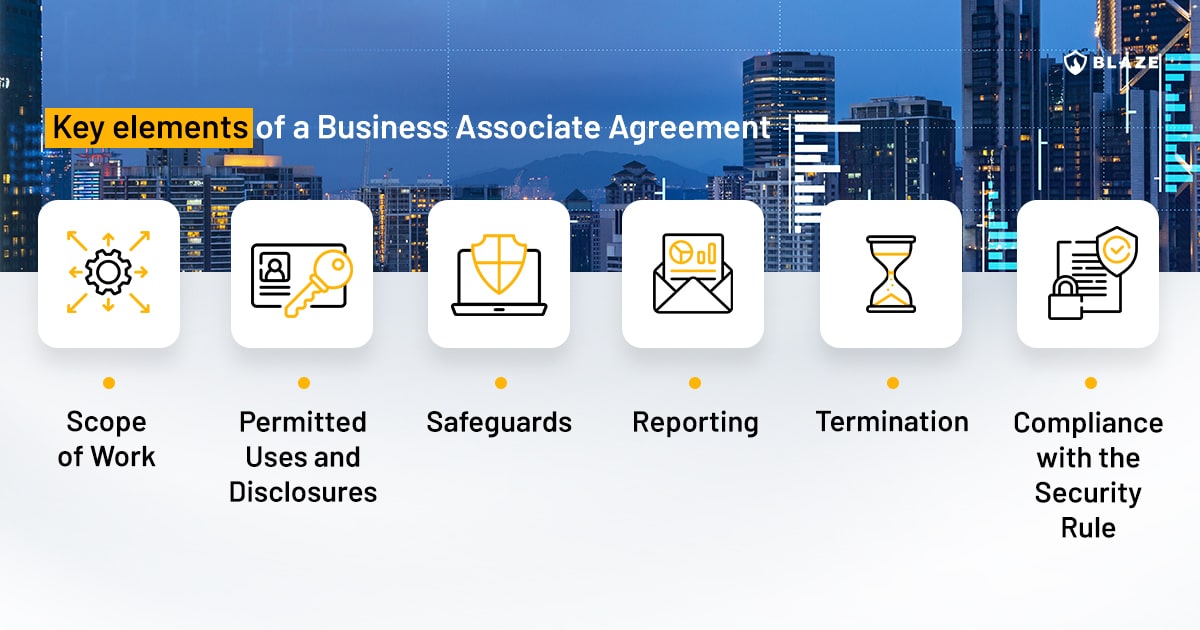
Key elements of a Business Associate Agreement
- Scope of Work: Clearly define the scope of the penetration testing to be conducted. This includes outlining the systems to be tested and the procedures that will be used.
- Permitted Uses and Disclosures: Specify how the penetration testing service may use and disclose PHI. As much as possible, penetration testing should be conducted on systems with dummy data to avoid direct contact with PHI.
- Safeguards: The agreement should require the penetration testing service to implement appropriate safeguards to prevent unauthorized use or disclosure of PHI.
- Reporting: Define the reporting obligations of the Business Associate in case of a security incident or breach involving PHI.
- Termination: Define the conditions under which the contract can be terminated.
- Compliance with the Security Rule: The BAA should state that the Business Associate will comply with the HIPAA Security Rule in the conduct of the penetration testing.
The U.S. Department of Health & Human Services provides sample BAA provisions and a model agreement to help organizations create their own agreements. However, these are general provisions and will need to be tailored to fit the unique requirements of a penetration testing service.
Almost all major cloud service providers and large email providers are HIPAA compliant and are able to sign a BAA. We have listed as reference links to the BAAs of Google, Microsoft and even Protonmail (especially for international reference, as they are based outside the US and yet able to sign a BAA).
Given the legal and regulatory implications of a BAA, it is highly recommended to have these documents reviewed by a legal team before they are signed. This ensures that the agreement adequately addresses all regulatory requirements and protects the interests of both parties.
Penetration testing in healthcare organizations
As healthcare systems continue to digitalize their operations, the threat landscape expands and brings a new set of risks and vulnerabilities. Ransomware attacks targeting clinics and hospitals led to severe data breaches and serious disruption of healthcare day-to-day operations, with the WannaCry attack on NHS being one of the most notorious ones, and more recently Clop ransomware gang attacks on institutions worldwide, including on healthcare sector in the US. Therefore, identifying risks and vulnerabilities early through penetration testing has become an important tool in any cybersecurity strategy, and healthcare is no exception.
Within the healthcare sector, these types of security evaluations often touch on various platforms that go beyond regular IT infrastructure, including Electronic Health Record (EHR) systems, imaging devices, patient monitoring systems, and communication protocols such as Health Level Seven International (HL7) and FHIR – a set of international standards for the transfer of clinical and administrative data between software applications used by various healthcare providers.
Understanding and assessing the potential threats and vulnerabilities in these areas is crucial. Let’s delve into some of them:
EHR systems
These systems contain a wealth of sensitive patient data and are often the prime target for cyber-attacks. A well-conducted penetration test will highlight vulnerabilities in these systems, allowing for timely mitigation.
In late 2022, USA Today reported that from 2010 to 2014, the first five years that data breach information was collected by US Health and Human Services, close to 50 million people had their medical data stolen or exposed. According to the same report, in the following five years, that number quadrupled and continued to rise during the COVID pandemic.
In January 2023, critical vulnerabilities in OpenEMR, a popular open-source solution used by more than 100,000 medical providers and serving over 200 million patients, were made public by SonarSource, and this is probably only the tip of the iceberg for EHR systems security.
Medical devices
Devices such as MRI machines, heart monitors, and insulin pumps are now connected to the Internet for better patient care and data analysis. For at least a decade, there has been public research on the security of medical devices and software (even some funded by government grants in Germany). In fact, there are even cybersecurity companies solely dedicated to this niche. Additionally, many medical device manufacturers have been establishing their own product security teams for security engineering and pentesting of their own medical devices.
The fact modern medical devices can (and certainly will) be connected makes them potential entry points for cyber attackers.
Healthcare-specific communication protocols (e.g., HL7 and FHIR)
These standards are used to exchange, integrate, share, and retrieve electronic health information. While they are indispensable in modern healthcare, they can also pose vulnerabilities if not properly secured.
There has not been a lot of public security research around HL7 and FHIR protocols, but the few materials out there highlight several weaknesses in these protocols and how especially HL7 is usually not locked-down enough in many healthcare IT environments.
In our experience, a lot of the techniques of API security testing, including the usage of regular pentesting tools and common vulnerabilities, are found in FHIR-powered applications.
Phishing and social engineering attacks
These attacks often aim to trick healthcare staff into revealing login credentials or other sensitive information. Phishing is also commonly the source of initial access by adversaries and legitimate red team operations. Penetration testing can simulate such attacks to assess staff awareness and the effectiveness of current security training.
A comprehensive penetration test in a healthcare environment should assess all of these potential weak points, providing a thorough evaluation of the organization’s cybersecurity defenses. Importantly, this has to be done while ensuring compliance with the regulations and stipulations of the HIPAA BAA, a topic we will explore in the following section.
The intersection of HIPAA BAA and penetration testing
When it comes to healthcare data security, HIPAA BAA and penetration testing intertwine significantly. Penetration testing uncovers system vulnerabilities that could potentially be exploited to gain unauthorized access to PHI. Ensuring these vulnerabilities are identified and addressed is not just about maintaining robust security; it’s a requirement under the HIPAA BAA.
As previously stated, HIPAA BAA mandates that Business Associates implement safeguards to prevent unauthorized access or disclosure of PHI. Penetration testing can serve as a vital part of these safeguards. A well-executed penetration test, followed by remediation of identified vulnerabilities, is evidence of an organization’s commitment to protecting PHI, thus fulfilling the requirements of HIPAA BAA.
On the other hand, a penetration testing services company is often classified as a Business Associate under HIPAA due to the nature of the services they provide.
To conduct their assessments, penetration testers attempt to breach the systems under the scope, and in some cases, this access may include contact with PHI. Even if the penetration testers don’t need direct access to PHI, they are interacting with the systems that handle this sensitive information, potentially impacting the security of that data. The mere possibility that they could come into contact with PHI during the course of their testing makes penetration testing firms a Business Associate under HIPAA.
Therefore, before the penetration testing service can begin its work, it must enter into a Business Associate Agreement (BAA) with the healthcare organization. The BAA stipulates the roles and responsibilities of the penetration testing company in safeguarding PHI in compliance with HIPAA requirements.
Best practices for ensuring HIPAA compliance during healthcare penetration testing
Aligning penetration testing needs with HIPAA rules and BAA requirements is no small task, but with the right strategy and a meticulous approach, it is entirely achievable. Here are some best practices to help ensure your penetration testing activities stay within the bounds of compliance:
Understand the regulations
Before initiating any penetration testing activities, ensure that your team has a thorough understanding of HIPAA regulations, especially those relating to the Business Associate Agreement. This knowledge will guide the planning and execution of your tests, ensuring compliance.
Engage a third-party auditor
Bringing in an independent, third-party auditor can provide an extra layer of assurance. These professionals can review your planned testing procedures and validate that they’re in line with HIPAA regulations.
Develop a clear testing plan
Detail your testing plan before starting, including what systems will be tested, what techniques will be used, and what data might be accessed. The plan should align with the BAA, ensuring PHI is appropriately safeguarded.
Maintain clear communication
Keep all relevant stakeholders informed about your penetration testing activities. This includes not only your internal team but also the Covered Entities you’re associated with. Transparency can help alleviate concerns and ensure everyone understands the purpose and extent of the testing.
Remediate promptly
Once vulnerabilities have been identified, swift remediation is crucial. The HIPAA BAA mandates that measures be in place to address potential threats to PHI, so any issues discovered during penetration testing should be addressed promptly.
Document everything: Keep detailed records of all penetration testing activities, including the planning phase, the testing itself, and the steps taken to remediate any identified vulnerabilities. This documentation will be invaluable if there’s ever a need to demonstrate your compliance with HIPAA regulations.
Review and update BAAs
Regularly review and update your Business Associate Agreements as needed to keep up with changes in your business practices or in the regulations themselves. This includes updating the BAA to reflect the use of penetration testing as a safeguarding measure for PHI.
Ensuring compliance with HIPAA BAA during penetration testing doesn’t have to be a daunting process. By following these best practices, you can both enhance your cybersecurity posture and maintain adherence to vital healthcare regulations. In the next section, we’ll explore some real-world examples where organizations have successfully managed the intersection of HIPAA BAA and penetration testing.
Infographic – Best practices HIPAA and pentesting

Conclusion
In the realm of healthcare, where sensitive patient data is routinely handled and exchanged, the necessity for stringent data security measures cannot be overstated. With the advancement of cyber threats, the need for robust security testing methods, such as penetration testing, has become more crucial than ever.
Penetration testing provides a realistic assessment of an organization’s security posture, revealing vulnerabilities that could be exploited by malicious actors. But, as we’ve discussed throughout this article, these tests must be conducted with careful consideration of HIPAA regulations, particularly the Business Associate Agreement.
Navigating the complex interplay between HIPAA BAA and penetration testing can be a daunting task, meaning that understanding and effectively managing the intersection of the HIPAA BAA and penetration testing is not without its challenges. It involves a delicate balancing act, maintaining the rigor of thorough testing while ensuring that the testing activities themselves don’t violate the regulations designed to protect the very data we’re trying to secure.
However, with a comprehensive understanding of the regulations, careful planning and execution of testing, swift and decisive remediation of identified vulnerabilities, and maintaining transparency and communication with all relevant stakeholders, healthcare organizations can both maintain their regulatory compliance, avoid HIPAA violations and significantly strengthen their defense against cyber threats.
FAQ
What is a Business Associate Agreement (BAA) under HIPAA?
A Business Associate Agreement (BAA) is a legal contract between a healthcare provider and a third-party service provider, known as a Business Associate. The agreement stipulates how Protected Health Information (PHI) can be used and disclosed, and mandates that the Business Associate will implement necessary safeguards to prevent unauthorized access to PHI.
Why do penetration testing services need a BAA?
Penetration testing services often require access to or interaction with systems that handle Protected Health Information (PHI). This potential access or interaction with PHI makes them a Business Associate under HIPAA, hence the requirement for a BAA.
How can a healthcare organization ensure HIPAA compliance during penetration testing?
A healthcare organization can ensure HIPAA compliance during penetration testing by carefully planning and conducting the tests, swiftly remediating identified vulnerabilities, maintaining open and transparent communication with all stakeholders, and ensuring the penetration testing company signs a Business Associate Agreement (BAA).








