As the need to bolster cyber resilience grows, organizations are increasingly turning to staff augmentation services to combat the recent 2023 figure of 4 million cyber workforce skills shortage.
This method integrates skilled professionals into existing teams, enhancing agility and expertise to address the rapidly growing threat landscape. Staff augmentation is more than a trend; it’s a crucial strategic adjustment in cybersecurity planning.
By utilizing external expertise and extended capabilities, companies significantly improve their IT security measures and increase resilience against cyberattacks. This article aims to dissect the rising importance of staff augmentation in cybersecurity. It emphasizes how cybersecurity staff augmentation plays a critical role in filling team gaps and transforming the digital security environment of modern organizations.
Understanding staff augmentation: more than just a buzzword?
In the boardroom of many modern businesses, “staff augmentation” is a term that resonates with increasing frequency. But what does it entail, and why is it becoming the go-to solution for many companies, including those in the cybersecurity domain?
At its core, staff augmentation is hiring specialized talent on a contract basis or augmenting your existing staff with external experts to meet specific business objectives. Think of it as a tactical approach to staffing, filling gaps as and when they emerge without the long-term commitment of traditional hiring.
What is cybersecurity staff augmentation?
Staff augmentation in the context of cybersecurity refers to the practice of temporarily hiring external IT security experts to enhance the capabilities of an existing cybersecurity team.
This approach differs from traditional hiring methods. While conventional recruitment focuses on long-term employment, staff augmentation is designed to address immediate and specific staffing requirements as needed. It allows organizations to rapidly scale up their cybersecurity workforce, especially when facing unforeseen challenges or tackling large-scale projects.
How does it differ from traditional hiring and managed services?
Unlike traditional hiring, which often involves a lengthy recruitment and onboarding process, staff augmentation is agile, addressing immediate needs without long-term commitments and the risks that come with traditional hiring. This model contrasts managed services, where an external partner is entrusted with complete control over certain IT functions. In staff augmentation, the external professionals work under the company’s management, integrating with the in-house team and adhering to its protocols and strategies.
The typical process of staff augmentation
- Identifying skill gaps: The process begins with a thorough assessment of the existing cybersecurity team’s capabilities, identifying areas where additional technical skills are needed. This might include specialized skills for risk assessments, security testing, advanced threat detection and monitoring, or cybersecurity response strategies.
- Selecting the right professionals: Once the specific needs are identified, the organization collaborates with staffing agencies, companies offering staff augmentation or directly contacts professionals who can fill these gaps. The focus is on finding experts with the right technical skills and experience to blend with the existing team seamlessly.
- Integration into the team: Once selected, augmented staff are integrated with the same resources as regular employees, such as company laptops and access to internal systems. They collaborate closely with in-house staff despite being external hires. The initial integration phase usually spans 4 to 6 weeks, varying with the organization’s complexity.
- Flexibility and scalability: One of the key advantages of this model is its flexibility. Organizations can scale their cybersecurity teams up or down based on current challenges and projects. This scalability ensures that the company always has access to the necessary expertise without the overhead of permanent hires.
- Duration of the engagement: Staff augmentation engagements can range from weeks to years, tailored to a project’s scope and organizational needs. The performance of augmented staff is regularly evaluated to align with business goals. At Blaze Information Security, we’ve worked in cybersecurity staff augmentation, particularly in application security, surpassing more than three years, showcasing its adaptability and long-term value.
Key reasons to opt for cybersecurity staff augmentation
Cybersecurity rapidly evolves, and teams always seek strategies to strengthen their defenses. Staff augmentation has emerged as a favored solution, and here’s why:
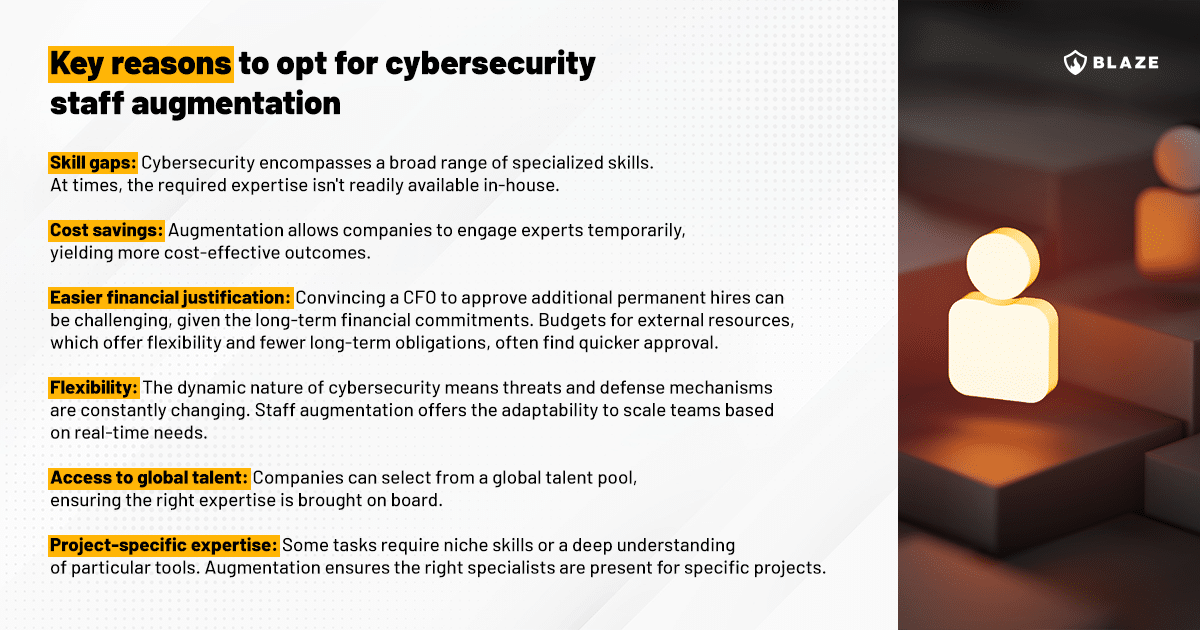
We feel that it’s important to get into more detail about some of the bullet points above to better highlight the reasons why an organization should opt for staff extension for cybersecurity teams:
Flexibility in operations
One of the primary benefits of staff augmentation is the flexibility it offers cybersecurity teams. This flexibility becomes particularly valuable when dealing with unpredictable landscapes. For instance, if a company needs to conduct application security activities such as threat modeling or penetration testing for a new software release, it can augment its team with experts specializing in this area for the project’s duration. This ensures the team can handle specific tasks without committing to long-term employment.
Access to specialized skills
The rapid evolution of cyber threats often requires specialized skills that may not be present in the current team. Staff augmentation allows organizations to access professionals with these niche skills, from more traditional ones, such as penetration testing, to security in machine learning and artificial intelligence experts, which are increasingly vital in advanced cyber strategies. Furthermore, organizations often need professionals with specific compliance certifications, especially when dealing with sensitive data.
Cost-effectiveness: A smart way to save money
Hiring full-time employees entails significant expenses, including salaries, benefits, and training costs, plus employment risks that come with labor laws in many jurisdictions. On top of that, many companies have a much easier time hiring third parties than making a business case for additional headcount. It offers a cost-effective alternative by enabling companies to hire experts only when needed. This approach saves organizations money by avoiding the fixed costs and risks associated with permanent hires and reducing the overheads related to recruitment and onboarding processes.
Scalability: Adapting to business needs
Another significant advantage of staff augmentation is scalability. Cybersecurity demands can fluctuate based on various factors like project phases, market trends, or emerging threats. Staff augmentation allows businesses to scale their team up or down quickly, aligning with current requirements without the complexities of restructuring permanent staff.
Addressing concerns about the staff augmentation model in cybersecurity
In this section, we aim to address concerns about staff augmentation in cybersecurity. We’ll discuss common concerns and provide reassurances on aspects such as commitment, security, and integration, demonstrating its effectiveness and versatility for organizations of all sizes. This discussion hopes to clarify how staff augmentation can be efficiently used to maximize value for an organization.
#1: Lack of commitment and consistency
- Concern: A common misconception is that staff augmentation, due to its temporary basis, leads to a lack of commitment and consistency in the workforce.
- Reassurance: Professionals hired through staff augmentation are highly motivated and dedicated. They bring a fresh perspective and are often quick to adapt, understanding that their reputation and future opportunities depend on their performance. Additionally, staffing agencies rigorously vet candidates, ensuring they possess the right skill set and a strong work ethic.
#2: Risk to confidential information
- Concern: There’s a concern that bringing external personnel might pose risks to sensitive information and cybersecurity integrity.
- Reassurance: Cybersecurity professionals, whether permanent or on a temporary basis, are bound by strict confidentiality agreements. Moreover, staff augmentation providers typically ensure that their analysts, consultants and other professionals comply with industry-standard security protocols. Organizations can also implement measures such as limited access to sensitive data and tailored onboarding processes for augmented staff to align them with internal security policies.
#3: Inadequate integration with existing teams
- Concern: Another concern is whether augmented staff can integrate effectively with the existing team and efficiently utilize the organization’s security tools and systems.
- Reassurance: Augmented staff often adapt to new environments and technologies. Their diverse experience with various security tools and systems in different settings equips them to integrate seamlessly. Furthermore, many staff augmentation services include a transition period to ensure smooth integration and alignment with the existing team’s workflow and culture.
#4: Staff augmentation is only for large enterprises
- Concern: Small and medium-sized businesses often believe that staff augmentation is a strategy only large enterprises can leverage effectively.
- Reassurance: Staff augmentation is highly scalable and customizable, making it suitable for organizations of all sizes. It allows smaller businesses to access the same level of expertise as larger firms without the need for significant investment in full-time hires. This levels the playing field, enabling smaller entities to bolster their cybersecurity defenses as effectively as their larger counterparts.
Potential challenges and pitfalls of staff augmentation for cybersecurity
As we saw throughout the article, staff augmentation offers several advantages for bolstering cyber defense, but it’s essential to understand its potential drawbacks to navigate them effectively.
Integration of external experts into existing company processes and culture can initially lead to communication issues. Knowledge retention post-tenure is another concern, as vital expertise may be lost without proper documentation or handover. Managing a mix of permanent and temporary staff also presents unique challenges, including consistency in deliverables and team dynamics. Furthermore, while cost-effective in the short term, over-reliance on this model could lead to higher long-term costs than developing in-house talent.
In summary, while staff augmentation is beneficial for cyber capabilities enhancement, organizations need to proactively address its challenges to fully leverage its advantages and minimize drawbacks.
Making the decision: is staff augmentation right for your cybersecurity team?
Staff extension has emerged as a compelling solution in the field of cybersecurity, but it isn’t a one-size-fits-all answer. Companies must weigh the benefits against the potential challenges to determine if this approach aligns with their objectives.
Firstly, organizations should assess their current and foreseeable IT security needs. Staff augmentation might be the logical choice if a consistent requirement for specialized expertise is not present in-house. On the other hand, if the need is sporadic, investing in training existing employees might be more prudent.
Budget considerations play a crucial role as well. While team augmentation can be cost-effective in the short term, will it remain so in the long run? Evaluating the financial implications of such a sustained approach might be worthwhile if the organization foresees a continuous dependency on external experts.
The organizational culture and team dynamics should also be factored in. If the current team thrives in a consistent environment with stable team members, introducing a frequent rotation of external professionals might disrupt the equilibrium.
Lastly, consider the managerial implications. Does the leadership have the bandwidth and expertise to effectively manage a blend of permanent and augmented staff? Seamless integration requires effort, and leaders should be prepared to guide this process.
It’s true staff augmentation offers numerous advantages, but it’s essential to approach the decision carefully. By considering the organization’s future IT security needs, culture, and objectives, leaders can determine if staff augmentation is the optimal strategy for their cybersecurity endeavors.
Conclusion
Staff augmentation equips cybersecurity teams with agility, adaptability, and expertise, which are essential for tackling today’s complex digital challenges. This model’s flexibility, skill access, cost-effectiveness, and scalability make it a strong choice for enhancing cybersecurity. Temporary staff with specific skills help companies quickly respond to industry changes and threats.
The article discussed concerns about commitment, confidentiality, and integration, as well as how they are addressed, alongside risks and challenges of staff augmentation. The article provides practical advice for implementing this model, aiding organizations in informed cybersecurity strategy decisions.
In conclusion, staff augmentation’s strategic and cost-effective approach is crucial for modern cybersecurity, particularly for a chief information security officer and their team. It ensures the right expertise is available when needed, evolving with the digital threat landscape. This model’s importance in cybersecurity will continue to grow, adapting to new challenges.
As the landscape of digital threats continues to expand, adapt and evolve, so will the significance and application of staff augmentation in cybersecurity.








